Critical WebP 0-day security CVE-2023-4863 impacts wider software ecosystem
28. September 2023
0 Min. LesezeitQuick links
This month, Apple Security Engineering and Architecture (SEA) and The Citizen Lab at The University of Toronto's Munk School opened a pair of Critical vulnerabilities relating to maliciously formed WebP images which could be used to exploit the Chrome browser, as well as the webmproject/libwebp library from Google.
As of Sep 27th, 2023, the CVEs known to track this libwebp vulnerability actively include:
CVE-2023-4863: Opened Sep 11th, 2023 with a CVSS score of 9.6. EPSS score 31.86% (97th percentile*). Note: this CVE was originally scored 8.8 ("High") before further details were disclosed.
CVE-2023-5129: Opened Sep 25th, 2023, with a CVSS score of 10 (the maximum possible) and was later rejected on Sep 27th, 2023, by Google, the assigned CVE Numbering Authority, as a duplicate.
The vulnerability identified in the WebP library libwebp extends to more than just browsers, and Chrome-powered applications (e.g, 1Password for macOS). This is particularly significant because the libwebp library is used by many operating systems and popular application frameworks to render .webp images, including the popular Electron framework. As such, the libwebp vulnerability extends to software general-purpose software that includes Pillow and other applications such as ffmpeg, and Gimp. Note that some of these applications and software components are bundled into container images.
Versions of webmproject/libwebp from 0.5.0 up to and including 1.3.1 are affected. You must ensure your operating system and software projects require at least version 1.3.2 to remediate the vulnerability. However, note that libwebp is mostly used indirectly by other software that bundles it, which contributes to the wider software ecosystem impact of this vulnerability.
Google and other vendors rapidly released fixes to popular browsers in response to the initial CVE.
Snyk is monitoring this vulnerability and will update this article as new information arises. We will also be updating Snyk Vulnerability Database with the latest data as we have it, so please continue to run your regular scans to keep your projects secure. This libwebp vulnerability again shows that scanning your applications and container images for vulnerabilities is critical and something you should frequently do to keep your software supply chain secure.
Check back or follow us on X (@snyksec) for the latest news and developments. For more information, keep reading below.
EPSS scores the direct output of the EPSS model. These scores convey an overall sense of the threat of exploitation in the wild. The percentile measures the EPSS probability relative to all known EPSS scores. In this instance, CVE-2023-4863 has a higher probability of being exploited than 97% of all rated vulnerabilities — meaning that this vulnerability is more likely than most to be exploited by a malicious actor. This data is updated daily, relying on the latest available EPSS model version. Check out the EPSS documentation for more details.
What uses libwebp?
The vulnerability is likely widespread across developer ecosystems as well since higher-level programming languages will often use the underlying libwebp library. For example, the GoDot Game Engine used for creating 2D and 3D games depends on the libwebp library, and the widely used FFmpeg utility also uses the libwebp library.
Security experts are still determining the full breadth of use across applications since the vulnerability likely impacts software components that use .webp image codecs and render its content (such as browsers, design tools, etc.).
Explaining the libwebp vulnerability
The libwebp library processes images using the .webp format. It was created over a decade ago by Google and is used in most applications that render .webp images. The vulnerability may be exploited using a maliciously crafted .webp lossless file, which causes the vulnerable library to overflow.
Attacks against this vulnerability can range from denial of service (DoS) to possible remote code execution (RCE). As an example, closely related attacks such as the 0-day BLASTPASS exploit (Apple CVE-2023-41064,CVE-2023-41061) showed that malicious .webp images sent through the iMessage system could compromise a victim’s iOS device without any interaction by its owner.
Please refer to the Snyk Vulnerability Database page for more information and links to detailed analysis and proof-of-concept examples.
Detecting the libwebp vulnerability with Snyk
There are various ways to detect the libwebp vulnerability using Snyk. Using the Snyk CLI, you can test your projects locally, you can import your projects into Snyk using our SCM integrations, or you can use Snyk reports to quickly run a search for libwebp across all the projects that you have already imported into Snyk.
Testing your projects using the Snyk CLI
Snyk Container can alert you to operating system packages that depend on vulnerable versions of libwebp. Snyk can monitor your containers or Dockerfiles using the web interface, or you can manually trigger a scan using the CLI command: snyk container test.
The following example shows the Snyk CLI used to scan the Docker container image python:3.11.1 and test if it is for the libwebp 0-day security vulnerability:
Testing with the CLI for C++ projects
Snyk Open Source can alert you to a vulnerable libwebp version in your C/C++ application dependencies. Snyk can monitor your applications using our web interface, or you can manually trigger a scan of your open source dependencies using our CLI command: snyk test --unmanaged.
