How Snyk Helps with the OWASP Software Assurance Maturity Model
Oliver Dombai
Mathias Conradt
The OWASP Software Assurance Maturity Model (SAMM) has become a cornerstone for organizations looking to measure and enhance their application security (AppSec) programs. As a widely recognized framework, OWASP SAMM helps organizations structure and assess their security efforts, offering a roadmap for continuous improvement. Understanding its significance and how it can be implemented is crucial for any company serious about its software security posture.
The OWASP SAMM framework, originally introduced as OpenSAMM in 2009 and later updated in 2016, has evolved to become a flagship project under OWASP’s umbrella. It focuses on application security, providing a prescriptive approach to building, managing, and improving software security practices. Unlike descriptive models like BSIMM, which offer observations of current practices, OWASP SAMM is designed to guide organizations in adopting specific, actionable security measures.
The mission of OWASP SAMM is clear: to be the leading maturity model for software assurance, offering a measurable and effective way for organizations of all sizes and types to analyze and improve their software security. This comprehensive model supports the entire software lifecycle, including both development and acquisition, and is built to be adaptable and risk-driven. This versatility ensures that OWASP SAMM remains relevant across various industries and technologies.
But why is a DevSecOps maturity framework necessary? In an era where security threats are increasingly sophisticated, organizations can no longer afford a disorganized or reactive approach. A maturity framework like OWASP SAMM provides the structure needed to manage security effectively. It allows organizations to measure progress, set benchmarks, and follow field-proven best practices without reinventing the wheel. By learning from others and leveraging a community-driven approach, organizations can adopt practices that have been tested and refined over time.
OWASP SAMM stands out as a framework of choice for several reasons. It is:
Measurable, with defined maturity levels across security practices that allow organizations to improve over time
Actionable, providing clear pathways for enhancing these maturity levels.
Versatile, being technology, process, and organization agnostic, making it suitable for startups and large enterprises alike
Open, with freely available resources and a community-driven knowledge-sharing approach, unlike proprietary frameworks that restrict access to information behind paywalls
Globally relevant, focusing specifically on application security and DevSecOps, rather than a broad enterprise information security approach.
The structure of OWASP SAMM is designed to support several key activities:
Assessing the current software assurance posture
Defining a strategy for improvement
Formulating an implementation roadmap
Offering prescriptive advice on how to carry out specific activities.
However, successful implementation requires more than just a well-defined strategy. Human resources, processes, and tooling play a critical role in bringing these security practices to life.
Snyk, a developer-focused security platform
This is where Snyk, a developer-focused security platform, comes into play. Snyk offers tools that align closely with the security practices defined in OWASP SAMM, making it easier for organizations to implement and maintain their security posture. Snyk provides four modules that perform static analysis on an application’s codebase across multiple layers.
Snyk Code: a static application security testing (SAST) tool that scans the developer’s own code for vulnerabilities.
Snyk Open Source: a software composition analysis (SCA) tool that scans for vulnerabilities in open-source dependencies at the application level.
Snyk Container: scans open-source dependencies at the container image level, ensuring what goes into the image’s package registry is secure.
Snyk IaC: scans for misconfigurations in infrastructure-as-code files, such as Terraform and CloudFormation, addressing potential security risks in the underlying infrastructure.
The philosophy behind Snyk is to empower developers to take security into their own hands by integrating security into the tools they already use across the entire software development lifecycle (SDLC). This shift-left approach aligns perfectly with the prescriptive nature of OWASP SAMM, enabling organizations to implement security practices earlier in the development process and maintain a robust security posture throughout.
To further enhance security efforts, Snyk AppRisk provides a way to manage and prioritize risks across all organizational assets, ensuring that remediation efforts are focused where they matter most. This holistic approach to security, combined with the structured guidance of OWASP SAMM, allows organizations to build and maintain a mature, effective, and measurable software security program.
The SAMM & Snyk
Let’s look into the details of each business function and security practice and how Snyk can help. The diagram below highlights the security practices that Snyk can support - marked in purple.
