Security breach leaks the personal data of all 6.5 million Israeli voters
February 12, 2020
0 mins readOn the 10th of February, 2020 a security issue exposed the personal data of all 6,453,254 Israeli voters. The leak exposed personally identifiable information (PII) including full names, ID numbers, gender, addresses, and voting information.
Ran Bar Zik, an information security journalist and software engineer at Verizon Media group mentioned that this is the most severe and unprecedented security issue he had uncovered to date.
In this article, Ran takes a closer look at the incident and its implications. Find the original post in Hebrew here.
I have been a programmer for many years. In my career, I have seen many things but this kind of security breach is something I have not seen before. No mechanism was able to stop me from gaining unauthorized access — even though I was connecting from a non-Israeli source address.
On February 7th, 2020 I received an anonymous tip through the “leak inbox” of the Israeli CyberCyber podcast. In a message, written in English, I received proof of concept and guidance to check Elector's website — a site that has an elaborate election management system used by the Likud party (Israeli right-wing party) for campaign management. The message included concerns and warnings about this system. The Elector website contains the complete PII of all Israeli voters.
Attorney Shachar Ben Meir has filed a special petition with the Election Commission to demand that the elections are canceled due to privacy concerns. RaFa Refaella Goichman published an interesting article that recounts the concerns of privacy activists and others over a system that contains the personal details of us all.
Elector and its editorial staff reassured the public that the website security is very tight. Here is a quote from the CEO of the company regarding the website’s safety:
