Enriched content on Snyk’s publicly available vulnerability database
Dan Mckean
2019年4月8日
0 分で読めますAt Snyk, we’re focused on security and particularly making open source software more secure. As consumers of open source software ourselves, we're keen to give back to the community where we can, and increase the availability of information about open source libraries to everyone, Snyk user or not.
Our publicly available Vulnerability DB is one such example, and has recently undergone some improvements — making it even more powerful as an aid to security.
Full version breakdown
Firstly, for each package page we've added a table that lists all its versions. Alongside each version, we show how many vulnerabilities that version has, split by severity. This enables you to check up on a specific version, or simply find a version free of known vulnerabilities, that suits your needs.
Currently this new version table only appears for npm packages, such as jquery, bootstrap, or angular, but work is coming soon to support other package managers.
We've also included some helpful tags so you can more easily identify the latest version, deprecated versions, or prerelease versions (alpha/beta/release candidate). Licenses are also shown, so you can see at which version a license was changed.
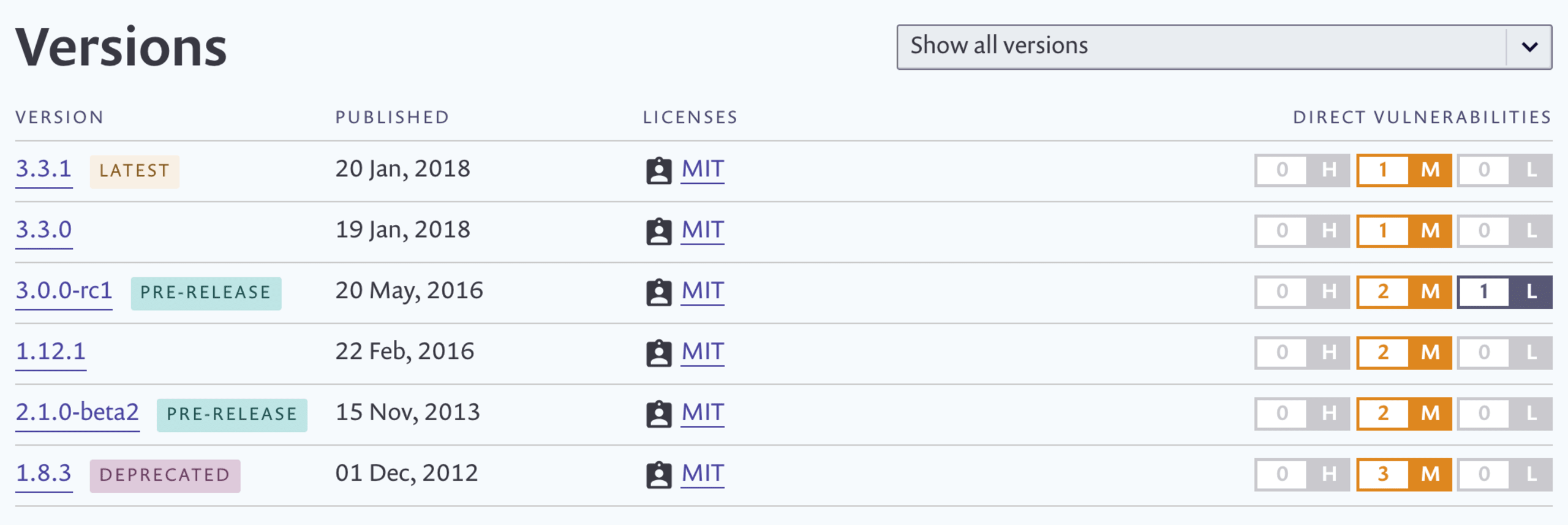
At the moment, we only display direct vulnerabilities — vulnerabilities that are in the package itself rather than in a dependency within it. Indirect/transitive vulnerabilities (those belonging to the package dependencies) will be arriving here soon.
Either way, you can of course also sign up for Snyk to scan your code in its entirety, dependencies and all!
