How to scale successfully with Snyk’s Project Attributes and Tags
Josefa Riveros
2020年9月30日
0 分で読めますGrowth is a great feeling! Whether we’re talking about plants in the garden, dough rising, or increasing the number of developers and teams that are building applications and services in your organization—you can’t help but love seeing things grow.
However, growing without the right tools to support your scaling needs can open you up to newsworthy security risks in your organization. These risks can range from:
Developers can lose a lot of time finding the projects they need to work on, which means work is either rushed or shortcuts might be taken to hit new pressing deadlines.
Crippling vulnerabilities drowned in a sea of less severe issues given the great increase in how much more open source projects you’re using.
Shipping different types of applications at pace, which use a growing variety of projects means that high-level governance is no longer a safe and sufficient option.
Maintaining high productivity, granular governance, and clear prioritization of work is essential to minimize security threats, so you need something which can help you organize your projects whilst enabling low-level control of them.
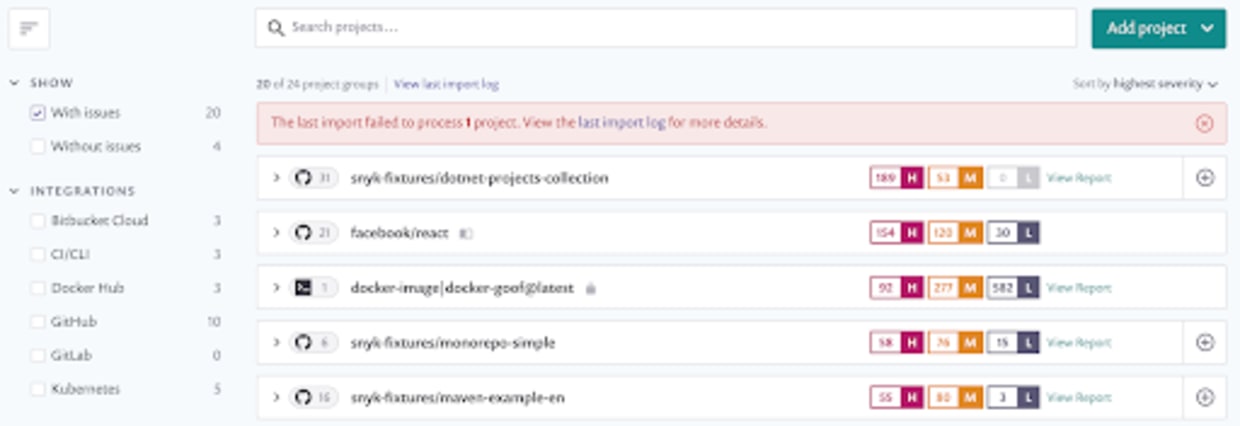
Project Attributes and Tags, with a side of Policies
It gives us great pleasure to announce the release of the solutions that’ll help you scale your use of projects within Snyk effectively: Project Attributes and Project Tags.
Not only do they sound like the next crime-fighting duo to hit our screens, but they also work in conjunction to help you maintain productivity, enable project-level governance, and drive prioritization. We’re going to give you a whistle-stop tour of what Project Attributes and Tags are and then we’re going to show you how to apply policies to projects.
Project attributes are fixed and non-configurable and are common “attributes” that projects are often grouped by in organizations. Within these attributes are multiple assignable values to help organize your projects effectively:
The environment that they are in: internal, external, frontend, backend, and more.
Their criticality to your business: high, medium, low.
The software development lifecycle stagethey’re in: production, development, sandbox.
In addition to enabling granular governance (we’ll get onto that in a moment), attributes can be used to filter projects in the project listing page, which means that you can find a small group of projects in an organization of thousands through simple filtering.

If you also want to organize and prioritize work based on criteria that are bespoke to your organization in addition to the project attributes that Snyk has provided, then you can create and assign project tags to your projects. Tags are completely flexible in what you want them to be, and which projects you want them to live on. Common examples of tags include:
You probably have numerous teams working in Snyk, but they’re likely responsible for a specific subset of projects. So, why not group those projects by tagging them with the team name to drive productivity across your teams?
