Snyk and Trek10 publish new AWS Quick Start Guide to secure serverless CI/CD deployments
Jay Yeras
2020年9月29日
0 分で読めますAbout a year ago, I worked with Trek10 on building a solution that would help customers who develop serverless applications on AWS to quickly get started with an enterprise-ready deployment pipeline. The AWS Quick Start walks through the steps associated with building, managing, and securing a custom-built deployment pipeline.
Snyk integrates with AWS services, enabling organizations to improve the security of their applications. Snyk, an APN Advanced Technology partner, offers the Snyk Developer-First Security platform, which finds and fixes vulnerabilities in applications using open source, containers and serverless.
Now, Trek10, which helps clients design, build, and support AWS workloads, and Snyk have partnered to design and provide a CI/CD solution that provides an enterprise-ready, dynamic deployment pipeline for your serverless applications, follows AWS best practices for isolating resources and walks you through creating three AWS accounts (subaccounts): development, shared services, and production.

We are delighted to announce the release of Serverless CI/CD for the Enterprise on the AWS Cloud, by Snyk and Trek10, as an official AWS Quick Start, which peels back the layers involved in discovering critical vulnerabilities in open source dependencies in your serverless applications.
This production-ready reference deployment has been tested and validated by AWS, Snyk, and Trek10 experts, and aligns with AWS best practices for security and high availability. Let’s go over the architecture that is described in Figure 1:
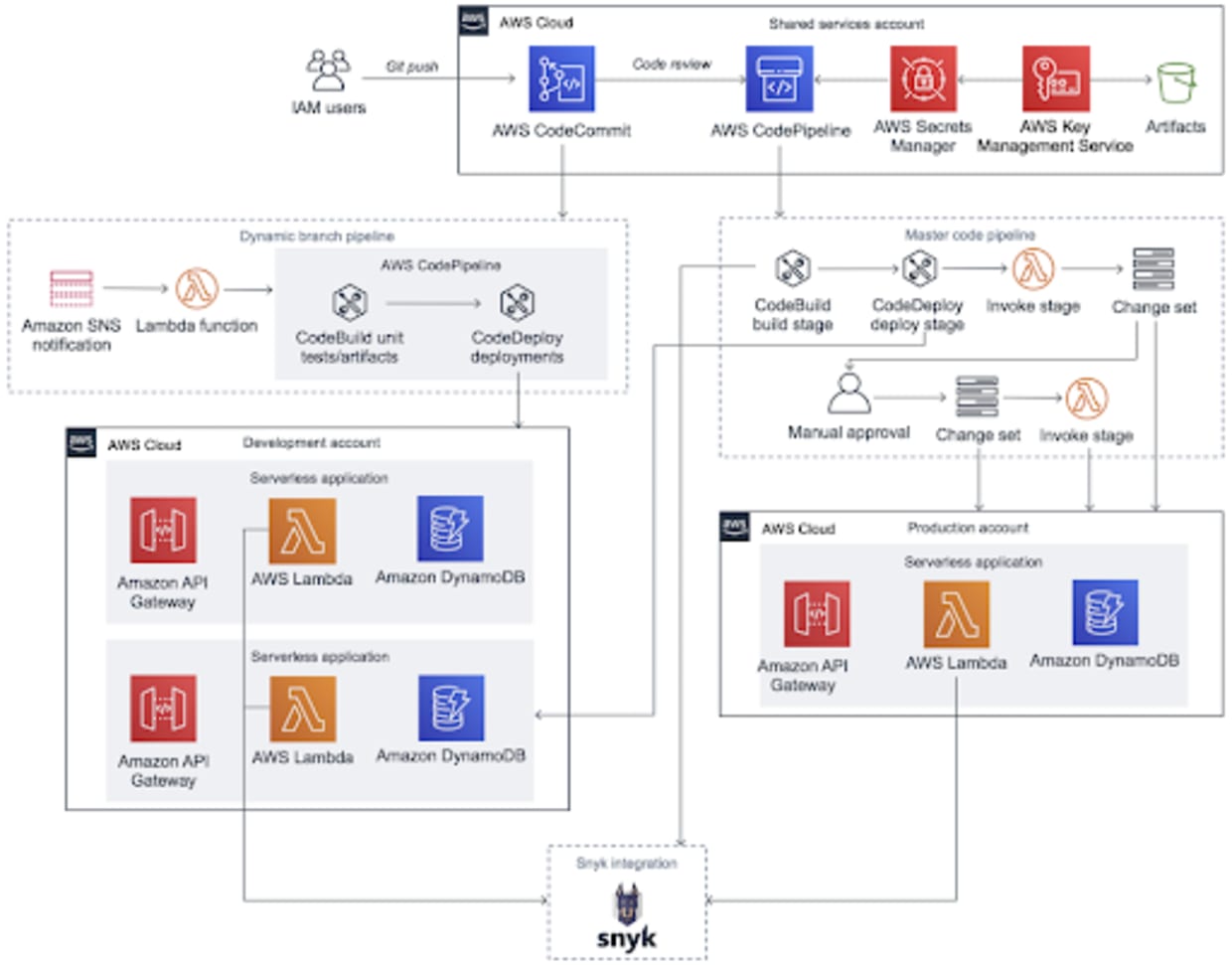
The solution enables cross-account access to development and production subaccounts as well as to Snyk’s API. It also deploys resources across three subaccounts consisting of AWS CodeCommit, AWS CodePipeline, AWS CodeBuild, AWS CodeDeploy and a sample serverless application leveraging Amazon API Gateway, AWS Lambda and Amazon DynamoDB. The serverless application will be monitored by Snyk’s AWS Lambda integration and allows for additional application scanning via the Snyk CLI through CodeBuild’s buildspec.yml file.