See the Snyk User Documentation for further details on C/C++ scanning capabilities.
Testing your projects using SCM integration
Importing your project into Snyk using our supported SCM integrations (GitHub, Bitbucket, GitLab, Azure Repos) will automatically trigger a test, which will enable you to use the Snyk UI to identify, prioritize, and fix the libwebp vulnerability in your projects.
Use reports in Snyk to detect the libwebp vulnerability across your projects
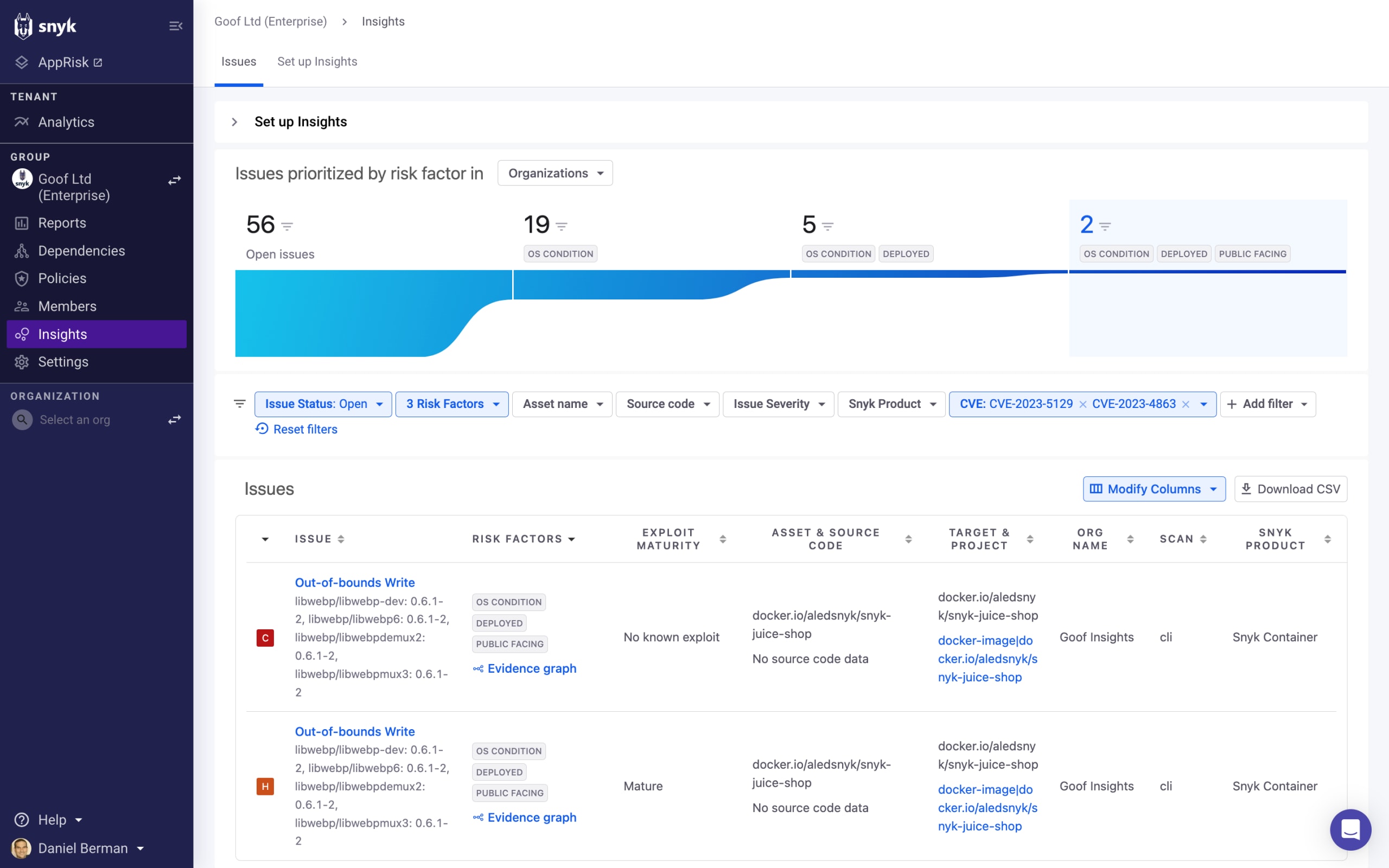
Snyk customers with access to Snyk’s reporting (Enterprise plan) can quickly identify libwebp in the projects they have already imported and are monitoring with Snyk. On the Issues Details report, filter the CVE: CVE-2023-5129 AND CVE-2023-4863.

Copy the URL to share this view with other team members or export it into a PDF for wider visibility across the business.