What’s important to one organization is not as important to another, and every organization tends to have their own wonderful terminology to describe risk. Help yourself to some tags and group projects based on your own internal risk criteria.
Applications and services can have some incredibly interesting names, and they can sometimes use projects within one or more repositories. Having the ability to group projects by which application or service they belong to is a neat way of ensuring you effectively prioritize what your teams should work on.
After you’ve created and applied your tags to your projects, you can leverage one more capability coming your way in the (very) near future which is filtering your projects according to the tags, in the Project Listing page—that'll help you find that needle in the haystack. This feature will be available in the UI really soon, so stay tuned!

Apply policies to projects to stay secure at scale
As we've already teased, the new combination of policies and attributes provides you with the granular governance you need to apply project-level policies.
Projects differ from one another and it’s more than likely that there are different standards that you’d like to give them. A project that is externally-facing and mission-critical to your business will most likely receive a different set of rules than a project that is internally facing and backend. When creating a security or license policy, you can now assign it to a specific group of projects based on the attributes and values associated with them.
Let’s run through a quick scenario:
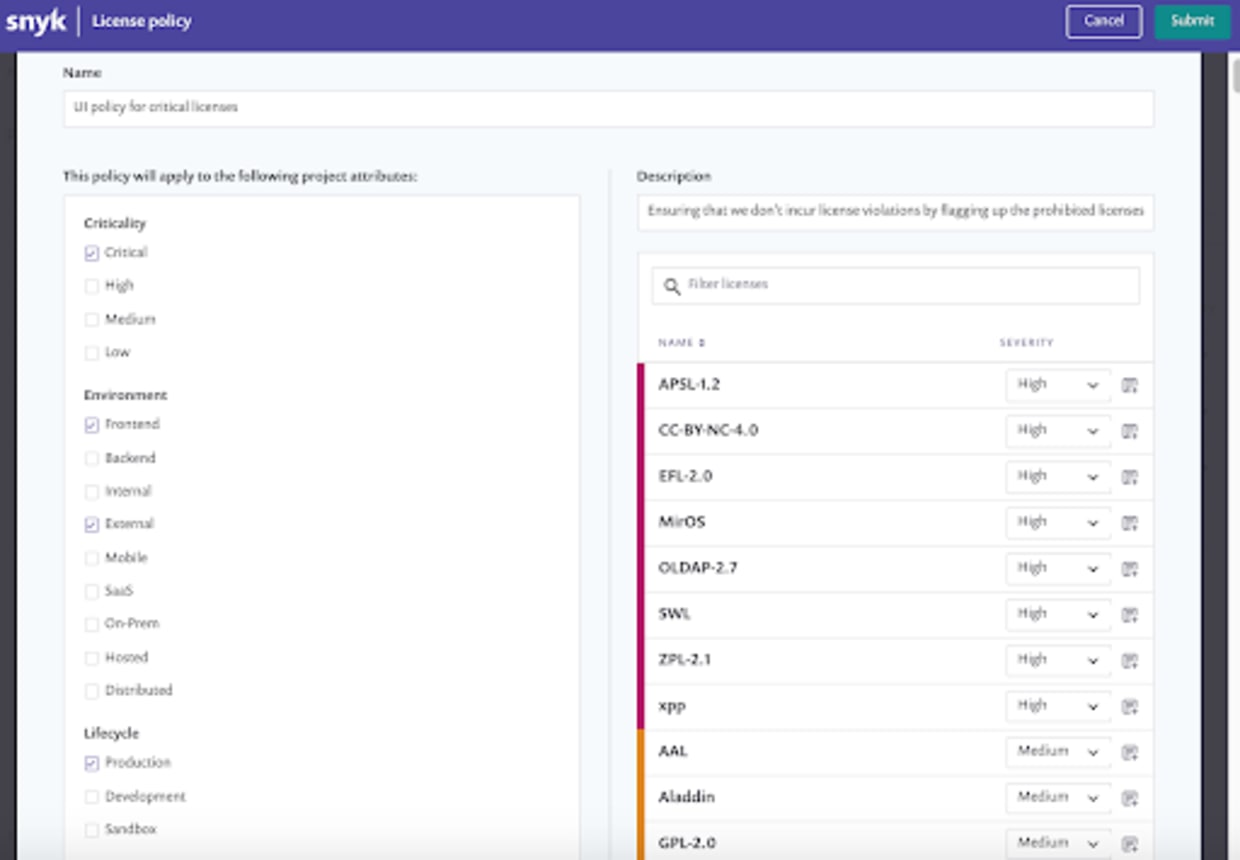
My organization’s legal team has a policy which states that it’s critical that we cannot risk license violation for anything our customers interact with in the UI of our application. This might occur if the projects that make up the application contain licenses the legal team has flagged up as prohibited. We have also been given a prioritized list of license violations, ranging from low to high severity. To avoid license violations, I need to create a policy which will catch the prohibited licenses in my team’s projects.
