Blazing the trail for cloud native application security
Daniel Berman
21 décembre 2020
0 minutes de lecture2020 was an incredibly challenging year for all of us but with the dawn of a new year just over the horizon, it’s a great opportunity as any to take a few moments to appreciate the work done by our engineering and product teams. Hard work that was executed under difficult and strenuous circumstances and that has helped position Snyk as the leading, developer-first, Cloud Native Application Security solution on the market.
What is cloud native application security?
Software development as we knew it, up until a few years ago, has changed.
Application development and deployment processes have changed to support the model of more rapid and frequent deployments. And the code making up applications has changed—relying more and more on an assembly of open source code, proprietary code, containers, and infrastructure as code.
From an application security perspective, these changes pose a unique challenge that requires a unique solution, and at SnykCon this year we announced our Cloud Native Application Security platform, unique in the industry as the only developer-first solution that enables the entire cloud native application to be built quickly and securely in a DevOps environment.
Shall we start our recap then?
1. Integrating early and across the SDLC
The first step in vulnerability management is identifying there is an issue to start with. In 2020, we put a lot of effort into ensuring Snyk can be easily implemented across the different stages of an application’s lifecycle. This work included new IDE plugins, improvements to our GitHub and Bitbucket integrations as well as new integrations with private and container registries.
IDEs
Integrating security testing into the developer’s local development environment is a key ingredient in shifting security left. It enables developers to find and fix issues as early as possible and before they become too costly to fix. In 2020, Snyk added to its existing support for Eclipse and IntelliJ, and extended support for ALL major Jetbrains IDEs—WebStorm, PyCharm, PhpStorm, GoLand, and more.
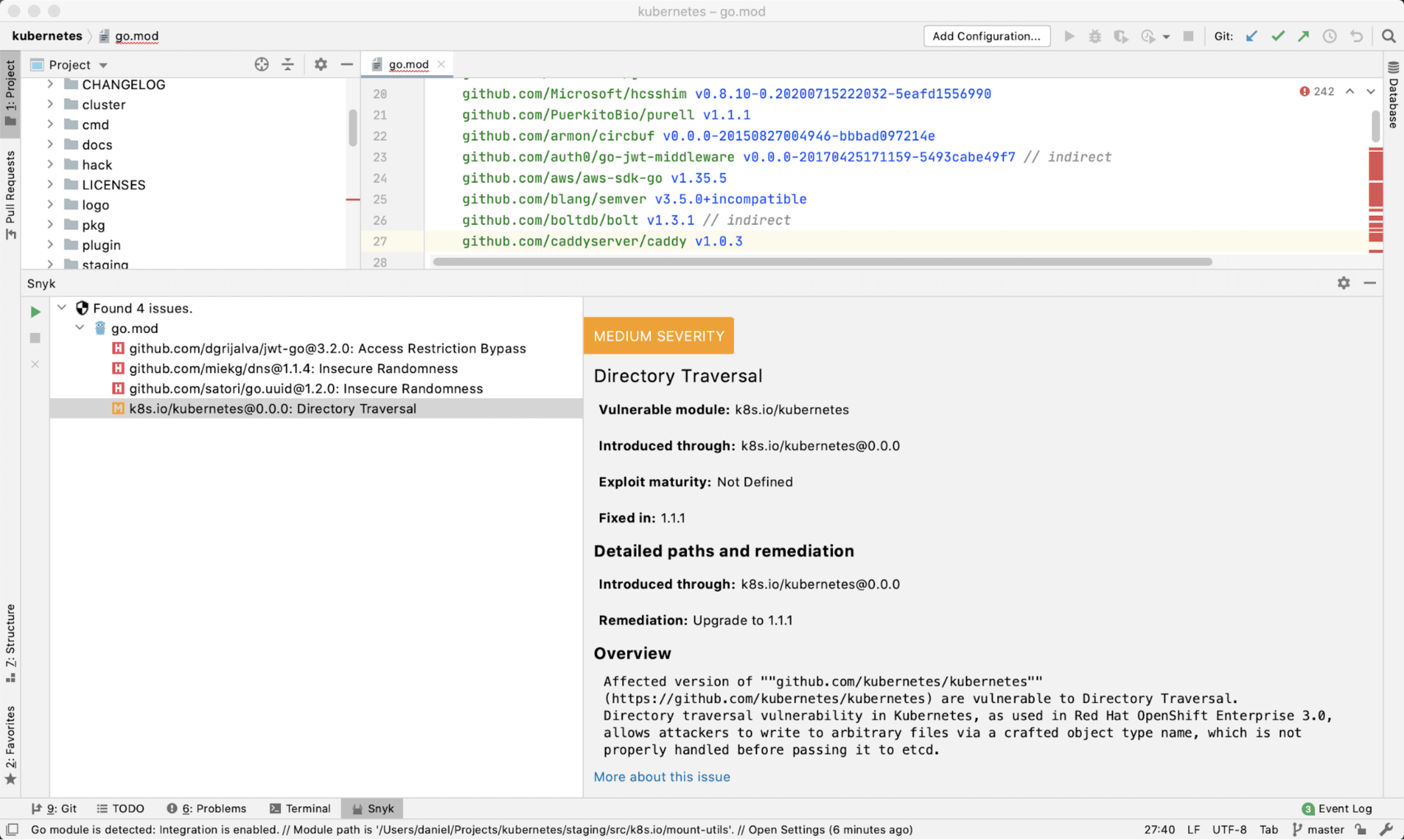
Snyk CLI
With the addition of Snyk Container and Snyk IaC, the Snyk CLI can do more than ever. This required some updates to how the CLI works in order to support existing and future functionality, but the net result is an improved workflow and new capabilities.
Snyk Container test
In place of the previous snyk test --docker command is the new snyk container test command, and the associated monitor subcommand. Aside from the CLI syntax, there are several improvements under the hood with the new container command:
As you might guess from the change in wording, we can scan more than just Docker containers. Snyk works great with any OCI containers, even if you do not have a Docker engine running. If you’re a podman user, or you build with tools like jib for your Java apps, Snyk can scan it.
If you have extracted an archive of the files from a container image and want to scan that rather than the image itself, Snyk Container now handles that.
