Recursos





Mostrando 25 - 48 de 611 recursos
Article
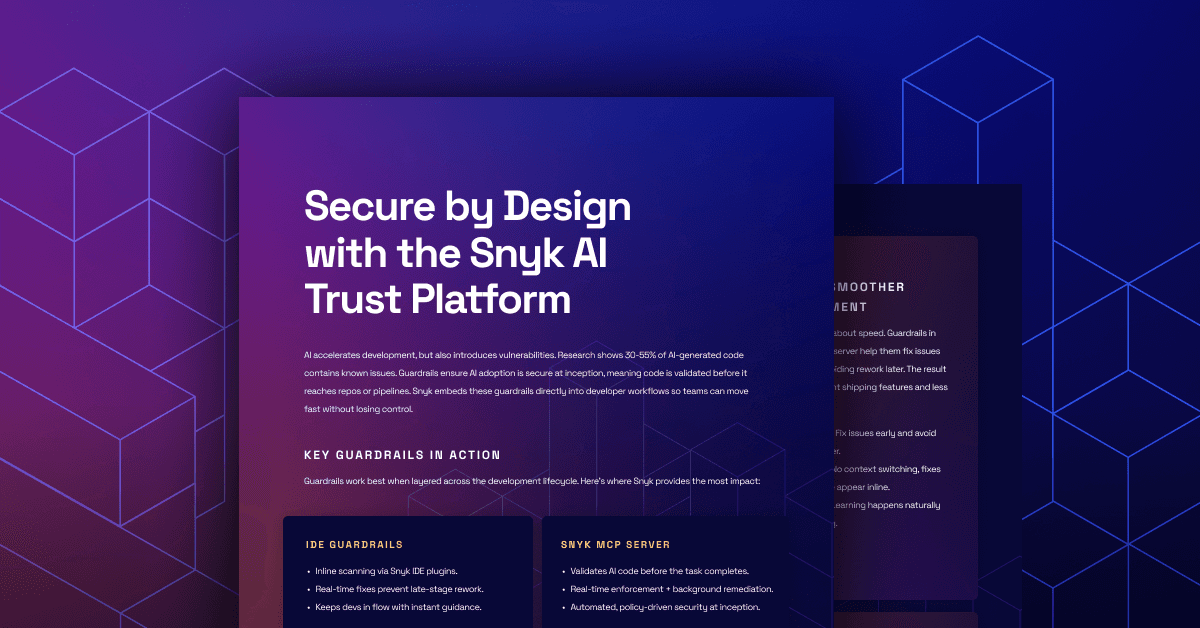
Let AI Detect and Patch Your Vulnerable Code: Claude Desktop and Snyk MCP Server
Integrate Claude Desktop with Snyk's official MCP Server to enhance security in your development workflow. Learn how to set up, configure, and use Snyk's security scanning tools to detect and patch vulnerabilities, streamlining DevSecOps and securing your code.