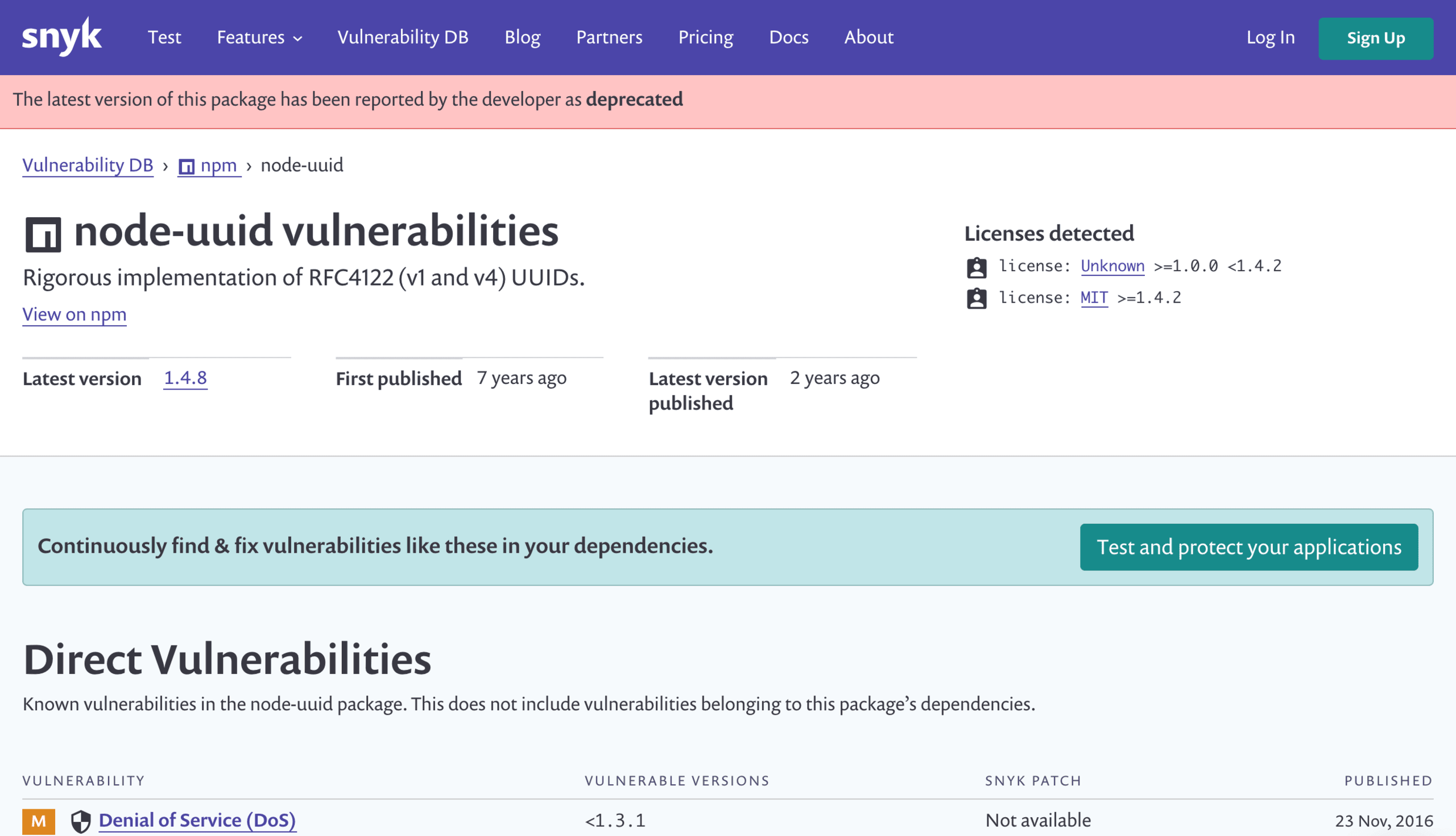
Deprecation warnings
In addition to the work we’ve done with package versions, we've also added a warning to any packages for which the latest version is marked as deprecated to help inform you about packages that are no longer supported. Again, this is currently for npm only, but support for more package managers is coming soon.
You may also notice some new headers that display the first and last published dates. Together, they can help you judge how established and well-maintained a package is before you commit to using it.
