Recursos





Mostrando 49 - 72 de 639 recursos
The Frictionless Developer Security Experience: Securing at the Speed of AI
Traditional security creates friction, slowing developers down. Learn how a frictionless approach embeds fast, AI-powered security and automated fixes into the dev workflow. Empower your teams to build securely without sacrificing development velocity.
Let AI Detect and Patch Your Vulnerable Code: Claude Desktop and Snyk MCP Server
Integrate Claude Desktop with Snyk's official MCP Server to enhance security in your development workflow. Learn how to set up, configure, and use Snyk's security scanning tools to detect and patch vulnerabilities, streamlining DevSecOps and securing your code.
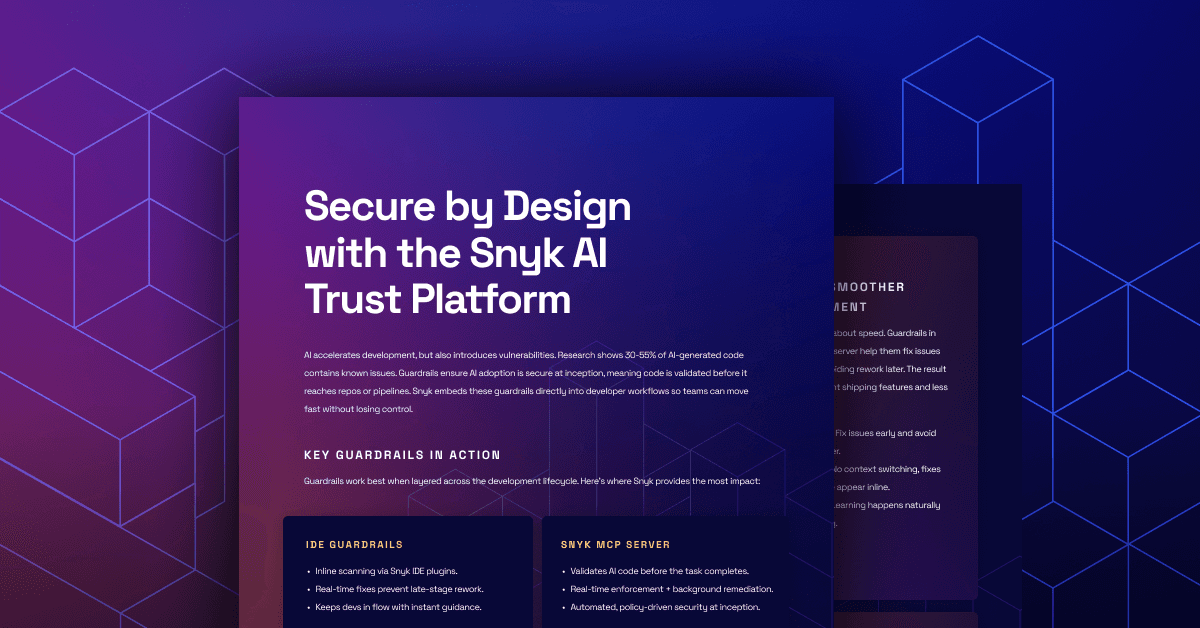
Segurança desde o início: a nova ordem no desenvolvimento orientado por IA
A segurança tradicional é muito lenta para o desenvolvimento orientado por IA. Conheça a “Segurança desde o início”, uma nova abordagem que proativamente evita vulnerabilidades em código gerado por IA e limpa backlogs com a Remediação Acelerada por IA.