6 steps for scaling risk-based AppSec programs
13. Oktober 2023
0 Min. LesezeitScaling a risk-based AppSec program involves adapting your security practices to accommodate the growth and evolving needs of your business, while effectively managing and mitigating security risks.
No matter the maturity level or organization type, scaling an AppSec program that manages both security risks and business growth means incorporating existing tools and combining them with new solutions, services, and context to form a lean, mean security machine that leaves no stone unturned and no room for doubt. Building this kind of a security program isn’t something that happens overnight — it’s a step by step process that evolves alongside dynamic business processes and as the organization scales.
Here are 6 steps to help you as you scale your risk-based AppSec program, as well as a handy cheat sheet for quick reference:

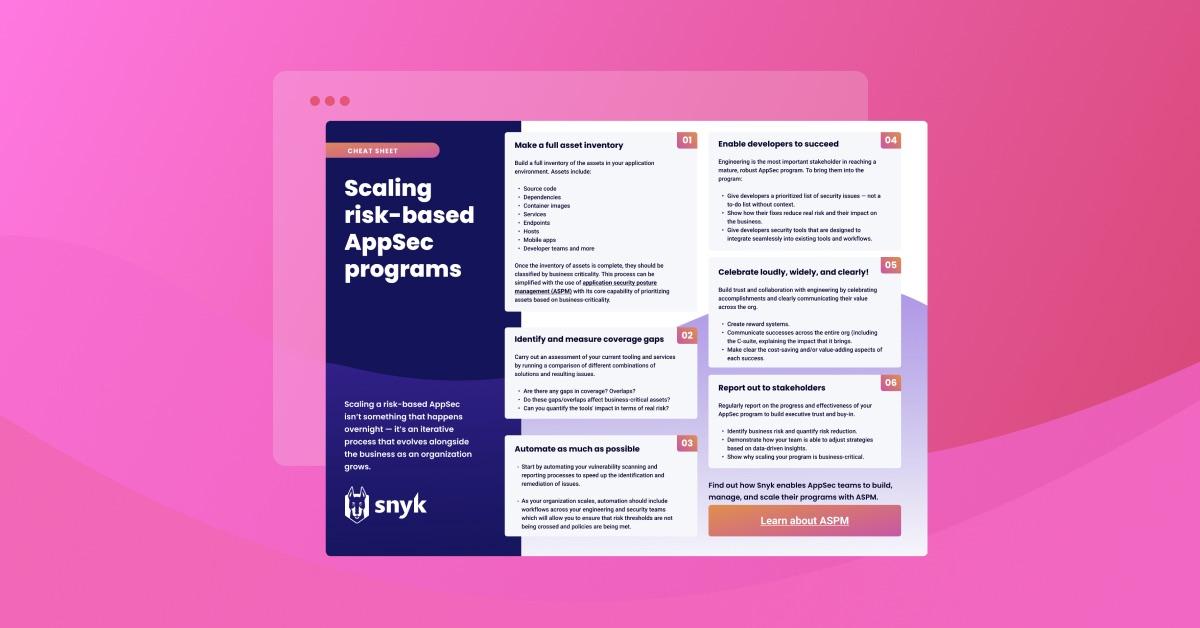
1. Make a full asset inventory
In order to build a risk-based AppSec program, you need to know where the risk lives! The first step is to build a full inventory of the assets in your application environment. We define assets as all the different components involved in building, deploying, and running the application — source code, dependencies, container images, services, endpoints, hosts, mobile apps, developer teams, and more.
Once the inventory of assets is complete, they should be classified by business criticality. We recognize that this is not a small, overnight effort and encourage you to learn more about application security posture management (ASPM) and its core capability to prioritize assets based on business-criticality.
For those organizations that do have at least partial visibility (or are unsure if they have a complete inventory), continuing to rely on a fragmented view of your environment is an inherent business risk. Without a comprehensive inventory of your assets, your organization will not be able to properly identify risk and effectively govern security.
2. Identify and measure coverage gaps
Improving efficiency in instrumenting tools and services is an important foundational step to a scalable security program. Measuring, optimizing, and maximizing the use of thoroughly evaluated tools and services will lead enterprise organizations to develop a healthy application security posture.
Carry out an assessment of your current tooling and services by running a comparison of different combinations of solutions and resulting issues. Are there any gaps in coverage? Overlaps? Do these gaps or overlaps affect business-critical assets? Can you quantify the tools' impact in terms of real risk?
3. Automate as much as possible
You may still be getting by with spreadsheets, but your organization must reach its maturity scale with an automated process of day-to-day task management. If you haven’t established an automated workflow to operate security at scale across all businesses, now it is business-critical.
Automating vulnerability scanning and reporting to speed up the identification and remediation of issues is an important start, but as your organization scales automation should, include workflows across your engineering and security teams which will allow you to ensure that risk thresholds are not being crossed and policies are being met. Remember, you can't accidentally forget to do something if it happens automatically.
4. Enable developers to succeed
Engineering is the most important stakeholder in reaching a mature, robust AppSec program. Without their support, achieving maximum efficiency will remain a pipe dream.
AppSec must guide developers to make good decisions up-front. For example, developers should be given a prioritized list of security issues and be shown how their fixes reduce real risk — not a to-do list without context. Additionally, developers should be given security tools that are designed to integrate seamlessly into existing tools and workflows.
5. Celebrate loudly, widely, and clearly!
One way to build trust and collaboration with engineering is to make sure to celebrate accomplishments and clearly communicate their value across the org. Create a reward system, shout the compliments out far and wide, and be specific with what the accomplishment means to the org (ex: "This early fix saved us $5M of future debt.").
If the organization sees how fixing vulnerabilities has a real impact on the business, it will be easy for them to get on board. If possible, try to show the value of an AppSec program in terms of profit and not just savings. For example, added security can increase compliance, increasing your total addressable market (TAM).
And remember, organizational values start at the top. If security successes are celebrated in the C-suite as loudly as they are on the engineering floor, the whole organization will see security as a value-add, not just a box to check.
6. Report out to stakeholders
Properly scaling an AppSec program is going to require resources — and resources require approval. Regularly report on the progress and effectiveness of your AppSec program to stakeholders in order to build executive trust and buy-in. Show that you can both identify business risk and quantify risk reduction. Demonstrate how your team is able to adjust strategies based on data-driven insights and why scaling your program is business-critical.
Start scaling
Scaling a risk-based AppSec program is an ongoing process that requires adaptability, dedication, and a commitment to making the job of devs as easy as possible. Using the above recommended steps, take time in the near future to evaluate your current AppSec processes to see where improvements can be made in any of those six focus areas. Then be sure to regularly review and update your strategy to address new challenges and opportunities for improvement.
Secure what matters most to your business
Find out how Snyk enables AppSec teams to build, manage and scale a modern AppSec program with Snyk AppRisk ASPM