And if you use distroless images to reduce your base image vulnerabilities, the new Snyk CLI properly scans those, too.
Plus, now that there are subcommands for
containerandiac, the built-in help system has been streamlined and improved, so you can get context-sensitive help when you need it.
Snyk IaC test
Snyk Infrastructure as Code (IaC) was our 3rd major product release this past year - more on that below. Initially, Snyk IaC only supported scanning from git repositories, but more customers wanted to automate their testing as part of their CI pipelines and so we added support for these tests in the Snyk CLI. You can scan Kubernetes and Terraform files using the snyk iac test command.
Git-based workflows
This year, we also focused on improving our existing integrations with the various git-based source code management systems, making them more developer-friendly and ensuring they provided a more native experience to their respective users.
GitHub
As you’d probably expect, our integration with GitHub is the most popular integration point with Snyk. As such, we are continuously rolling out new features to make the experience as frictionless as possible.
First, we added the option to configure the GitHub account on whose behalf Snyk’s fix and upgrade PRs are opened, as well as the ability to assign these PRs to a specific contributor in the repository. We also introduced the option for a contributor to request to skip a failed Snyk test.

GitHub security integration
GitHub launched their 3rd party security integration capabilities in October, enabling us to provide results from Snyk Container and Snyk IaC directly in the GitHub Security tab for your repos. We’ve been supporting GitHub Actions for some time and this new capability allows developers who are already using GitHub extensively to get their security detail reports in the GitHub UI.

Dockerfile scans from SCM
For all the good that comes with containers, one of the side effects is that the images end up stored separately from the Dockerfiles that are used to create them. From a security perspective, that means you don’t know whether your container is “good” until after you build it and then run it through a scanner.
Until now. Snyk already integrates with your favorite SCM tools and since your Dockerfile is likely stored alongside your code, we have added the ability to detect and scan the Dockerfile directly from a repo, then check which base image you’ve selected and report on the vulnerabilities present in that base image. This is designed to make it easy to get started with container scanning and to show immediate results since the base image is often the source of most vulnerabilities when you’re getting started.
As an added benefit, you can now associate the detected Dockerfile container image tests you run. Associating these two objects has always been possible in Snyk Container, but this streamlines the process as you no longer need to hunt through git repos to find your Dockerfile, and you can easily tell which images are linked to particular Dockerfiles.