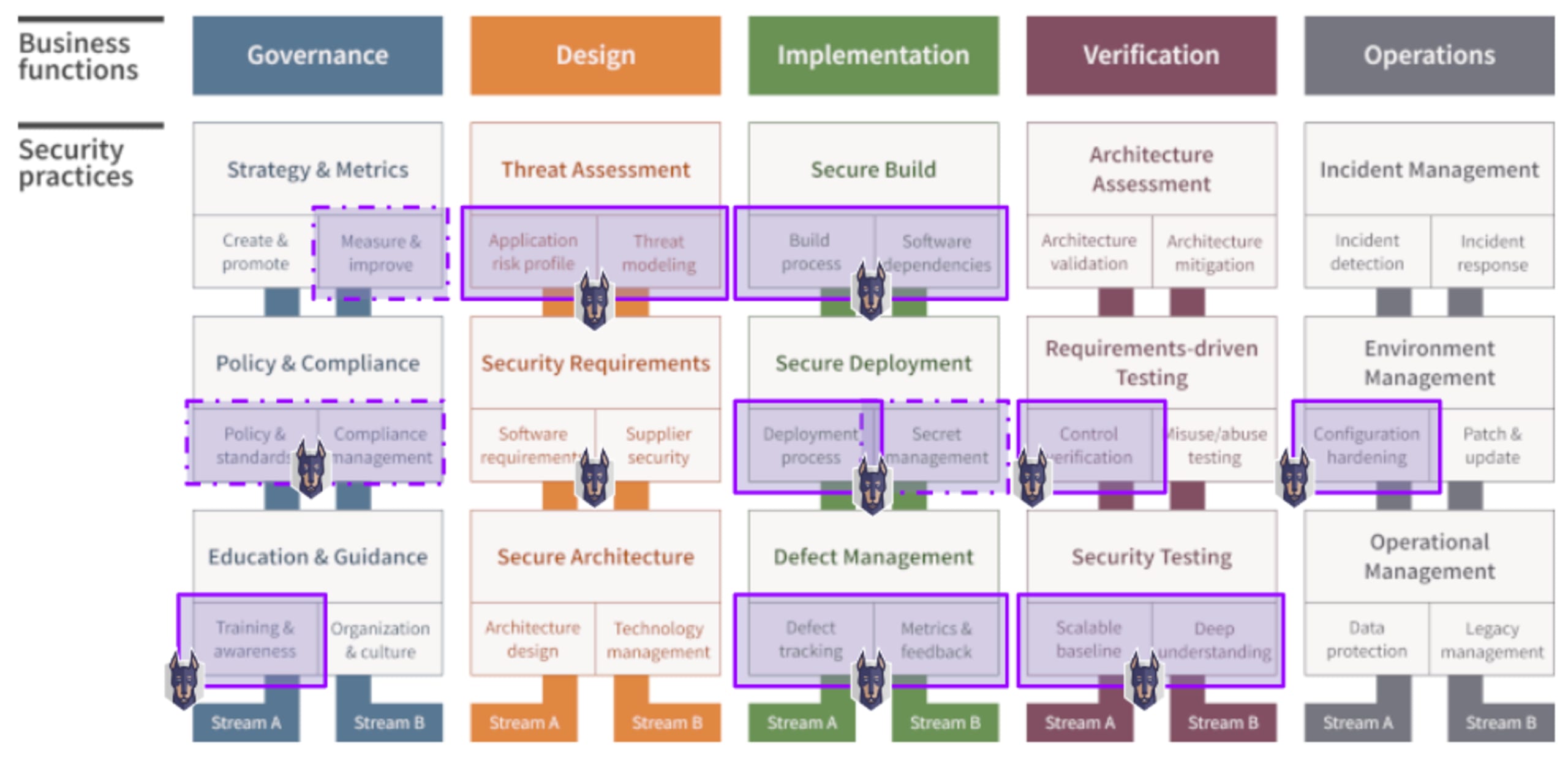
Business function: Governance
Security practice: Strategy and Metrics
The Strategy and Metrics practice within the Governance business function of the OWASP SAMM model is focused on creating and maintaining a cohesive and effective plan for achieving software security objectives across an organization. This practice ensures all security activities are aligned with the organization's goals, avoiding inefficiencies or counterproductive efforts. By developing a well-defined software security program, this practice helps prioritize security initiatives, ensuring that resources are allocated effectively.
In addition to planning, the Strategy and Metrics practice emphasizes the importance of tracking security program effectiveness through a metrics-driven approach. This involves defining and monitoring key performance indicators (KPIs) and other metrics that provide insight into how well the security efforts meet organizational objectives. This approach enables continuous improvement and alignment of the security strategy with the organization’s broader goals.
