Case study: Python RCE vulnerability in Celery
Calum Hutton
15. Februar 2022
0 Min. LesezeitOverview
I conducted research based upon existing Python vulnerabilities and identified a common software pattern between them. By utilizing the power of our in-house static analysis engine, which also drives Snyk Code, our static application security testing (SAST) product, I was able to create custom rules and search across a large dataset of open source code, to identify other projects using the same pattern. This led to the discovery of a stored command injection vulnerability in Celery. SAST tools such as Snyk Code allow developers to identify bugs in their software purely by analyzing static source code and identifying patterns of inefficient or dangerous code.
Motivation
I was motivated to conduct this research project based on personal experience and vulnerability research in open source Python projects (CVE-2017-11610 and CVE-2021-32807). My hypothesis was that object traversal (the ability to acquire a reference to an arbitrary object attribute from another object) is a common feature in Python. I wanted to investigate and prove this hypothesis to identify the prevalence of this pattern in the wider Python ecosystem, and particularly identify instances of arbitrary (or nearly-arbitrary) object traversal that could lead to security vulnerabilities.
Context
In Python, almost every element of the language is an object, with its own explicit and inherited attributes and methods (including class instances and modules). Because of this, Python applications may offer a method of traversing an object namespace in order to obtain a reference to an object's attributes, or sub-attributes. To achieve this, a recursive attribute lookup may be performed.
The following simplified example code demonstrates how object namespaces can be traversed (in Python 3), by importing an innocuous module (random), it is possible to acquire a reference to a dangerous function (os.system) by using getattr to acquire a reference to the imported os (aliased as _os) module:
If a Python application were to expose object traversal functionality to the user in a way that they can manipulate the requested object namespace path or attribute, it could lead to arbitrary (or nearly-arbitrary) object traversal, leading to several potential issues:
The most likely impact of exposed object traversal functionality is broken access controls or information disclosure, if a user can acquire a reference to a private method or attribute such as
obj._private_method() or obj._secret.Remote code execution (RCE) is also possible, if an arbitrary method such as
os.system()is acquired and called with user supplied arguments. This is not as likely as the user needs to acquire a reference to the method, and be able to pass arguments to it.
To summarize, an attacker who can control or manipulate object traversal within a Python application could potentially access a given module or class instance's attributes and sub-attributes, utilizing their functionality in an unrestricted or unexpected way.
The vulnerable pattern
The pattern identified as relevant to the above CVEs is that of a recursive attribute lookup, usually based upon a Python dotted path. The path is split and iterated over in a loop, with the current element of the path used to acquire a reference on the context using getattr(). The reference from the previous getattr() call is then used as the context for the next and the process repeats until there are no elements of the path left. The following script demonstrates this:
The dot-separated path is split into two strings (_os and system). For the first iteration of the loop, the cls variable is a reference to the random module, so the getattr() looks up the _os attribute of the random module, which is the os module. The context of the getattr() then becomes the os module, and in the next iteration, the system attribute of the os module is retrieved, aka os.system().
Case study (Celery - CVE-2021-23727)
