SocketSleuth: Improving security testing for WebSocket applications
2023年9月6日
0 分で読めますToday, we are proud to announce the beta version of SocketSleuth, our new Burp Suite extension for performing security testing against WebSocket-based applications. SocketSleuth was created out of our security research group to aid in our security research against applications that leverage WebSockets for communication.
While Burp Suite from Portswigger is the gold standard proxy for pentesting applications, its current support for WebSockets is rather limited and its capabilities are not on level with its suite of features for testing traditional HTTP-based applications.
This is particularly the case regarding some of Burp’s automation features such as the amazing Intruder, which allows researchers to automate the sending of requests with payload insertion points, a powerful feature that enables request attributes to be manipulated based on the Intruder configuration.
If you’ve ever been on an engagement and faced a WebSocket-backed application, you might have opened up the BApp store (Burp’s built-in extension store) and been surprised to find no extensions that enhance WebSocket testing capabilities. Well, starting from the Montoya API released on October 27, 2022, this is no longer the case. The Montoya API now enables developers to hook into the WebSocket functionality of Burp Suite, enabling the community for the first time to build tools for testing WebSockets in our favorite proxy.
SocketSleuth Features
For the initial beta version of our extension, we have kept the feature set simple and will gather user feedback to help us add capabilities that users will find most useful. However, the initial features are powerful and should significantly improve the typical workflow for testing WebSocket-based applications. Below, you can find a summary of the key features included in the initial beta.
WebSocket Connection Manager
Viewing all the different WebSocket connections, their connection handshake requests, and messages in Burp Suite can be a little overwhelming. The SocketSleuth WebSocket history tab makes its easier to see this information and focus on the relevant WebSockets for a given task.
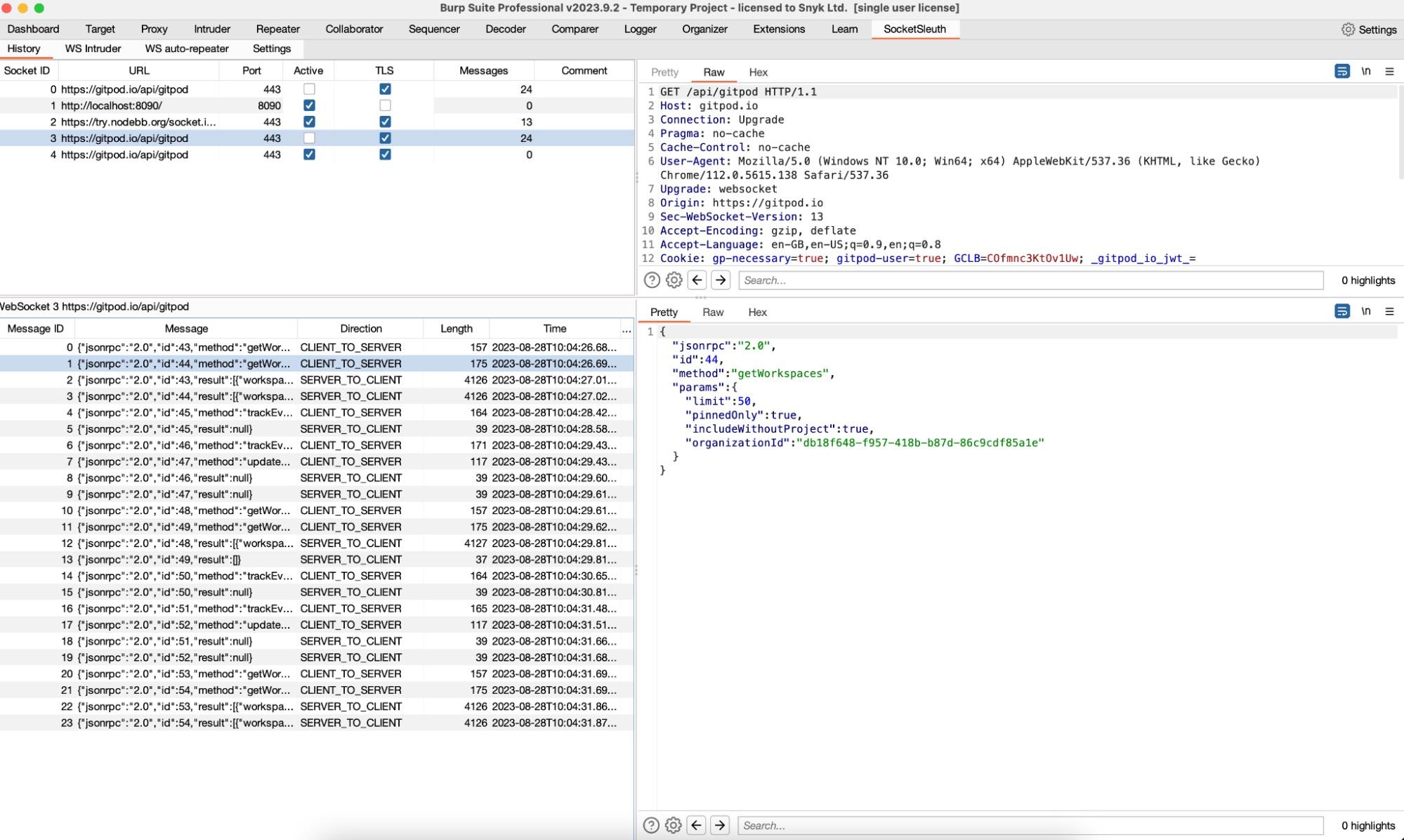