Bitbucket
Bitbucket Cloud users were glad to hear that Snyk added support for Code Insights, enabling them to gain visibility into their issues from within the Bitbucket user interface. We also enhanced the Snyk Pipe—used for scanning for vulnerabilities as part of Bitbucket’s CI/CD pipelines—to support Code Insights as well.
Azure Repos
We also added support for Azure Repos Server, complementing our support across the Microsoft Azure ecosystem - from Azure Repos (cloud-based and now on-premises as well), and running through Azure Pipelines, Azure Container Registry, and Azure Functions.
2. Enhancing ecosystem support
In 2020, we also improved our coverage for existing programming languages and extended Snyk’s security testing to support more package managers and more ecosystems.
Java
We improved the security scanning of Java Gradle projects imported from Git repositories (GitHub/GitLab/Bitbucket/Azure Repos) by adding additional support for gradle.lockfile files. Using lock files has a number of benefits, but in the context of Snyk's security testing, guarantees more accurate and complete results. More information is available here.
Python
Reflecting the popularity of this ecosystem, we have seen a steady increase in the number of Python projects being tested by Snyk users. As such, this year saw a number of improvements made to help organizations using Python to better secure their codebase. We added Poetry support, enabling users of this up-and-coming Python package and project manager to test and monitor their projects via the Snyk CLI, and also added Pipenv support in our SCM integrations. To make it easier to fix Python vulnerabilities we added automated remediation workflows for Python.
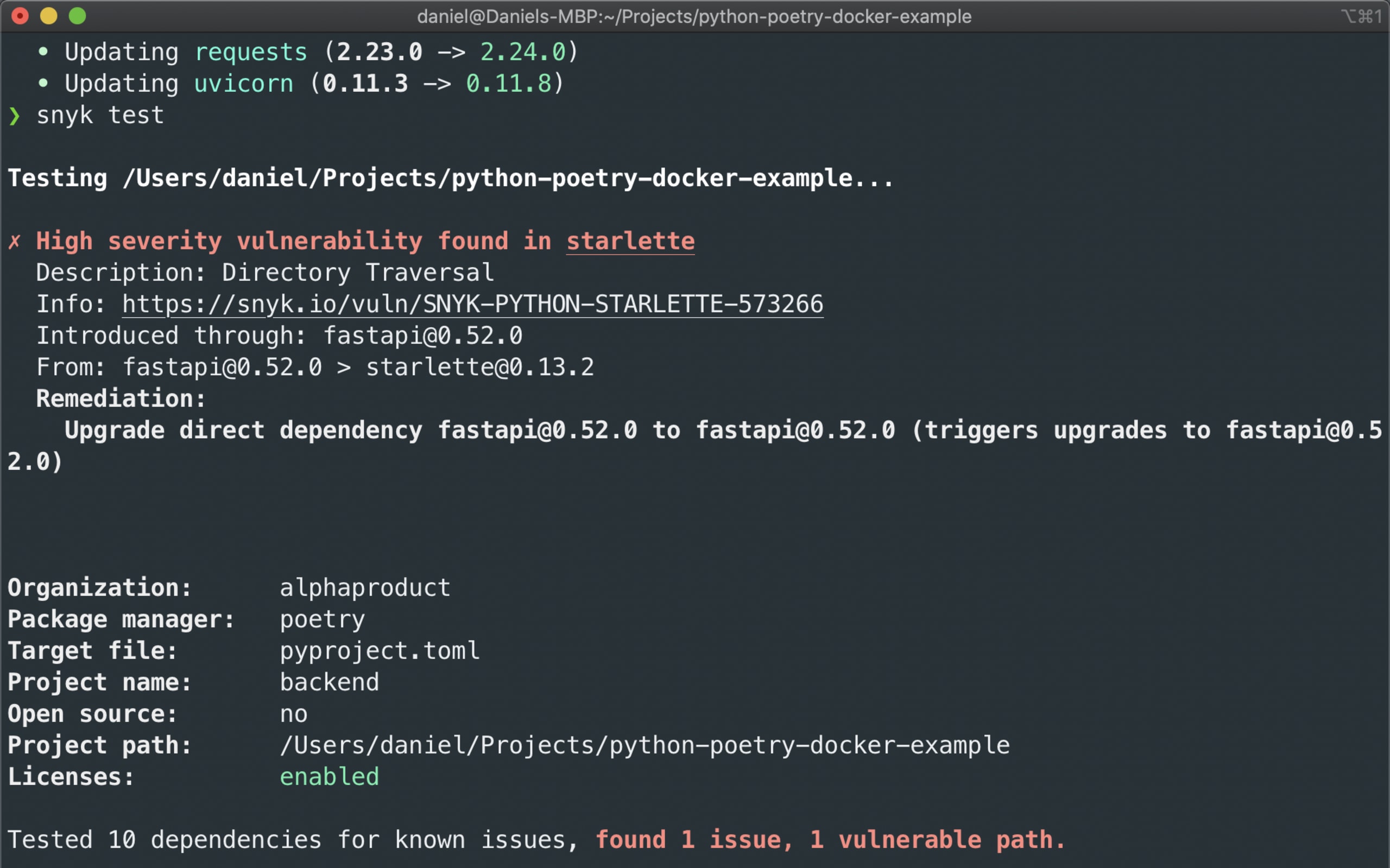
Scanning a Poetry project in the Snyk CLI
Golang
Golang has seen exponential growth over the past few years and is also a favorite among Snyk users. In 2020, we invested in improving both performance and coverage for this language. Moving to depGraphs dramatically enhanced the scanning experience for Go projects, enabling the super-fast scanning of large projects such as Kubernetes! Support for Go Modules projects, already available for CLI scans, was extended to cover our Git-based SCM integrations. We also did some work to enable vulnerability detection in Go containers.