Using the Snyk Code engine, I developed rules to identify the same pattern in other open-source Python code. One of the rule/pattern matches was inside Celery, an open-source asynchronous task queue which is based on distributed message passing. The rule matched the exception_to_python function within the celery.backends.base.Backend class:
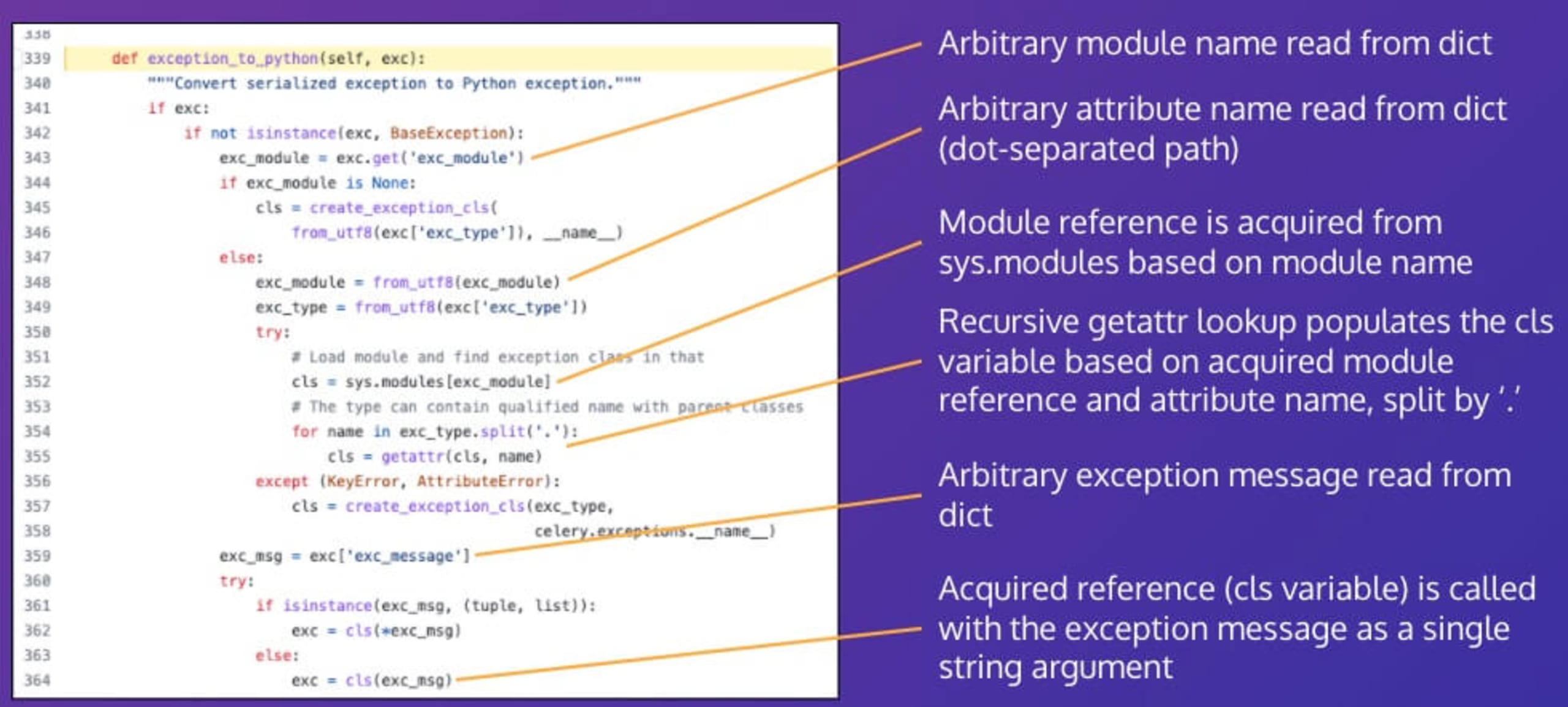
The recursive getattr pattern can be seen inside the function, on line 354. Through further review of the function and how it was used within Celery it became clear that the entire exc dict object was originating from JSON data stored in a Celery backend. As such, it could potentially be controlled or manipulated by a user with access to the backend server, and hence all fields of the dict should be considered potentially tainted.
Further analysis of the code identified that an arbitrary module reference is accessed, based on a property of the exc dict object (line 352). The recursive attribute pattern is then used to lookup an arbitrary attribute of the module. The acquired attribute reference is then called with a single string argument, also taken from the exc dict object (line 364).
Considering that the entire exc dict object could potentially be tainted, and no validation is in place to prevent arbitrary modules and attributes being accessed, this code was identified as likely vulnerable to stored command injection.
I proved this hypothesis using the Python console, by importing the relevant classes and crafting a malicious dict to simulate an attacker creating a malicious JSON blob within the database of a Celery backend:
First, I create a Python dict, to be passed to the vulnerable function. This dict contains properties that control the module to be accessed (exc_module), what attribute of the module to acquire a reference to (exc_type), and finally what argument to pass into the acquired method (exc_message).
The next few lines import the vulnerable code from Celery into the Python console, and initialize the Backend class with a Celery object.
Finally the vulnerability is triggered when the dict is passed into vulnerable method exception_to_python.
The last line in the code snippet above is the output from the id command, proving that the crafted dict was deserialized and successfully triggered arbitrary command injection within the Backend class.
For a system utilizing Celery, an attacker exploiting this vulnerability could lead to command injection within the producer, potentially allowing for total system takeover. If the Celery backend is remote, this vulnerability could also allow attackers who have gained access to the Celery backend to move laterally within an organization's network and gain a foothold on additional network infrastructure.
Remediation
This issue was responsibly disclosed to Celery and was fixed in version 5.2.2 of the software by adding validation of the targeted module and checking the types of resolved attributes before calling arbitrary functions with potentially tainted input. In general, when deserializing objects, care should always be taken around any potentially tainted data, even if it originates from a remote data source or database. If possible, the types of objects should be checked and validated before deserialization, or at least before calling a method or property of the deserialized object.
Finding this command injection vulnerability in Celery and performing the required tainted data analysis was simplified with Snyk Code. Our revolutionary SAST tool is a developer-friendly, fast, and accurate alternative to traditional security tools. IDE plugins integrate real time testing into existing workflows, empowering developers to find and fix vulnerabilities in as little as 5 minutes. Start a free trial today and see how Snyk Code makes secure development simple.
Beginnen Sie mit Capture the Flag
Lernen Sie, wie Sie Capture the Flag-Herausforderungen lösen, indem Sie sich unseren virtuellen 101-Workshop auf Abruf ansehen.
References
Celery (CVE-2021-23727): https://security.snyk.io/vuln/SNYK-PYTHON-CELERY-2314953
