Mapping vulnerabilities to microservices with Snyk and OpsLevel
October 21, 2021
0 mins readJohn Laban is the Founder & CEO at OpsLevel. This blog post originally appeared on the OpsLevel blog.
Snyk is rapidly becoming the de facto standard for businesses that want to build continuous security into their software development processes. And with their developer-first tooling and best-in-class security intelligence, it’s no surprise.
From open source and containers to your application code and infrastructure as code, Snyk has solutions for finding and fixing security vulnerabilities across your stack. In any context, the insights surfaced by Snyk are valuable, whether critical vulnerabilities are found or not (we think the peace of mind resulting from no vulnerabilities detected is fantastic).
Microservice complexity
But a reoccurring challenge in a microservices context is connecting the dots so that the correct service owners can quickly review (and act on) Snyk scan results. Shipping quality, secure services is always the goal, but amidst so many operational concerns, vulnerabilities can fall through the cracks.
Plus, platform, security, or SRE teams that are focused on security posture and best practices often struggle to assess the overall state of their architecture. With thousands of scans and hundreds of services, how can they easily identify which services and teams are out of compliance and falling behind?
Using Snyk scan results and OpsLevel checks together overcomes these challenges.
Snyk + OpsLevel
Combining these two solutions unlocks many benefits:
It’s clear if a service isn’t being scanned as expected
Check writers (e.g. platform or SRE teams) have fine-grained controls for evaluating scan results
Automatic reporting on which services and teams are out of compliance
Service owners never lose sight of their scan results (and know how urgently they need to address any open vulnerabilities)
And, for all users, reviewing scan results becomes easier and more meaningful thanks to the complete context provided by OpsLevel’s service catalog.
Mapping vulns to services
In order to integrate Snyk with OpsLevel, documentation can be found here. It uses OpsLevel’s extensible Custom Event Check framework to receive JSON payloads. To send the scan result JSON payloads, we recommend using Snyk’s CLI tool. An example script can be found in docs from OpsLevel.
Scan results are mapped to services by setting up a check. OpsLevel provides Snyk-specific templates (e.g. No Critical Vulns or Less than 5 Low Vulns) that you can use as a starting point.
You can also write your own with jq — for payload parsing and pass/fail logic — and Markdown plus Liquid — for formatting and templating of result messages.
Education and prioritization
All checks in OpsLevel come with a natural place for check writers to explicitly educate service owners on what steps to take in order to pass a check, as well as explain why a particular check matters in the first place.
Incorporating Snyk scan results into OpsLevel’s Service Maturity model also makes prioritization clear for service owners. In addition to using the result message and notes sections of a check to give complete context, check writers can use the filters and levels in OpsLevel’s rubric to create a targeted, graduated approach to shipping more secure and mature services.
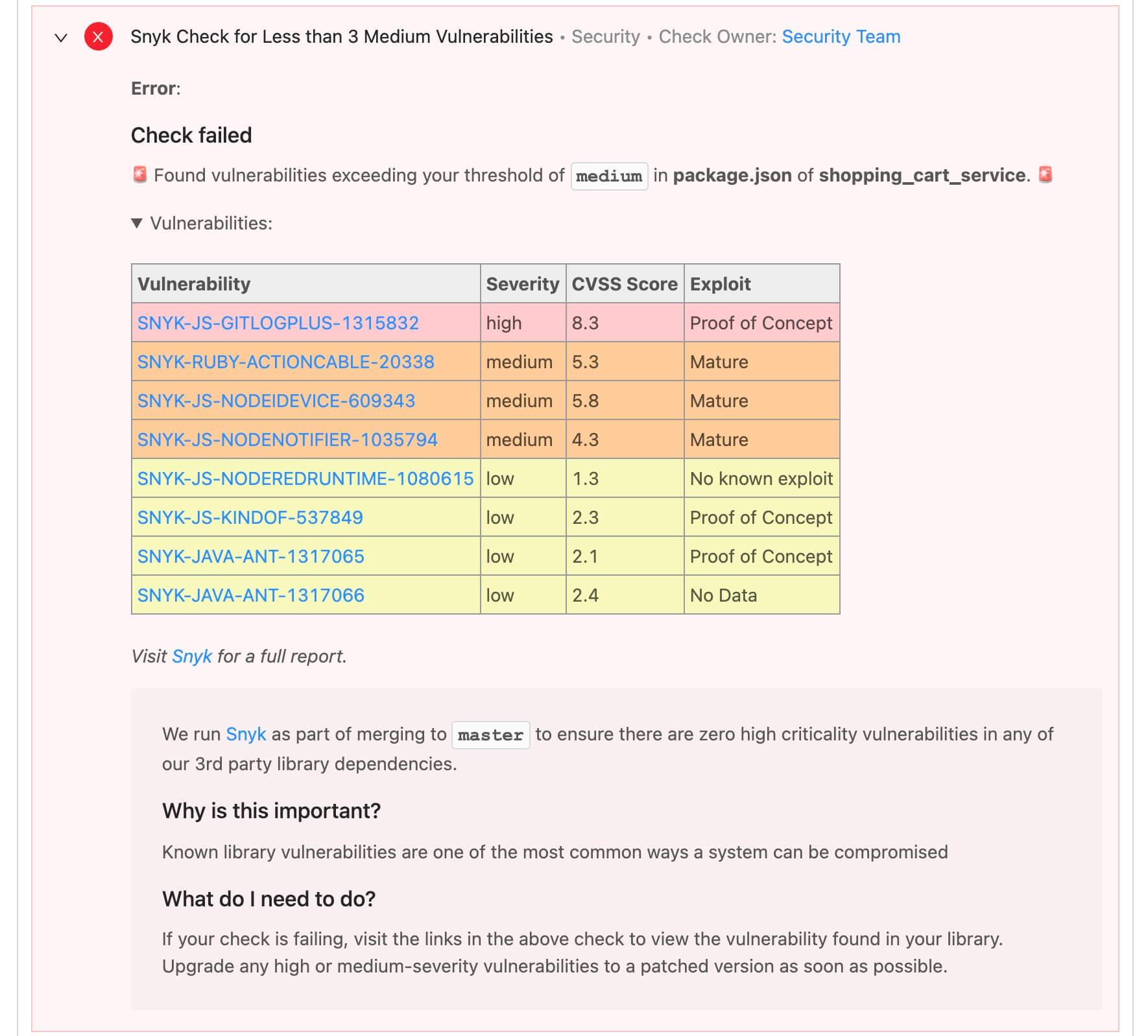
A service owner's view of their scan results, with more than 3 medium vulnerabilities
For example, the presence of high vulnerabilities in scan results may be a show-stopper for any customer-facing services, but much less concerning for internal-only services. Distinctions like this are quickly encoded in OpsLevel and then easily reviewed by service owners, so their time is always spent on the right operational or security tasks.