Kubernetes and Terraform
Snyk released our 3rd official product in 2020: Snyk Infrastructure as Code (Snyk IaC) and with it, the ability to scan your deployment configurations while they are still in code so that when you are ready to deploy you know the objects you create are well-configured. With increasing numbers of applications and cloud infrastructure being defined in declarative manifest, we see more developers being tasked with making sure their applications and services are secure. And since changes can be made every time code is committed, the only way to scale is to build security into the pipeline to find and fix issues prior to deployment.

3. Prioritizing your vulnerability backlog
Vulnerability backlogs tend to quickly pile up into thousands of issues. It’s impossible, and usually unnecessary, to tackle each and every one of these issues. But where does one start?
That’s why we placed a huge focus this year on helping development and security teams decide where best to focus their efforts for the best security impact. To this end, we introduced a long list of developer-first prioritization capabilities that provide these teams with the security tools and context needed to sift through their issues and prioritize fixes effectively.
Priority scoring
Snyk’s brand new Priority Score is an advanced, built-in scoring system powered by a proprietary algorithm that processes a wide array of factors, such as CVSS score, the availability of a fix known exploits, how new the vulnerability is, and whether it is reachable or not. The resulting score is displayed on the individual issue cards within the Snyk UI and can be used to quickly filter and sort through the backlog.

Reachable Vulnerabilities
Reachable Vulnerabilities is an advanced analysis tool that provides application-level context on vulnerabilities and helps you determine whether a vulnerable function is reachable as part of the application’s execution path. Snyk users are already using Reachable Vulnerabilities to drive their fix decisions for their Java maven and Gradle projects and we will be expanding support for additional ecosystems next year.

