Cheat sheet: Meeting security compliance standards
15. September 2022
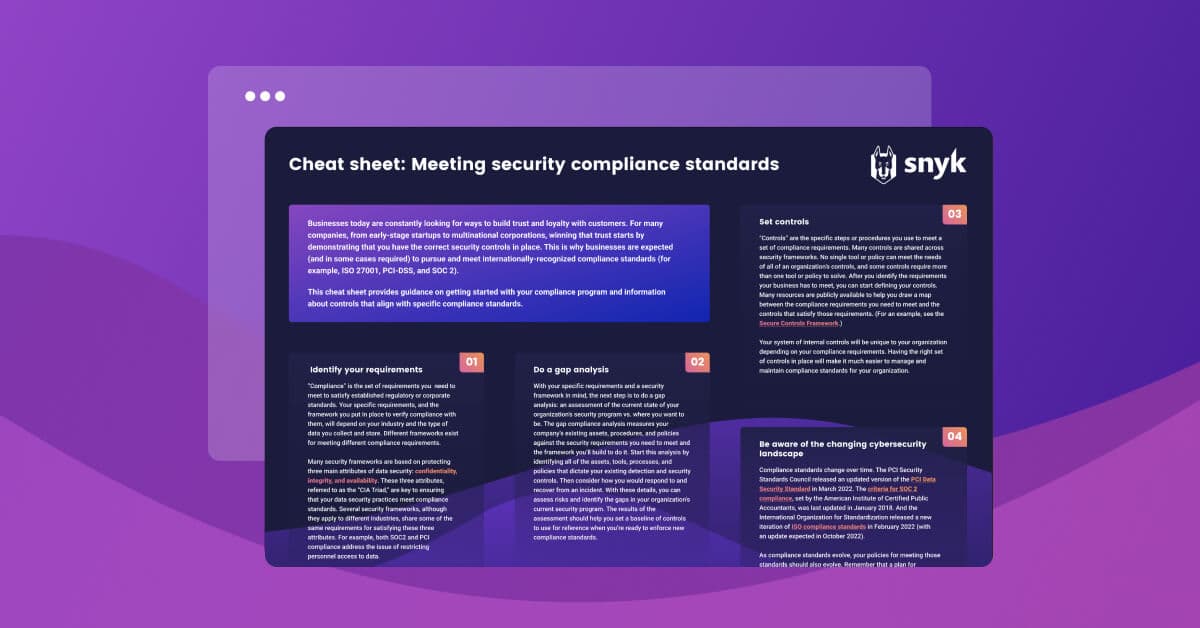
0 Min. LesezeitSecurity and compliance has a major role in every organization. Businesses are nothing without the trust and loyalty of their customers, and for many companies — from early-stage startups to multinational corporations — winning that trust starts by demonstrating that you have the correct security controls in place.
Internationally-recognized compliance standards, such as ISO 27001, PCI-DSS, and SOC 2, make up the industry-standard goals that most businesses and organizations pursue. This cheat sheet provides guidance on getting started with your compliance program, and information about controls that align with specific compliance standards.

Use the following steps as a guide for establishing your own compliance program, and check out the cheat sheet linked above for more information on how Snyk can help you establish controls for meeting SOC 2, ISO, and PCI compliance requirements.
1) Identify your requirements
Security compliance begins with determining the requirements your organization must meet to satisfy established regulatory or corporate standards. This list of requirements, and the way you implement them, will depend on the industry you're in, the priorities of your organization, the type of data you gather, and how it is stored. There’s no one-size-fits-all when it comes to security compliance, which is why multiple frameworks exist.
Though there’s no exact formula for a security framework, the three main attributes of data security — confidentiality, integrity, and availability — are a great place to start. These three attributes, referred to as the “CIA Triad,” are key to ensuring that your data security practices meet compliance standards. Common security frameworks often share some of the same requirements for satisfying confidentiality, integrity, and availability standards. For example, both SOC2 and PCI compliance address the issue of restricting personnel access to data.
2) Do a gap analysis
Now that you know your specific requirements and have chosen a security framework to work toward, it’s time to perform a gap analysis. A gap analysis is an assessment of the current state of your organization’s security program vs. where you want to be. The gap compliance analysis measures your company’s existing assets, procedures, and policies against the security requirements you need to meet and the framework you’ll build to do it. Allowing you to determine what steps you’ve already completed, and what still needs to be established.
Begin your gap analysis by identifying all of the assets, tools, processes, and policies that dictate your existing vulnerability detection and security controls. Then, use this information to assess how your organization would react to a hypothetical security incident. This information will help you perform an accurate risk assessment and identify the gaps in your organization’s current security program. This baseline measure will act as a reference point for enforcing and assessing new compliance standards.
3) Set controls
Controls are the specific steps or procedures you use to meet a set of compliance requirements. Many common controls, such as restricting access to personal data, are shared across the dominant security frameworks. It’s important to note that no single tool or policy can meet the needs of all of an organization’s controls — especially since solving some controls requires multiple tools or policies.
Now that you’ve determined your requirements and completed your gap analysis, you can begin to define your controls to cover the required areas. Thankfully, there’s no shortage of resources to help you match the compliance requirements you need to meet with the controls that satisfy them — we recommend the Secure Controls Framework.
4) Be aware of the changing cybersecurity landscape
As with most things in the cybersecurity and software development space, compliance standards are always evolving. The PCI Security Standards Council released an updated version of the PCI Data Security Standard in March 2022. The criteria for SOC 2 compliance, set by the American Institute of Certified Public Accountants, was last updated in January 2018. And the International Organization for Standardization released a new iteration of ISO compliance standards in February 2022 (with an update expected in October 2022).
As compliance standards evolve, your policies for meeting those standards should also evolve. Remember that a plan for compliance should be dynamic and up to date.
Establishing security and compliance standards with Snyk
We hope this guide helped simplify the process of establishing a compliance program. Compliance auditors want to see evidence of risk management in your SDLC. For more information on how Snyk features can help you establish controls for meeting SOC 2, ISO, and PCI compliance requirements, download the compliance cheat sheet today and book a demo to see Snyk in action.
Developer loved. Security trusted.
Snyk steht für Developer-First Security in einem Toolset, mit dem Sie Governance-Prozesse automatisieren und Compliance konsequent gewährleisten.