Automated reporting
Individual check results guide service owners to the appropriate next steps for improving and securing their services. In aggregate, they can inform key stakeholders–platform teams or engineering management–on their organization’s current security posture.
Answering questions like which part of my application is most at risk? or what team is falling behind? is straightforward with OpsLevel’s check reports.
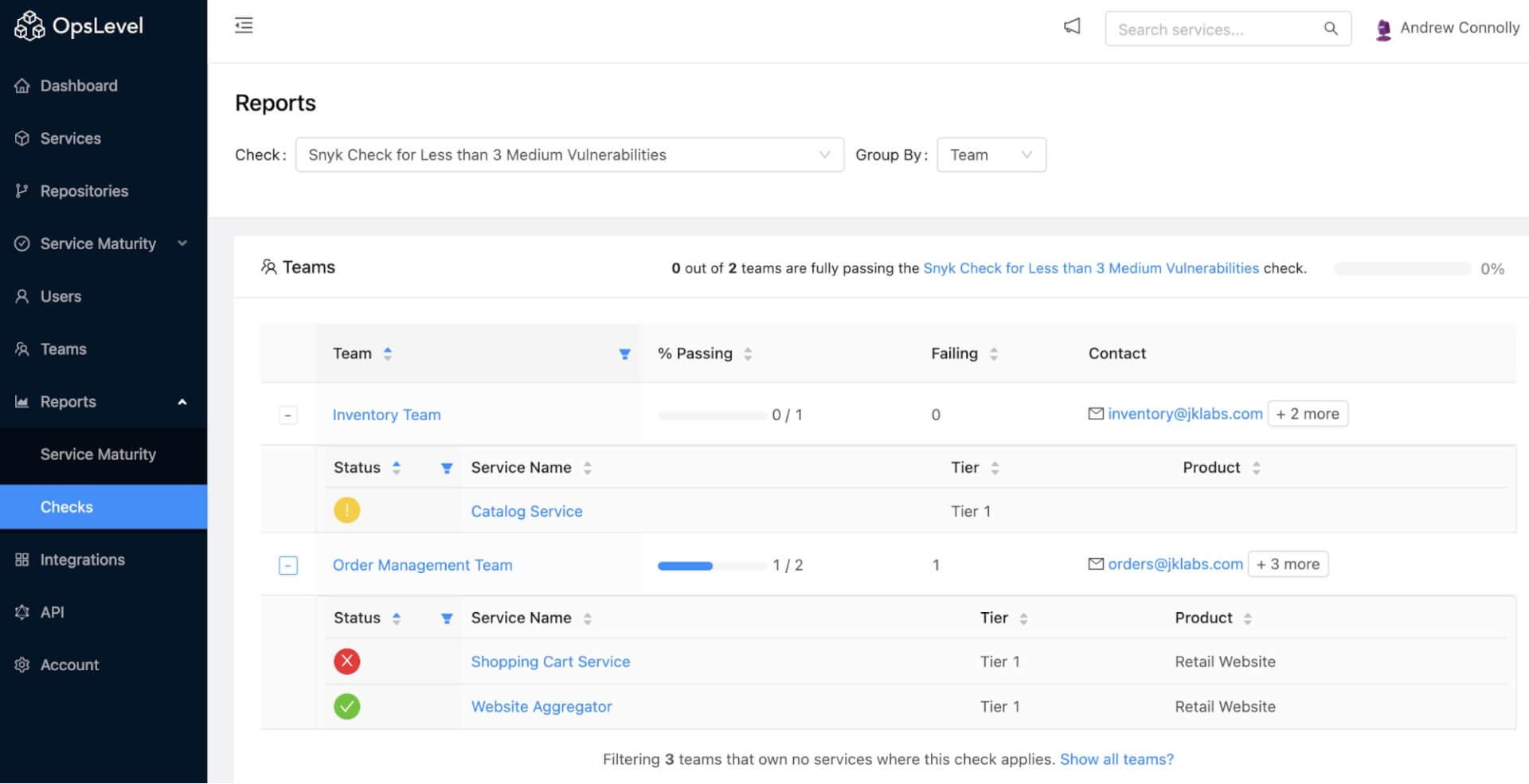
A top down view of all the relevant services' status for this check: 1 passing, 1 failing, and 1 with no scan results.
Try OpsLevel + Snyk
If you’re already using Snyk, you’re on the right track towards shipping more secure services. Accelerate that journey by embedding your scan results into a comprehensive service catalog. For more information on OpsLevel or to request a demo, click here. If you haven’t tried Snyk, you can start using it for free.
Get started in capture the flag
Learn how to solve capture the flag challenges by watching our virtual 101 workshop on demand.





















