Securing Artifactory using Snyk
Or Fattal
2019年8月19日
0 分で読めますWe are excited to share that starting today, you can make sure that vulnerable artifacts will not be used in your organization by using Snyk’s Artifactory plugin!
Snyk as your Artifactory gatekeeper
Snyk’s Artifactory plugin allows your team to define the desired security level and enforce it across the organization. The plugin prevents the team from using an artifact that does not meet the defined policy. This way, you can speed up development by detecting vulnerabilities in the very early stages of the workflow.
The plugin serves as a security gate and runs on your Artifactory server. Whenever someone in your organization attempts to download an artifact, Snyk’s Artifactory plugin triggers a scan for the requested library against our extensive vulnerability database and checks if the artifact has security vulnerabilities. In addition to security vulnerabilities, the plugin also verifies that the license of the library fits your license compliance settings. If any vulnerability or license issues are detected in the requested artifact, we will automatically block the download and add the relevant information to the artifactory server as metadata of the artifact.
The following illustration explains how the plugin works, step by step:
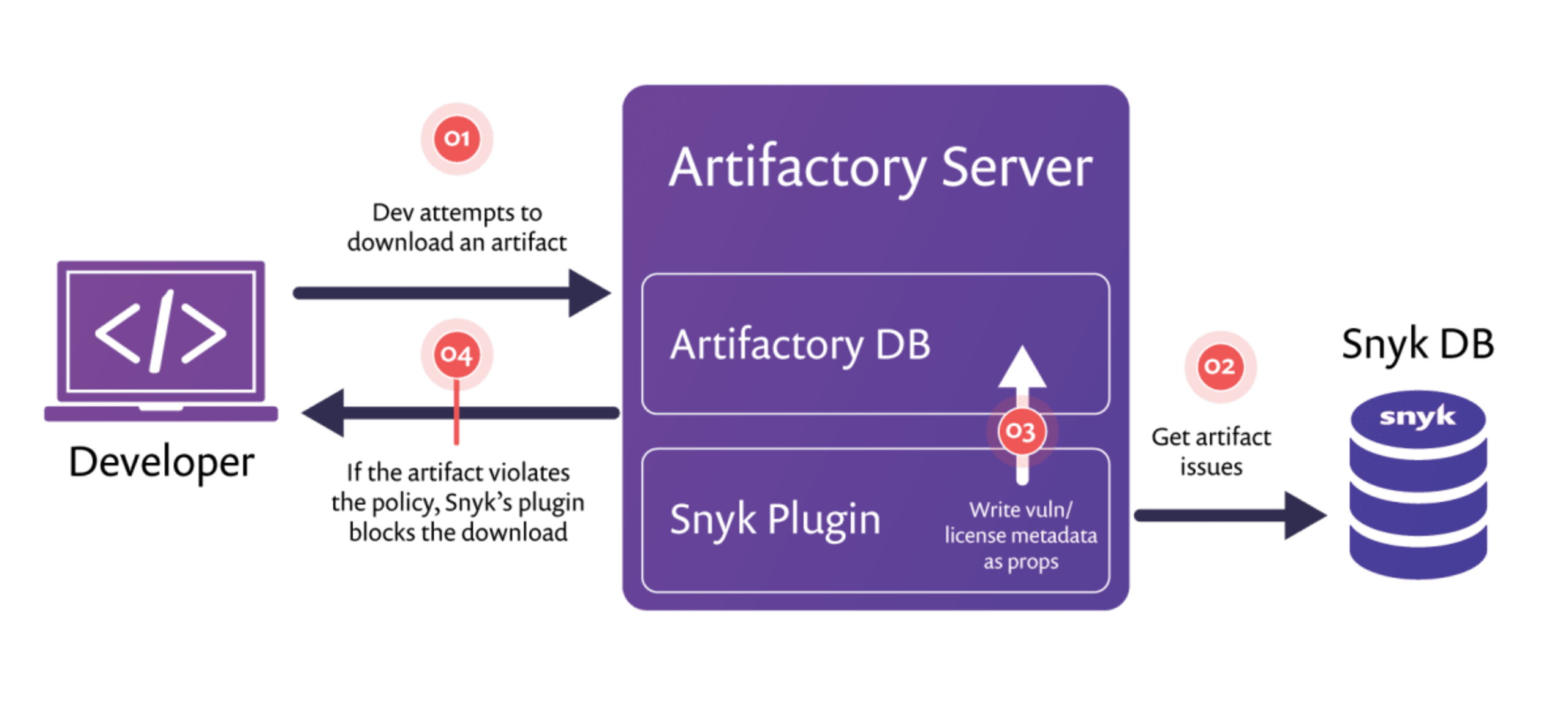
Enriching artifacts with actionable metadata
Snyk gives admins all the needed information in order to triage and take action for every artifact. Whenever Snyk analyzes vulnerabilities and license issues for a certain artifact, the results are being saved on the Artifactory server as additional properties of the artifact. By reviewing the results, admins can evaluate the issues found for an artifact and determine a course of action, before even using that artifact.
The following image shows how Snyk test results appear in the Properties tab of an artifact:

Giving admins the power to control what goes in and what notSnyk allows admins to control which artifacts should be blocked and which shouldn’t. As part of the plugin configuration, admins can set their own global blocking policy by defining which severity levels of vulnerabilities and license issues should prevent artifacts from being downloaded. The severity levels are set separately for security vulnerabilities and for license issues.When an artifact is being blocked due to a policy violation, the Artifactory admin can bypass the global policy for that particular artifact, allowing developers to download it anyway.
The following image shows how the severity thresholds are set in the plugin’s configuration file:

Powered by Snyk vulnerability and license database
Snyk Artifactory plugin is powered by Snyk’s comprehensive database foropen source security vulnerabilities. Our database is considered to be the most comprehensive in the industry. It was chosen to power the security of giants like Google and Microsoft and it includes 67% more vulnerabilities than public databases.
Start securing as early in the process as possible
With this native protection of your private registry, Artifactory users can enjoy from Snyk’s complete end-to-end security coverage that protects the development process from coding to deployment. Snyk’s uniquely offers native security insights within the development tools themselves such as IDEs, Git and build tools, and offers actionable one-click solutions for the alert.
How to get started?
Snyk’s Artifactory plugin works with any language that is supported in our test API: NPM, Maven, Ruby, Gradle, SBT and PIP; with .Net, PHP and GO (dep & vendor) coming soon.Getting started is extremely easy - you just need to download the plugin’s archive from ourrepo in GitHub and extract it to theplugins folder in your Artifactory server. You can read more about it in our Artifactory plugin documentation.
Stay secure!