"The system was written by senior information security professionals and software system developers. We did not compromise on building a system that would just deliver the goods — we wanted a system that would work well and secure the most rigorous standards"
Well, were these rigorous, according to the company, security standards enough? Within a minute, I was able to view every voter’s information on the website.
What did it take to "hack" this protected and guarded system? Pay close attention:
1. Navigate to the website and right-click "View page source" from the browser.
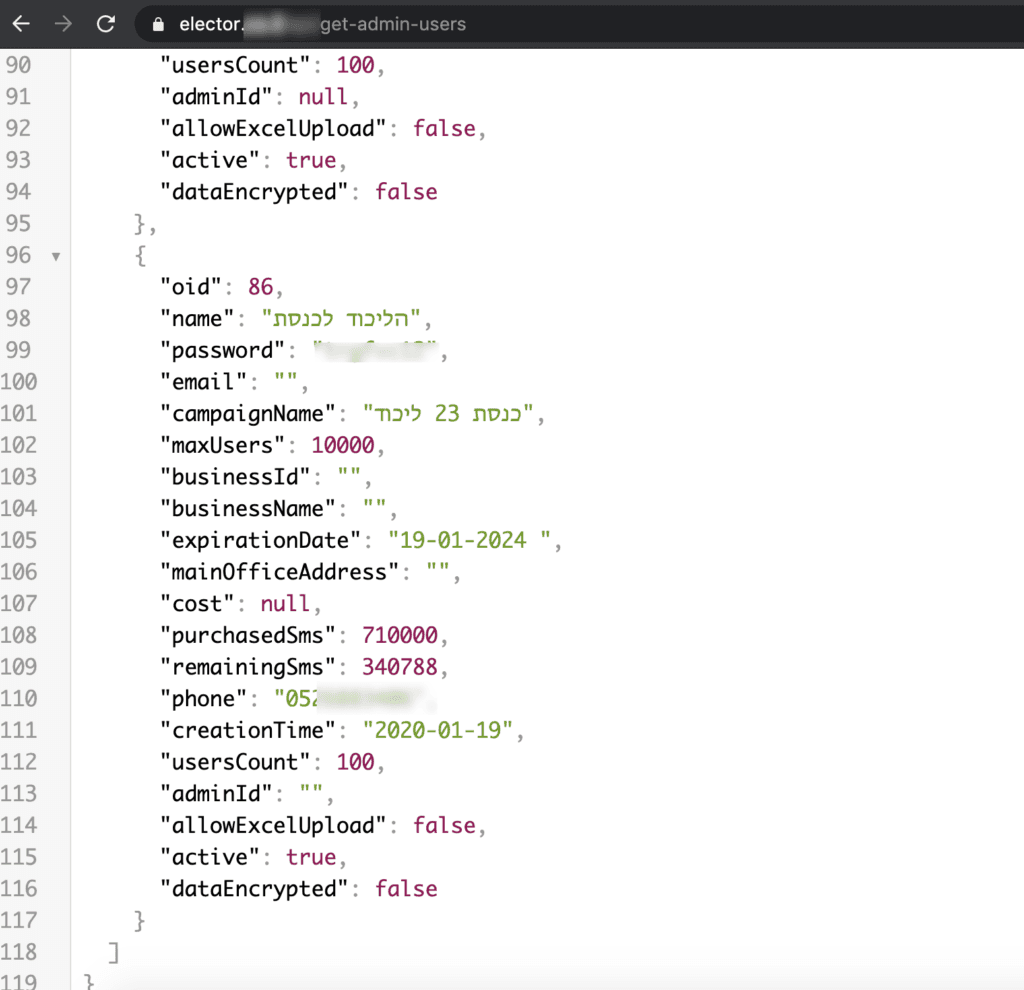
2. Find this API call: /get-admin-users which appears at the very beginning of the code:

3. This gives out a JSON response with the following details, which include plaintext passwords that allow log-in to the system:
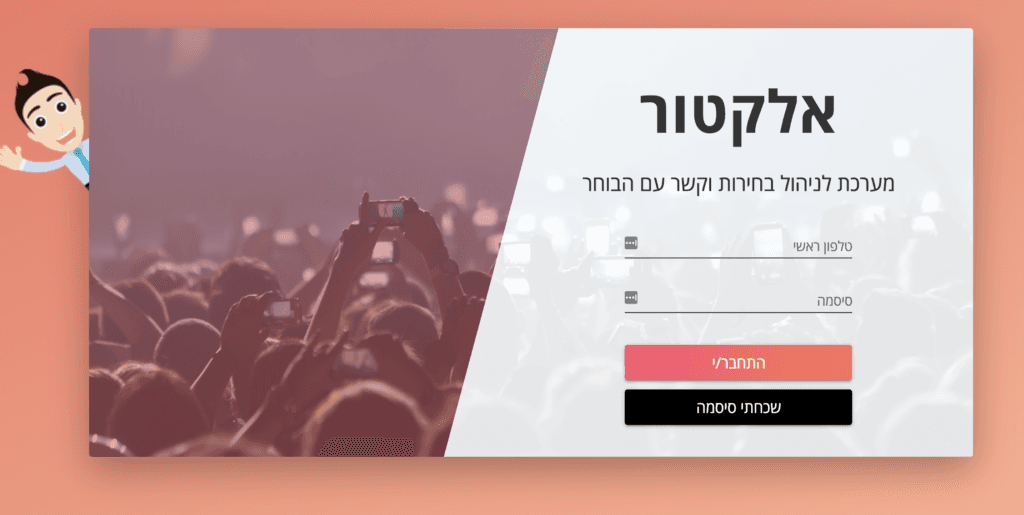
4. Sign in to the Elector website using the above details:
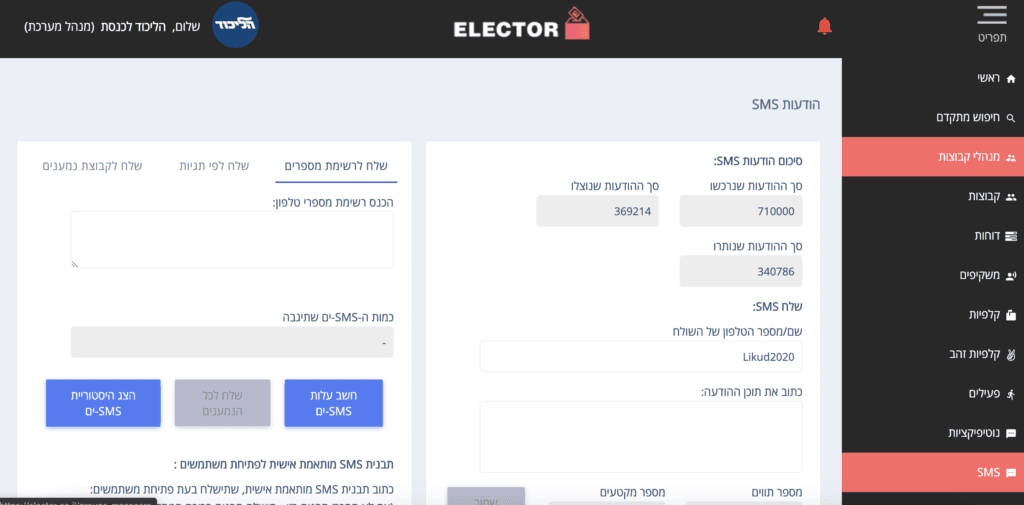
5. View the list of managers and their passwords:
All the data is here; that's it.
Whoever was to “hack” this website would’ve gained full access to all system information, and complete and unrestricted access to the full list of Israeli voters and their personal data.
Note that the duration of my stay on the site was limited. I am bound by the Computer Act 1995 and have been very careful not to cause damage but to enter the site for the sole purpose of understanding the damage.
Civic virtue, and nothing else, was my only motivation. As soon as I realized the extent of this security breach, I logged out and immediately reported the issue to the relevant cybersecurity authorities of Israel which replied promptly.
If you're interested in learning more about this incident, follow Ran Bar Zik’s coverage of the story here:





