In the top left panel, we have the list of WebSocket handshakes and some attributes about the connection, such as details about the host, the number of messages transmitted, and whether the connection is still alive. Selecting a given WebSocket will show the associated connection handshake request in the top right panel, and its messages in the bottom left. Selecting a given message will load its contents into the bottom right panel, and finally, the right-click context menu allows additional actions to be performed such as sending a specific message to additional tools in SocketSleuth.
WebSocket message interception with match & replace
A simple but powerful feature we missed was the ability to set interception and match & replace rules for WebSocket messages. It can be very useful to automatically replace a given value in a message and SocketSleuth allows this to be performed on WebSocket messages.
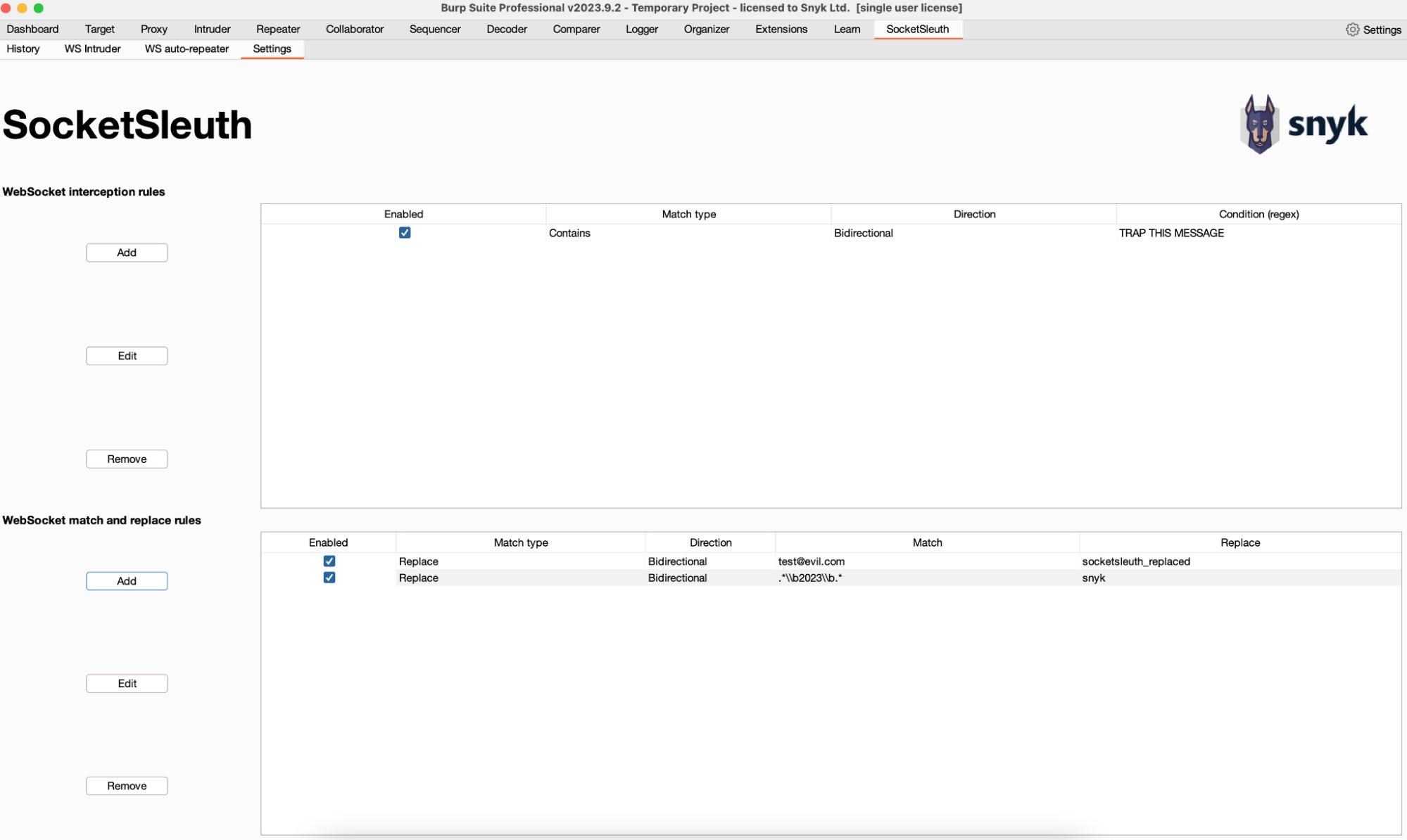
Text strings and regular expressions can be used to intercept and replace the contents of messages.
WebSocket AutoRepeater
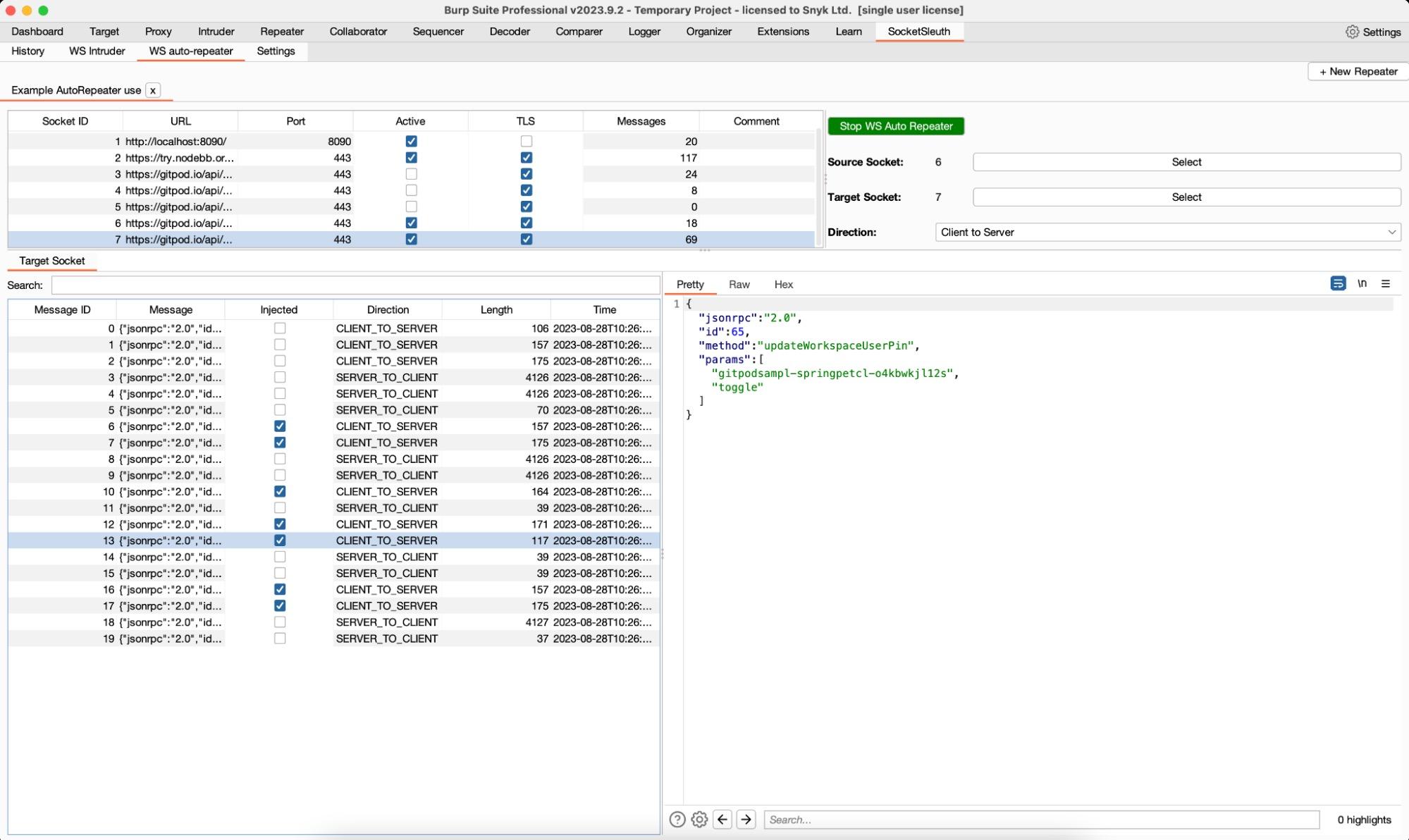