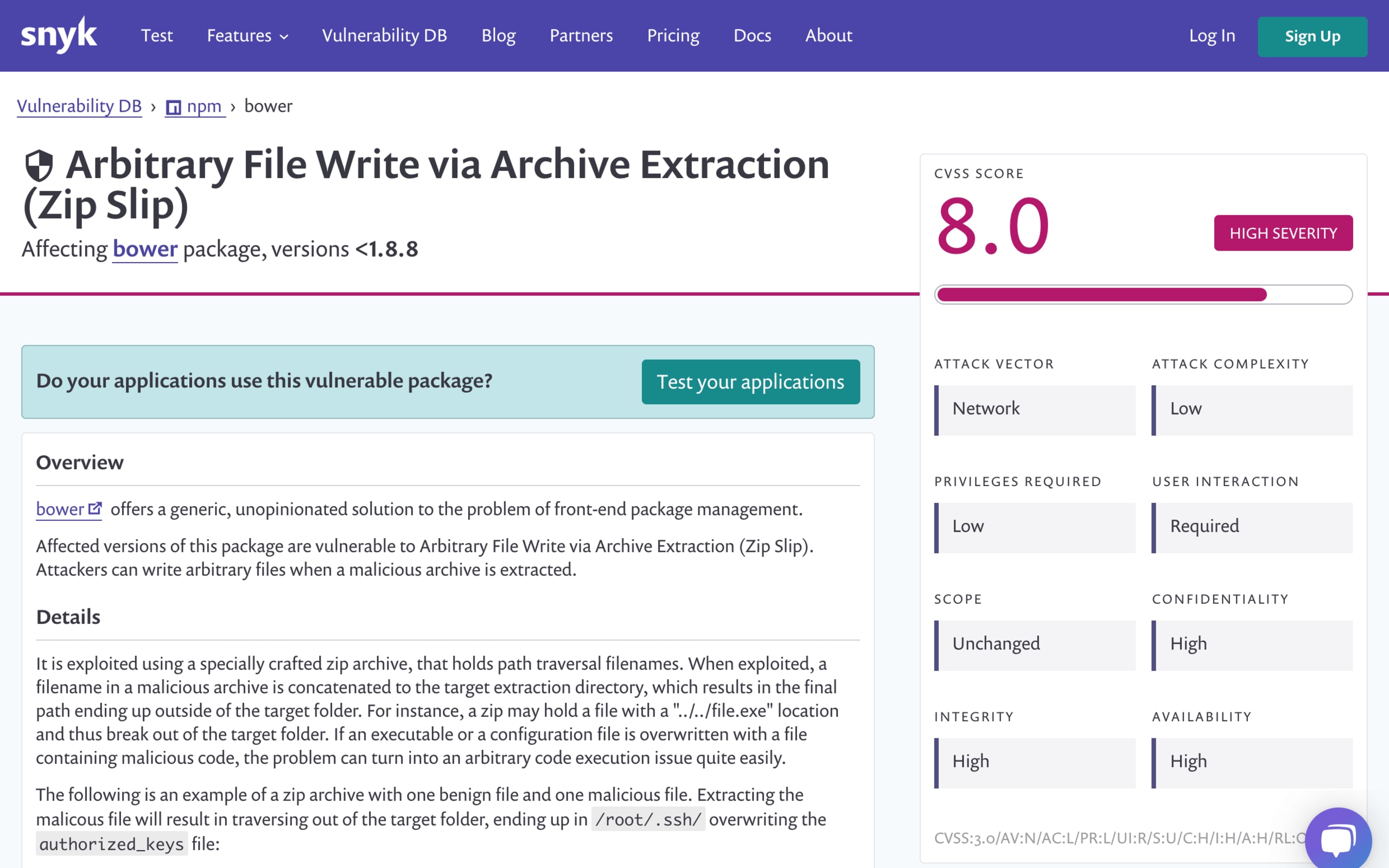
CVSS Breakdown
Last but not least, we've added a detailed breakdown of the CVSS score for any given vulnerability, for all package managers we support. This will help you determine just how much you need to worry about a given vulnerability based on what factors affect the score, while the existing details and remediation guidance will help you stay vulnerability free.
All this information (and more) is available via our API as part of our products full vulnerability database.
With the changes introduced to the publicly available vulnerability database we hope to make open source more secure, more accessible and easier to implement for everyone. To learn more about open source security you are welcome to subscribe to our blog, join the Secure Developer Community, or read our recently released report about the state of open source security.
脆弱性の自動検出および修正
Snyk は、コード、依存関係、コンテナ、およびクラウドインフラのワンクリック修正 PR と対策アドバイスを提供します。