Exploit maturity & relative importance for Linux vulnerabilities
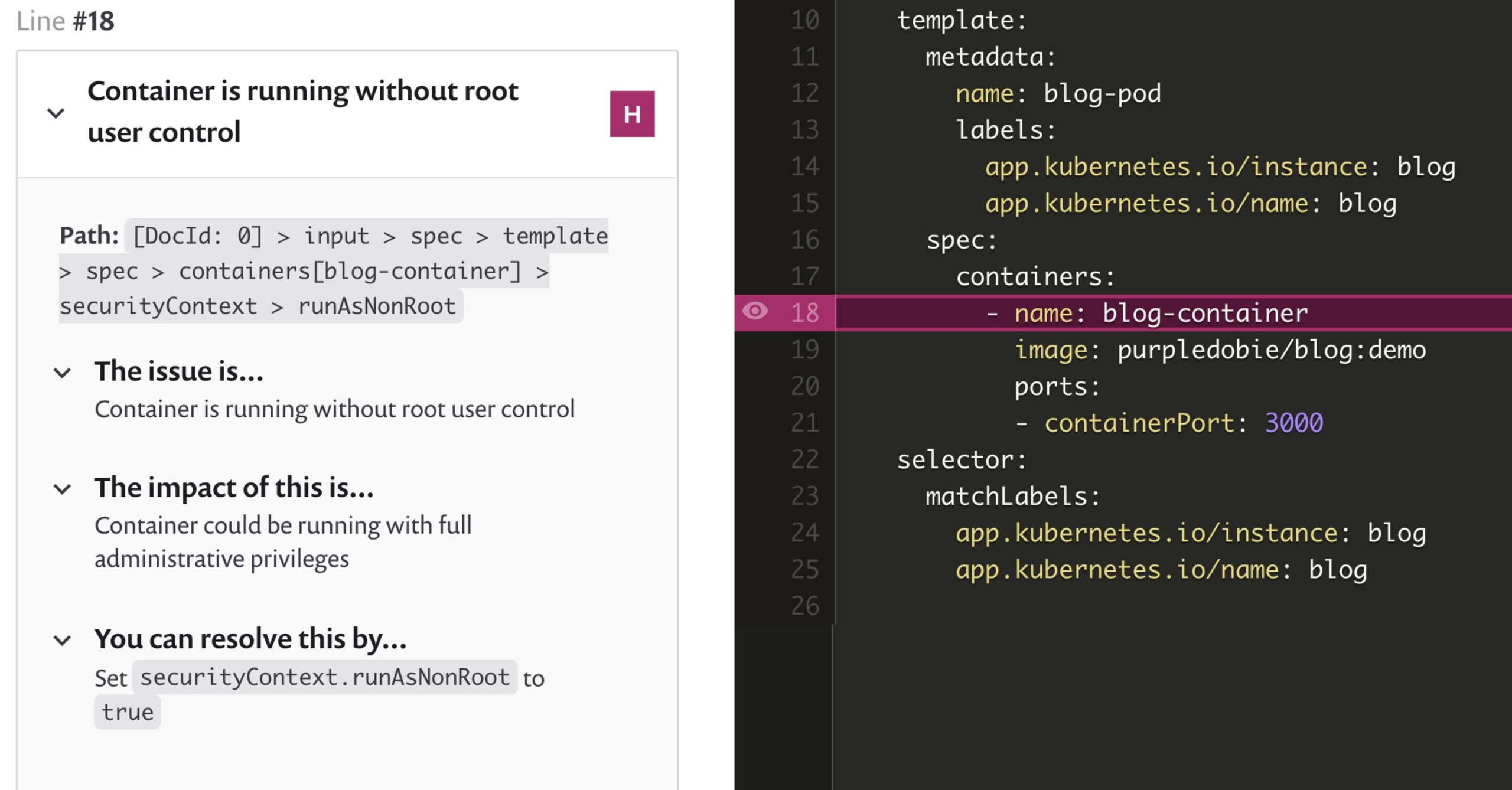
The priority scoring feature works with Snyk Container, too, and takes into account additional container-specific details. For example, if a vulnerability has a mature exploit and it’s actively running in a Kubernetes cluster, your priority score goes up. If the Kubernetes pod is configured in such a way that risk is increased, such as running the container as root, that is factored into the priority score, too.
In addition, vulnerabilities in Linux packages sometimes vary based on the particular Linux distribution you elect to use in your container images. What starts out as a high-risk vulnerability in a Linux package, might be considered a low-severity item in a particular distribution like Debian or Ubuntu. Snyk takes both ratings into consideration but considers the maintainers of a distribution to be the authoritative source, and so we assign the distribution’s rating to the vulnerability (low, in this example).

Snyk Container with distribution-specific security details
4. Fixing more issues, more easily, and with more confidence
There are plenty of tools that will scan your code for issues. Helping you take action and remediate these issues is an entirely different story. Automated and actionable remediation is a core component of the Snyk platform and was naturally a focus area for Snyk’s product and development teams this year.
Keeping your dependencies fresh
In March, we announced a partnership between Snyk and Neighbourhoodie Software, the makers of Greenkeeper. This partnership enabled the graduation of Snyk’s Automatic Dependency Upgrades which automatically trigger actionable, context-rich pull requests when new versions for dependencies are identified, and help developer keeps their projects healthier and more secure.
Merging fixes with confidence
To help developers merge Snyk’s fix PRs more confidently, we introduced Merge Advice—a new badge that is added to pull requests and that indicates whether or not the fix is likely to result in any breaking changes. This gives developers the intelligence they need to decide whether or not to merge.