How Snyk can help with Strategy and Metrics
Snyk provides robust Reporting and Enterprise Analytics capabilities. These tools help organizations define and track metrics and KPIs related to their software security efforts, particularly in static application security testing (SAST) and software composition analysis (SCA). Snyk’s analytics provide detailed insights into the effectiveness of security programs, enabling informed decision-making and helping to refine and improve the overall security strategy.
By leveraging Snyk’s reporting capabilities, organizations can clearly understand their security posture, measure the impact of their security initiatives, and ensure that their software security program is aligned with organizational goals.
Security practice: Policy and Compliance
The Policy and Compliance practice within the Governance function of the OWASP SAMM model is designed to ensure that an organization meets internal security standards and external regulatory requirements. This practice involves aligning security policies with the organization’s business objectives, creating application-specific security baselines, and enabling automated audits that monitor compliance throughout the Software Development Life Cycle (SDLC).
Stream A focuses on establishing and enforcing security policies and standards across all applications, ensuring consistent adherence and monitoring.
Stream B emphasizes the measurement and reporting of compliance with third-party requirements, ensuring that each application meets external obligations and that these are documented and maintained.
How Snyk can help with Policy and Compliance
Snyk Security Policies and License Policies allow organizations to define and enforce guidelines for the use of open-source libraries. This helps maintain compliance with both internal security standards and third-party requirements.
Additionally, Snyk AppRisk ensures that all security controls defined by the organization's governance policies are in place and effectively executed, helping monitor and report on application-specific security requirements. By integrating these tools into the SDLC, Snyk helps automate compliance enforcement, reducing non-compliance risk and strengthening the organization’s security posture.
Security practice: Education and Guidance
The Education and Guidance practice under the Governance function of the OWASP SAMM model is centered around equipping all personnel involved in the software development lifecycle with the necessary knowledge and resources to create secure software. This practice emphasizes the importance of ongoing education and raising security awareness across the organization. It starts with targeted training for developers and expands to include other roles within the organization, ultimately evolving into role-specific training to ensure that security practices are effectively implemented.
Beyond just training, this practice encourages organizations to foster collaboration and transparency, promoting application security through shared knowledge and tools across teams. The goal is to build a security-conscious environment where all members engage in secure development practices.
How Snyk can help with Education and Guidance
Snyk Learn is a secure coding learning environment that provides developers and other team members access to interactive, scenario-based lessons about secure development. This tool supports the organization’s efforts to increase security awareness and improve skills through hands-on learning, making it easier to integrate secure coding practices into daily workflows.
Business Function: Design
Security practice: Threat Assessment
The Threat Assessment practice within the Design business function of the OWASP SAMM model is focused on identifying and evaluating risks at the project level based on the software's functionality and its operating environment. By understanding the potential threats and likely attacks specific to each project, organizations can make more informed decisions about prioritizing security initiatives and managing risks. This practice evolves from simple threat models and risk profiles to a sophisticated, comprehensive approach where threat information is closely linked to external factors and compensating controls. The goal is to provide a deeper understanding of the potential downstream impacts of security issues and maintain an up-to-date view of the organization’s exposure to threats.
How Snyk can help with Threat Assessment
Snyk AppRisk is an application security posture management solution that automates the classification of software assets such as repositories, based on custom policies. This enables organizations to maintain an accurate and centralized inventory of application risk profiles, helping them proactively monitor and update threat coverage across the organization. Snyk AppRisk helps organizations ensure their risk assessments are thorough, up-to-date, and aligned with the current threat landscape.
Business Function: Implementation
Security practice: Secure Build
The Secure Build practice within the Implementation business function of the OWASP SAMM model focuses on establishing a standardized and repeatable software build process that integrates security from the ground up. The practice emphasizes the automation of the build process to eliminate subjectivity and human error, ensuring that security checks, such as Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST), are embedded within the pipeline. This automation helps identify and address security regressions early, preventing insecure artifacts from reaching production.
Additionally, the practice addresses the critical role of software dependencies in modern applications. It stresses the importance of identifying and tracking the security status of third-party components, including transitive dependencies, to minimize the impact of potential vulnerabilities. In more advanced implementations, the same rigorous security checks applied to the application code are extended to these dependencies, ensuring comprehensive security coverage.
How Snyk can help with Secure Build
Snyk offers a suite of tools that align perfectly with the Secure Build practice:
Snyk Code provides Static Application Security Testing (SAST) capabilities, enabling developers to scan their code for vulnerabilities as part of the automated build process. This ensures that security issues are detected and addressed early, reducing the risk of insecure code reaching production.