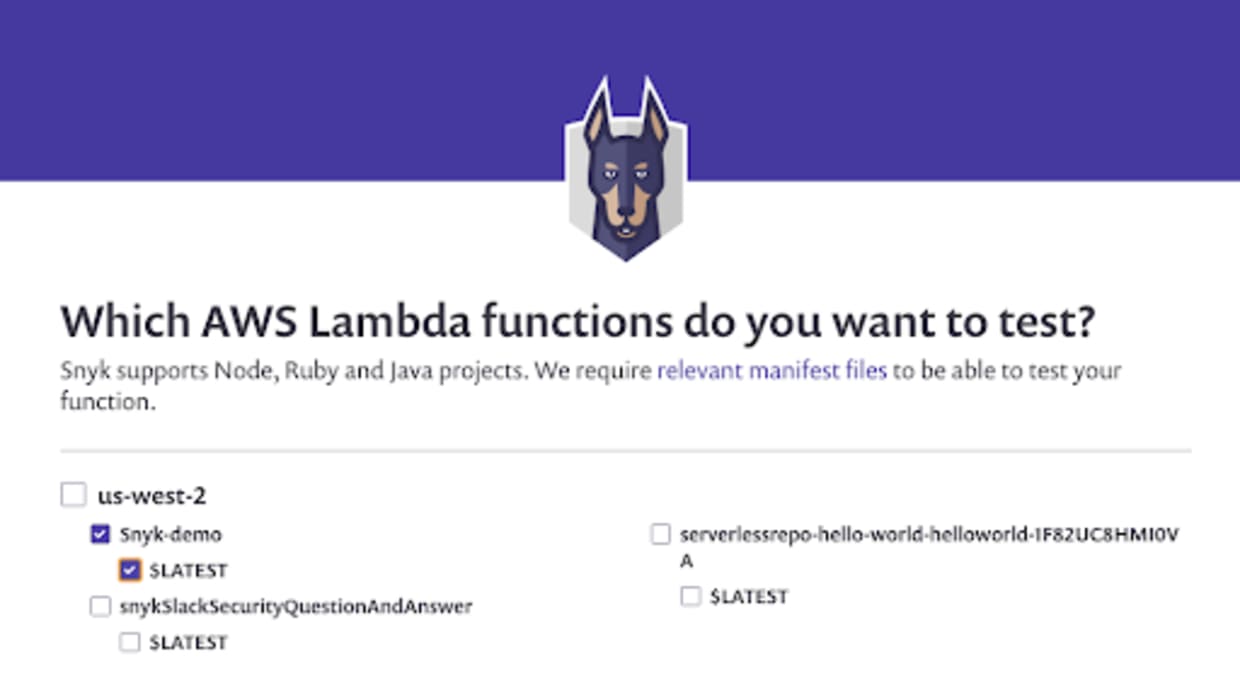

As shown in Figure 2, this integration allows Snyk to communicate directly with Lambda for each test it runs to determine exactly what code is currently deployed and what dependencies are being used. Each dependency is tested against Snyk’s vulnerability database to see if it contains any known vulnerabilities. Based on your configurations, if vulnerabilities are found, Snyk notifies you via email or Slack so that you can take immediate remediation action.
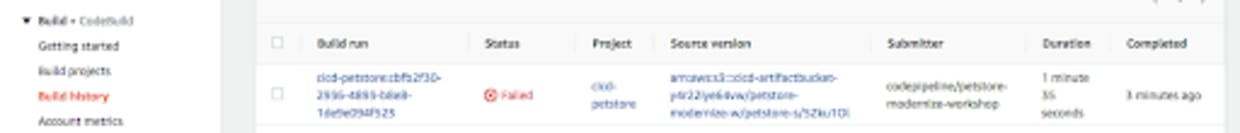
Similarly, you can fail your builds with AWS CodeBuild as shown in Figure 3 to avoid deployments that can leave you susceptible to an exploit.
We have worked hard to streamline the deployment of the solution. Not only have we automated the provisioning and deployment of these services, but we have simplified billing through Snyk’s AWS Marketplace listing (available for self-serve purchases as well as private offers). With advanced implementation support and expert guidance available from Trek10, learn more about Snyk’s collaboration with Trek10 to help customers embed security into serverless CI/CD deployments.