I begin by assigning the appropriate values to my project’s attributes so that I can group the critical projects. The values I’ve gathered these projects have is that they’re:
critical to the business
in production
frontend facing
external
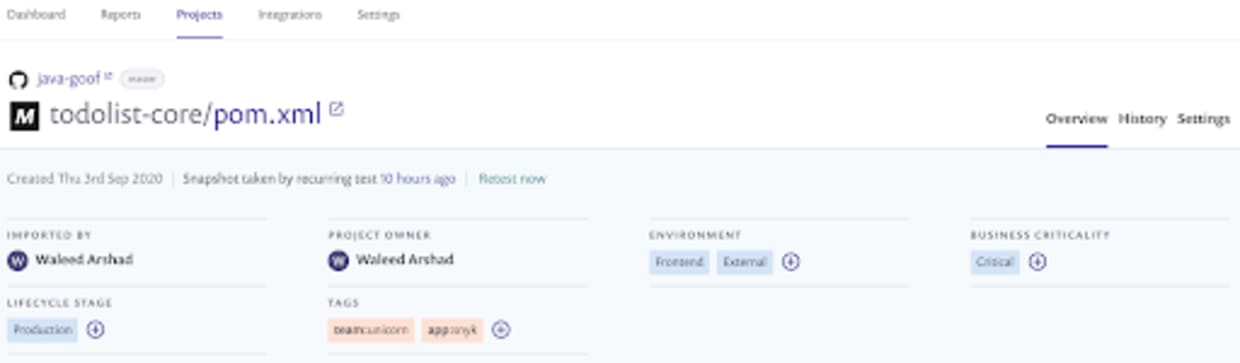
After I’ve applied the values to the right attributes for all of the projects in question, I can create a policy to apply to them.
In the policy tab, I can select whether I want to create a license policy that applies to organizations or attributes—in this example, I’ll be creating one specifically for attributes.
After I’ve modified the severity of the prohibited licenses to “High”, I can map them to the attributes of the appropriate projects. Once I click submit, the policy will be enforced. If the licenses in the policy are in any of the associated projects, my team will be notified in a number of places such as the project issues page and reports. I can also configure my PR checks to fail when high severity license issues are present.
What are you waiting for?
If you want to work securely at scale with your projects, whether you have a hundred or a hundred thousand of them, you should leverage the power of project tags, attributes, and policies today.
Project Attributes are available across all Snyk Open Source and Snyk Container plans, including the Free plan. Project Tags are available in Snyk Open Source and Snyk Container Pro and Enterprise plans. These features are available through the API and the UI.
Policies are features for Pro and Enterprise plans. License policies are available today, while Security Policies, and the ability to apply policies to project attributes, are currently in beta. Reach out to your Customer Success Manager if you’d like to get involved!
Capture the Flag を始める
バーチャル 101 ワークショップオンデマンドで、Capture the Flag の課題の解決方法をご覧ください。