Skipping Snyk’s PR test
Snyk will automatically execute security and license testing for any new pull request opened by you or any other contributor in a GitHub repository. To minimize disruption to the development workflow, we added the ability for developers to see the full details on why their pull request failed and subsequently request the administrator to skip the test and “force pass” the pull request.
Infrastructure as code guidance
Snyk IaC provides a unique interface to display and instruct users on how to fix IaC issues. What we’ve found in our talks with customers is that IaC is an area many organizations are still in the early stages of formalizing. There is a mix of skill levels, and particularly when it comes to security issues, many users need additional guidance. At the same time, IaC issues are not all vulnerabilities, in the classic sense, so even if you had the time to research issues, you can’t always turn to something like the NVD to look up an issue and references. So, we built additional guidance into Snyk IaC to provide context and impact assessments to issues that are raised.
5. Managing security and compliance, at scale
When managing application security programs for thousands of applications and projects, organizations require ways to maximize efficiency and productivity. As such, in 2020 Snyk invested in supporting governance at scale and introduced a number of key capabilities across Snyk Open Source, Snyk Container and Snyk IaC.
Security and license policies
To help organizations more easily control security and compliance across their different projects and teams, Snyk introduced a new policy engine that enables the definition, customizations, and appliance of both license and security policies.
Using license policies, organizations can define accepted legal boundaries and enforce these across the board. Snyk’s license policies also allow controllers to add actionable legal instructions for the developers to use if faced with a specific license issue.
Security policies enable you to set in place rules for automatically prioritizing and de-prioritizing vulnerabilities. Each policy contains a rule, or a set of rules, that define exactly how vulnerabilities should be handled. Rules trigger actions based on conditions. Currently, rules can change the severity for vulnerabilities based on their type (for this we use CWE—a common standard for categorizing vulnerabilities based on common characteristics) and Exploit Maturity. A policy might contain one rule, for example, raising the severity for all XSS (cross-site scripting) vulnerabilities and with mature exploits and another rule lowering the severity for RCE (remote code execution) vulnerabilities.

Project management
When trying to manage thousands of different projects, each with thousands of security issues, it’s easy to become overwhelmed. Even finding a project can become a more difficult task, not to mention understanding whether the project is among those that need your urgent attention.
Snyk’s Project Attributes and Project Tags help you organize your Snyk projects (Snyk Open Source, Snyk Container, and Snyk IaC) in a standardized way by associating business impact and tech stack metadata to them. This makes it easier to search and find projects, as well as focusing your efforts on specific projects based on their deployment environment, lifecycle stage, priority score, and any other characteristics that are important to your organization.
Backlog Management
Backlog Management, announced during SnykCon just a few months ago, opens targeted fix pull requests to fix vulnerabilities in your backlog based on their priority score. This enables you to reduce your vulnerability backlog at a more manageable pace.
License compliance management
The open source dependencies you pull into your project pose both a security AND legal risk. This year, we announced Snyk’s developer-first license compliance management capabilities, enabling you to manage and comply with the open source licenses you are using more easily.
Snyk goes both wide and deep with license compliance management by integrating across the SDLC (CLI, IDE, SCM, CI/CD) and by providing the ability to detect licenses in both direct and transitive dependencies. All of the most popular programming languages are supported, including, in no particular order of importance of course—Java, JavaScript, Scala, Go, Python, Ruby, PHP, Swift, Objective-C, and .NET.
Flagged license issues are displayed with the full context needed by developers to help them gauge the scope of the issue and take action, including detailed legal instructions specifying the next steps to be taken in order to comply with company policy. A variety of dashboarding and reporting capabilities provide controllers with the ability to view and share detailed lists of licenses being used, including a BoM report that lists all the open source components and licenses along with copyright information.
Looking into 2021 (spoiler alert!)
As much as 2020 was packed with Snyk product goodness, wait for what we’ve got in store for 2021!
Snyk’s core themes—developer-friendliness, automated and actionable remediation, and security depth - will all continue to play a key role in upcoming announcements. We will be adding support for a very important ecosystem and will be reinforcing some of the unique capabilities making Snyk the leading cloud native application security solution on the market.
Wishing us all a happy and healthy new year!
