190,000 users affected by Docker Hub’s security breach. Now what?
2019年4月29日
0 分で読めますOn Thursday, April 25th, 2019, Docker Hub shared the news of a security breach by way of an email communication that was sent out informing us about unauthorized database access that affected an estimated 190,000 users. Docker Hub has also released a FAQ for users regarding this breach: https://success.docker.com/article/docker-hub-user-notification
Full email sent to DockerHub users. Strong recommend to check your GitHub security logs for suspicious activity. pic.twitter.com/MtsIDyW8jM
— Kenn White (@kennwhite) April 27, 2019
In our recently launched Shifting Docker security left report we shared the security concerns of Docker images that ship with known vulnerabilities, and found that the top two most popular Docker base images each have over 500 vulnerabilities.
If you use Docker images, you can test them for free with Snyk, either directly from Docker Hub, or conveniently from your command line. You should test, for free, to see if your Docker images contain vulnerabilities to receive remediation advice for your projects and base images.
What personal information is affected by the security breach?
The following sensitive information may have potentially been exposed to the attacker:
Docker Hub usernames
Docker Hub passwords in their hashed form; however, we don’t have any details with regards to how they were hashed and can only hope that a secure cryptographic hash was put in place to protect the data per password.
GitHub and BitBucket tokens
What actions has Docker Hub taken to protect you?
Docker Hub may have reset your account details if it detected that your account was part of the data breach.
Furthermore, to mitigate potential damage resulting from the integration between your repo pipeline and Docker Hub with the use of tokens. Docker Hub has reset all automatic build tokens that were impacted.
What could potentially happen?
With tokens, developers often integrate their CI/CD pipeline with Docker Hub in order to then trigger automatic image builds and in order to publish new images directly to the Docker Hub repository as part of the CI/CD workflow. If attackers succeed in cracking the hashed password for an account, or if they access projects with the tokens they retrieved and issue changes in the Docker images being built, then they could compromise said Docker images. Furthermore, if they were able to access base images, upon which many Docker images are built, then they could effectively compromise a large user base.
At this point, we have no knowledge of any such supply chain attack successfully compromising Docker images; furthermore, Docker Hub has also communicated that none of the official Docker images have been compromised.
What should I do to protect my code?
1. Reset your account password
We would recommend that you reset your Docker Hub password to ensure that your account cannot be accessed by the attacker.Navigate to https://cloud.docker.com/settings and update your password:
2. Reset your account tokens
You should consider resetting your account tokens for these cases:
If you shared your GitHub tokens with Docker Hub, you should check your GitHub repositories to confirm that no unauthorized commits were made to your repositories by unauthorized persons.
GitHub security audit logs can be consulted at https://github.com/settings/security to review the log and assess if unauthorized actions were performed.
Even if you issued read-only GitHub tokens for Docker Hub, these tokens may still be used to read proprietary data in private repositories. We advise that you revoke all existing tokens and create new ones in their place.
If you store credentials in your source code, whether as plain-text or encrypted, reset your credentials to avoid any sensitive data being exposed through your GitHub tokens.
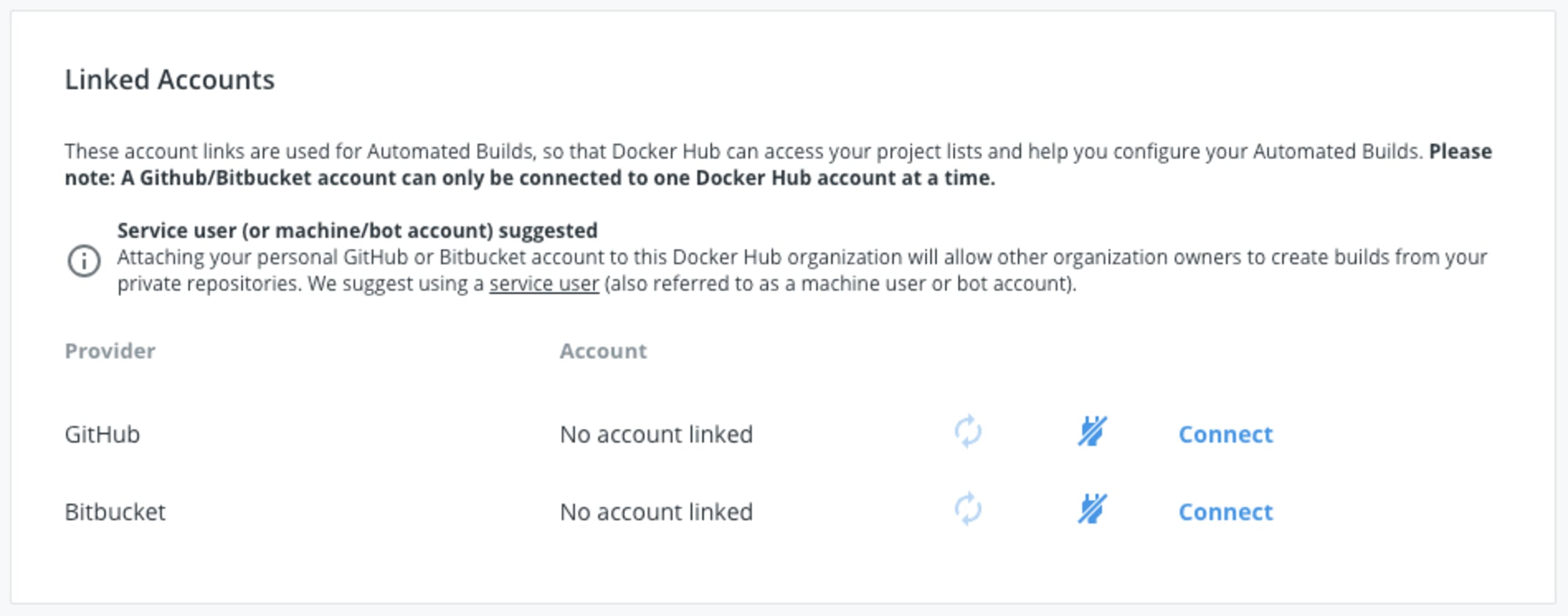
Navigate to https://cloud.docker.com/settings and re-connect your source code management systems, from the Linked Accounts area shown below:
Taking control of your Docker image security
Snyk’s solution for container vulnerability management provides insights and pro-active remediation advice for publicly known security vulnerabilities in third-party libraries that are used in your Docker images.
With both source code repository integration, as well as integration with registries such as Amazon Elastic Container Registry, Snyk routinely scans your Docker images and detects security vulnerabilities in your Dockerfile and base images early in the development process, as they are introduced.
開発者ファーストのコンテナセキュリティ
Snyk は、コンテナイメージと Kubernetes ワークロードの脆弱性を検出して、自動的に修正します。