The most common vulnerabilities in Maven Central and npm
2018年6月27日
0 分で読めますThe full version of this blog entry was originally posted by Snyk as a guest post on the Cloud Foundry blog.
In this post we’ll look at the most common types of vulnerabilities for two of the main ecosystems we track in our vulnerability database, namely Maven Central and npm. The Snyk Vulnerability database consists of vulnerabilities from over 1,000,000 open source packages we track that use Composer, Go, Maven Central, npm, NuGet, pip and Rubygems.
In 2017, the number of vulnerabilities published across our tracked ecosystems reached an all-time high, increasing by 83 percent from 2016. We can see what vulnerability types were the most common offenders in the two main ecosystems, which we’ll talk about here.
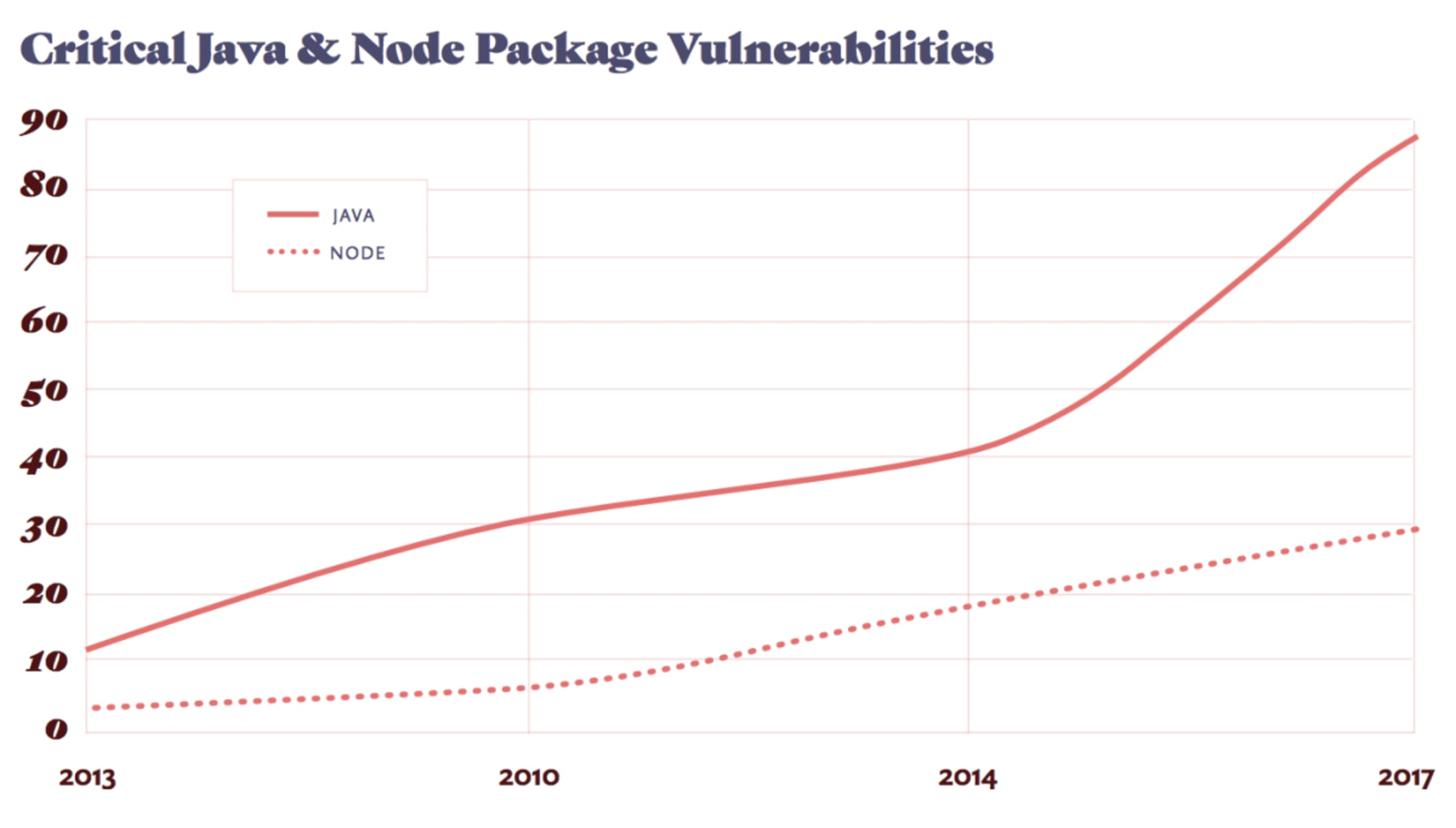
In our April and May posts, we’ll dig deeper into some of these vulnerabilities to see how they can be exploited.
JavaScript (npm)
1. Directory Traversal – Example: the st package.
The most common vulnerability in the npm ecosystem is Directory traversal. This is a vulnerability that typically occurs when a relative directory path is provided but not validated. Without validation, the relative directory passed in could reference a parent directory, gaining access to sensitive data. For example, one approach that is frequently used to execute an exploit is by using html entities, in which the ‘.’ is represented with ‘%2E’. In such cases, a request for the following url /%2E%2E/%2E%2E/%2E%2E/etc/password would result in /etc/passwd being leaked.
2. Resources Downloaded over Insecure Protocol – Example: Chromedriver.
This vulnerability allows attackers to perform a Man in the Middle (MitM) attack. When resources are downloaded over an insecure protocol, it is possible for an attacker to intercept this connection and alter the packages received.
3. Cross-Site Scripting (XSS) – Example: the handlebars package.
XSS attacks occur when an attacker tricks a user’s browser into executing malicious JavaScript code in the victim’s own environment. Such scripts can steal the user’s session cookies for the domain, retrieve typed password or credit cards, scrape or modify its content, and perform or modify actions on the user’s behalf, actions which would otherwise be typically blocked by the browser’s Same Origin Policy. For more info, check out XSS Attacks, the Next Wave.
Maven Central
1. Denial of Service (DoS) – Example: the jackson data processor.
A Denial of Service is a vulnerability that saturates the resources of the back end servers, that will then affect other user requests. This is often through CPU consumption but can also be filling server disks, memory or other resources.
2. Arbitrary Code Execution – Example: the Apache Struts library.
Arbitrary Code Execution is the running of malicious code sent to a vulnerable server. Often this code will call commands on the remote machine. It is often a result of another vulnerability, for example, a deserialization vulnerability, as in the struts case.
3. Cross-Site Scripting (XSS) – Example: Jenkins CI Server Plugin.
See the XSS description in the npm section above.
To see more common vulnerabilities in these ecosystems, see our full post on the Cloud Foundry blog.
Capture the Flag を始める
バーチャル 101 ワークショップオンデマンドで、Capture the Flag の課題の解決方法をご覧ください。