If you do find the issue, you’ll be able to see exactly where it’s being used. You can then click on the project itself to find more information about the issue and fix instructions.
Prioritizing fixes
You're likely to identify multiple libwebp issues in your projects, which can cause confusion as to where to focus your fix efforts first. Snyk offers several mechanisms to assist with the prioritization process.
Using Snyk’s Priority Score
Snyk’s Priority Score calculates many risk factors to help you quickly identify issues that should be addressed first. The score calculates a number of signals, such as EPSS, exploit maturity, CVSS, social trends, and more, and can then be used to quickly sift through the list of vulnerabilities and prioritize fixes accordingly. In the case of libwebp, the score will understandably be high in most cases.
The score is displayed for each libwebp issue on the Projects page and is also available within Snyk’s reports.

Using Insights in Snyk
For Snyk customers using Insights, you will be able to leverage additional application context to understand which issues pose more risk.
Insights aggregates and correlates data from across the Snyk platform to construct a 360° view of your application that includes all the components involved in producing it and the context of how it is deployed in production. This view enables Insights to help you better assess the risk a given libwebp issue poses by answering questions such as whether the issue applies to your environment or not, whether the code introducing the issue is deployed or not, and so forth.
You can open the Insights tab and use the CVE filters and the funnel at the top of the page to quickly hone in on the riskiest libwebp issues in your projects.
In the example below, two libwebp issues are being flagged as applicable to the operating system in use. They are associated with a container deployed to production that has a configured path to the internet, thus posing more risk.
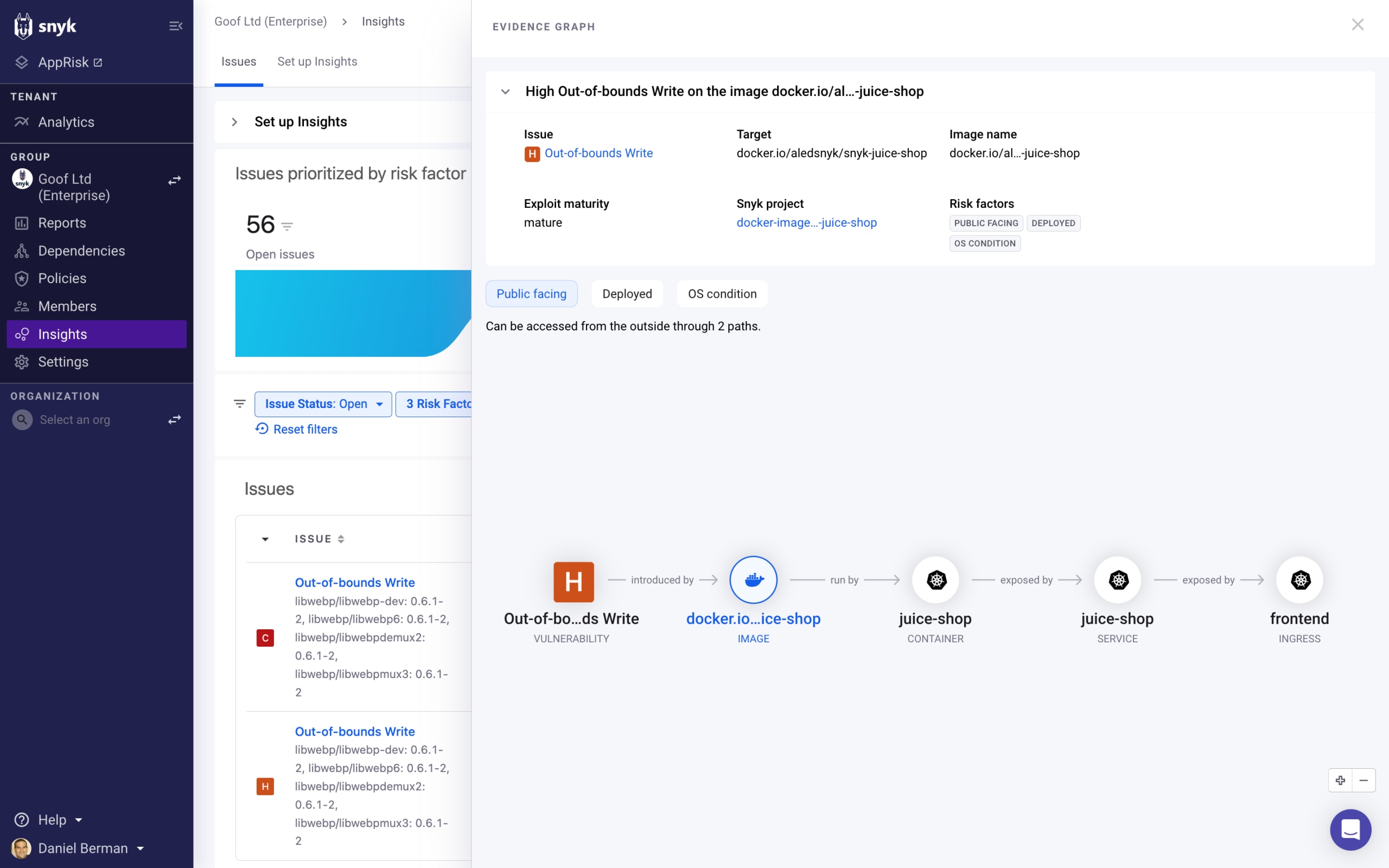
To understand exactly how the risk is being introduced and how it relates to the application, open up the Evidence graph for more context:
For more information about Insights, how to set it up, and how to use it, please refer to our online documentation.