Snyk Open Source focuses on scanning open-source dependencies, including transitive ones, for known vulnerabilities. This tool helps maintain a secure software supply chain by continuously monitoring and addressing issues in third-party components.
Snyk’s Automatic Fix PRs feature automatically creates pull requests to fix vulnerabilities detected in open-source libraries. This integration with Git systems streamlines the process of remediating security issues, ensuring that applications remain secure over time.
Snyk’s Pull Request Check automatically reviews every pull request for new vulnerabilities introduced by changes, helping to shorten security review cycles and maintain code integrity.
CI/CD Integration and Snyk CLI: Snyk integrates seamlessly with CI/CD pipelines, acting as a security gate by blocking builds that contain vulnerabilities above a certain severity threshold. Additionally, the Snyk CLI can generate a Software Bill of Materials (SBOM) in SPDX and CycloneDX formats, providing detailed insights into the components used within an application and their associated risks.
By integrating Snyk into the build process, organizations can automate security checks, manage vulnerabilities in both application code and dependencies and ensure a consistent, secure build process that aligns with best practices outlined in the OWASP SAMM model.
Security practice: Secure Deployment
The Secure Deployment practice within the Implementation business function of the OWASP SAMM model ensures the security and integrity of applications are preserved during the deployment process. This practice emphasizes automating the deployment process to reduce manual errors and incorporating security verification checks throughout. It also advocates for Separation of Duties, ensuring that deployment is handled by trained personnel not directly involved in development.
Beyond the mechanics of deployment, the practice also addresses the protection of sensitive data, such as passwords, tokens, and other secrets, which are essential for the operation of applications in production environments. Basic practices involve moving these secrets out of repositories and configuration files into secure vaults, while more advanced implementations generate secrets dynamically during deployment and continuously monitor for any unprotected secrets.
How Snyk can help with Secure Deployment
Snyk provides several tools that align with the Secure Deployment practice:
Snyk Code supports Secure Deployment by offering Static Application Security Testing (SAST) to identify vulnerabilities in the code before deployment, ensuring that only secure code reaches production.
Snyk Open Source aids in the secure deployment process by scanning open-source dependencies for vulnerabilities, including transitive dependencies, thus safeguarding the application from risks associated with third-party components.
CI/CD Integration and Snyk CLI: Snyk integrates directly into CI/CD pipelines, acting as a security gate that prevents the deployment of builds containing vulnerabilities above a specified severity threshold. This automation ensures that security checks are consistently applied and that only compliant builds are deployed.
Secret Management: Through Snyk’s partnership with GitGuardian, Snyk also helps manage and secure secrets, aligning with the second stream of the Secure Deployment practice. This integration enables the detection and mitigation of secret leaks, ensuring that sensitive information is adequately protected during deployment and in production environments.
By leveraging these tools, Snyk helps organizations automate their deployment processes, enforce security checks, and manage secrets effectively, ensuring a secure and reliable deployment pipeline that aligns with the best practices outlined in the OWASP SAMM model.
Security practice: Defect Management
The Defect Management practice centers on the systematic collection, tracking, and analysis of software security defects. This practice aims to ensure that software is released with a known level of security assurance by effectively managing defects throughout the development process. It emphasizes not only the identification and resolution of security defects but also the enrichment of defect data to derive meaningful metrics. These metrics can then guide decisions about the security of individual projects and the overall security assurance program. In advanced implementations, defect management is formalized, with real-time data analysis and trend detection playing a crucial role in shaping the organization’s security strategy.
How Snyk can help with Defect Management
Snyk provides robust tools to support the implementation of the Defect Management practice:
Snyk’s Web UI, Reporting, and Enterprise Analytics: These capabilities enable organizations to track all vulnerabilities systematically and generate detailed metrics. Snyk's tools allow teams to monitor key metrics such as the number of baseline issues, newly identified issues, preventable issues, and Mean-Time-To-Resolve (MTTR). This comprehensive tracking and analysis help organizations make informed, metrics-based decisions about security priorities.
Team and Project-Based Metrics: Snyk allows metrics to be grouped by teams or projects, providing insights into which teams are excelling in terms of security posture. This feature facilitates better management and accountability and introduces elements of competition and gamification, which can be valuable when developing security champion programs.
By leveraging Snyk’s tools, organizations can enhance their defect management processes, ensuring that security defects are tracked, resolved, and used to inform strategic decisions and improve overall security practices.