Burp extensions like Autorize and AutoRepeater have made automated testing for authorization issues far easier. The WebSocket AutoRepeater function takes its inspiration from these BApps and allows a source and destination socket and message direction to be specified.
When the AutoRepeater is running, it will take all messages from the source socket, and if the direction matches the configuration, automatically replay the message in the destination socket.
When AutoRepeater is configured with two WebSockets associated with two different privilege levels, it can provide an easy way to perform authorization testing for components using WebSockets.
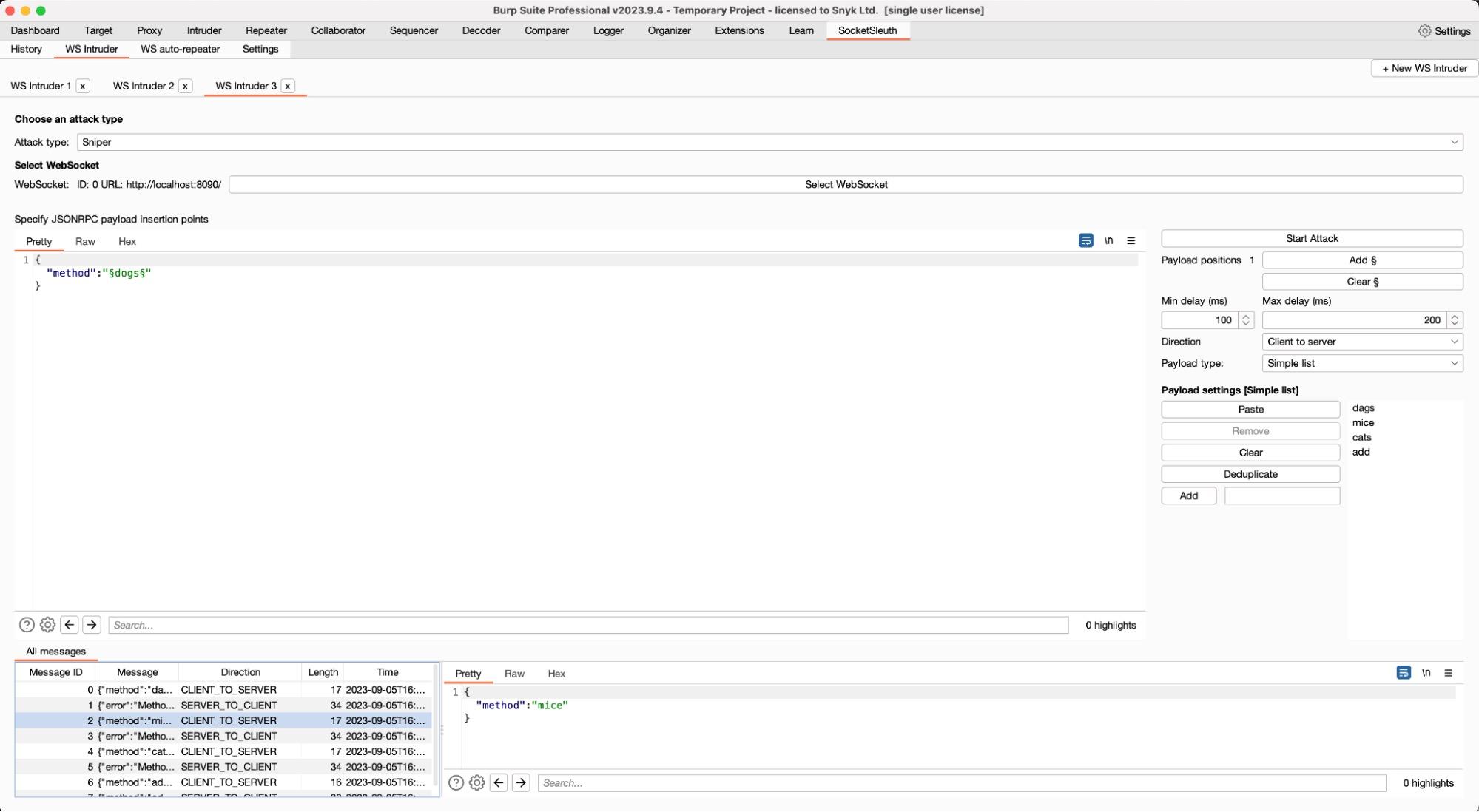
WebSocket Intruder
The final feature included in the beta release is the WebSocket Intruder. Like its HTTP request counterpart, it aims to provide some automation capabilities that can be used in a variety of scenarios such as enumerating hidden methods, brute forcing parameters, or anything else that is required. For the initial launch, two intruder attack types are present: JSON RPC method discovery and Sniper.
The first can be used to enumerate JSON RPC methods from JSON RPC APIs. The second aims to provide similar capabilities as the traditional intruder Sniper to place automation payloads into different positions within the message. Currently, only two payload types for the Sniper are supported — Simple List and Numeric — however, this should be sufficient for most use cases.
Start SocketSleuthing
We hope that SocketSleuth will provide utility to anyone undertaking penetration tests against applications leveraging WebSockets.
The Burp Suite WebSocket extension is still in its early stages but we have found it incredibly useful during our recent research projects and hope the community finds this a useful addition to the Burp Suite ecosystem. Additional features and bug fixes will be implemented soon, and we are excited to reveal some of the upcoming planned additions in the near future.
SocketSleuth is in the process of submission for the official BApp store, but you can use it right now through Snyk’s GitHub repository at https://github.com/snyk/socketsleuth/.
We welcome any feedback and suggestions, and hope SocketSleuth can be used to improve security testing of WebSocket-backed applications.