How to fix the libwebp vulnerability
Fix libwebp in container base images
Update your base image to a newer tag with a fixed vulnerability. Fix pull requests with the required fix can be triggered directly from within Snyk for supported ecosystems.
For example, Snyk will recommend alternative container base images via the UI or the CLI, and when you import your source code repository via an SCM such as GitHub, it enables you to automate the container image fix by raising a pull request that updates the Dockerfile FROM entry:
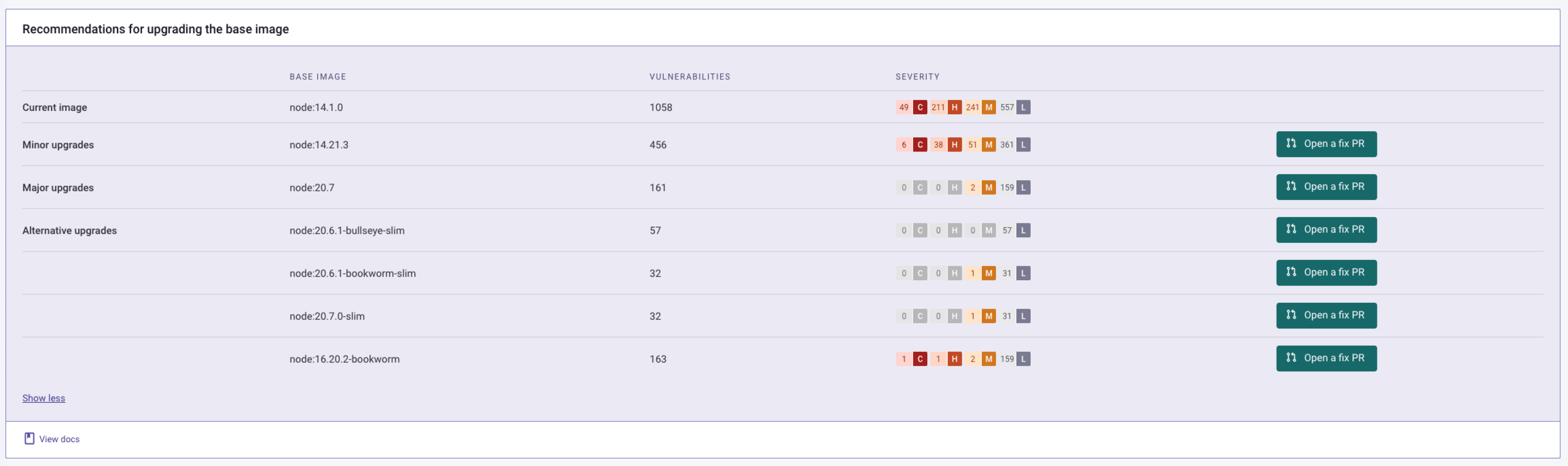
Snyk Container will recommend remediation for most Docker Hub official base images as fixes are published:
Fix libwebp in C and C++ projects
Update any webmproject/libwebp dependencies in your project to version 1.3.2 or newer and rebuild your application.
Next steps in responding to the ‘libwebp’ vulnerability
Test your projects with Snyk using the methods outlined in this article. To get started, sign up for a free Snyk account, then import and scan all potentially impacted projects using the import wizard.
Identify the highest priority fixes for the
libwebpvulnerability using priority scoring or Insights (for customers on the Snyk Enterprise plan).Apply fixes by updating the
libwebplibrary to version 1.3.2 or newer in your open source project dependencies or container images.Continue to monitor this situation as it unfolds, ensure you’re following us on X (@snyksec), and check back on the Snyk Blog for any developments as they occur. Snyk’s Security teams will update our resources regularly with the latest updates.