Business Function: Verification
Security practice: Requirements-driven Testing
The Requirements-driven Testing practice ensures security controls in an application function as intended and meet the project’s specified security requirements. This practice involves the incremental development and execution of security tests and regression cases, focusing on positive and negative testing. Positive testing verifies that the security controls perform correctly according to functional security requirements. Negative testing seeks to identify flaws and vulnerabilities by testing how the application handles misuse and abuse scenarios. In its more advanced stages, the practice includes security stress testing, such as denial-of-service tests, and emphasizes the continuous improvement of application security through automated security unit tests and regression tests for any identified and fixed bugs.
How Snyk can help with Requirements-driven Testing
Snyk supports the implementation of the Requirements-driven Testing practice by helping to identify vulnerabilities in both proprietary and third-party code:
Snyk Code allows developers to detect vulnerabilities in their code early in the development process, ensuring security controls meet the required standards and function correctly.
Snyk Open Source scans open-source dependencies for known vulnerabilities, ensuring third-party components integrated into the application meet the necessary security requirements and don’t introduce new risks.
Security practice: Security Testing
The Security Testing practice within the Verification business function of the OWASP SAMM model is dedicated to uncovering technical and business-logic application weaknesses, going beyond merely verifying that security requirements are met. This balances automated and manual testing methods to ensure thorough coverage. Automated security testing provides a scalable and efficient way to detect common vulnerabilities, or "low-hanging fruit." These tests are continuously refined and executed more frequently to catch bugs and regressions early in the development cycle.
However, automated testing has its limits, especially when it comes to complex attack vectors and business logic flaws that require a deeper understanding of the application. This is where manual expert testing becomes essential. Manual reviews are typically prioritized based on risk, recent changes, or major upcoming releases, ensuring that critical components receive focused attention. Organizations may also engage in bug bounty programs to leverage external expertise and uncover additional vulnerabilities.
The primary goal of Security Testing is to identify and expose vulnerabilities in an application to management and business stakeholders, helping them understand and address risks proactively.
How Snyk can help with Security Testing
Snyk Code enables automated scanning of proprietary code for vulnerabilities that helps catch common security issues early in the development process, making it easier to address them before they become more significant problems.
Snyk Open Source focuses on scanning open-source dependencies, including transitive dependencies, for known vulnerabilities. This ensures that third-party components integrated into the application do not introduce security risks.
CI/CD Integration and Snyk CLI: Snyk can act as a security gate, blocking builds that contain vulnerabilities above a specified severity threshold. This integration ensures that security testing is an ongoing part of the development lifecycle, catching issues as early as possible.
Business Function: Operations
Security Practice: Environment Management
The Environment Management practice within the Operations business function of the OWASP SAMM model emphasizes the importance of maintaining the security and integrity of an application’s operational environment. Even after deployment, ongoing security efforts are necessary due to the continuous release of new security patches and features for various components of the technology stack. Since many technologies are not secure by default—often to support backward compatibility or ease of setup—it's crucial to apply secure baseline configurations consistently across all systems.
This involves regularly monitoring for vulnerabilities and ensuring timely patching across all components to keep the environment secure. This includes establishing formal processes for configuration hardening, where configurations are continuously monitored, and any deviations from the security baseline are treated as security defects.
How Snyk can help with Environment Management
Snyk supports the Environment Management practice through its Snyk IaC (Infrastructure as Code) tool. Snyk IaC scans IaC files, such as CloudFormation, Kubernetes, ARM, and Terraform, for misconfigurations that could pose security risks. These scans are based on best practices and frameworks like CIS Benchmarks and AWS Well-Architected Framework, ensuring that your infrastructure is configured securely.
Snyk IaC can be integrated seamlessly into various stages of the development lifecycle:
IDE Integration: Developers can catch misconfigurations early in development.
Git Integration: Snyk IaC scans can be triggered as part of the Git workflow, ensuring that misconfigurations are detected before changes are merged.
CI/CD Automation: Snyk IaC scans can be automated through the CLI in a CI/CD pipeline, providing continuous security checks as infrastructure changes are deployed.
By using Snyk IaC, organizations can enforce secure configuration baselines consistently across their environments, proactively manage vulnerabilities, and ensure that their operational environments remain secure and compliant with industry standards.
Conclusion
In conclusion, the OWASP SAMM framework is invaluable for organizations aiming to strengthen their application security. By leveraging Snyk, organizations can effectively implement the security practices defined in OWASP SAMM, ensuring that they are not only meeting but exceeding their security goals.