Recursos





Mostrando 553 - 576 de 632 recursos
7 Best Practices for Static Application Security Testing
Static application security testing (SAST) plays a pivotal role in ensuring application security by detecting vulnerabilities in source code prior to compilation and deployment. Download this cheatsheet and learn how to streamline your security workflow.
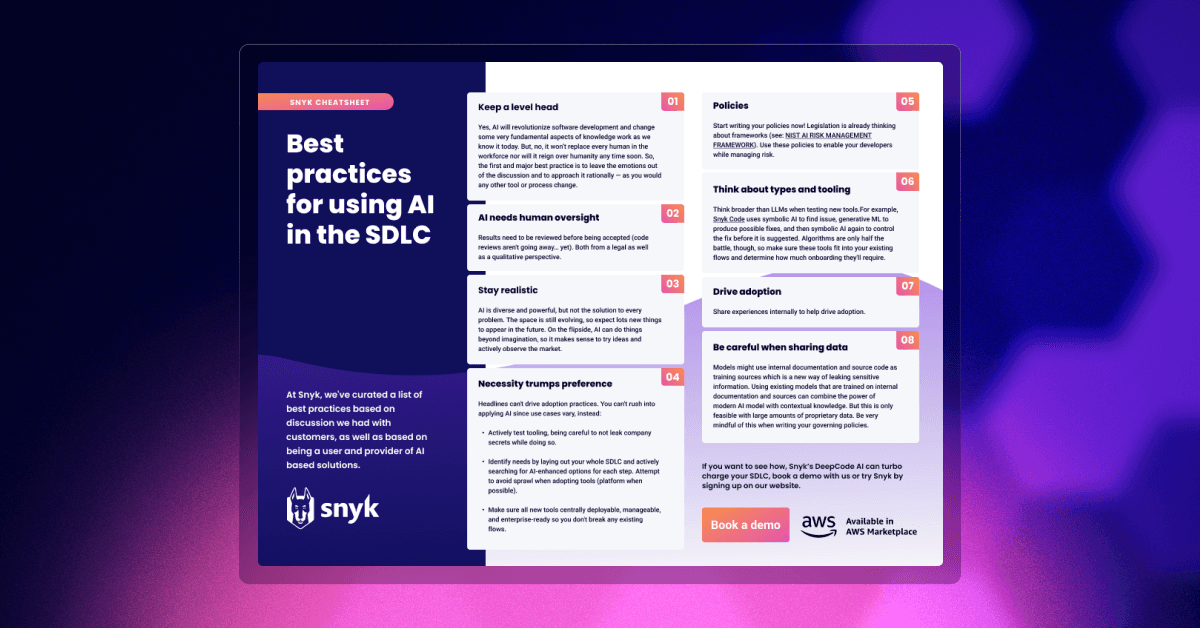
Best Practices for AI in the SDLC
AI has become a hot topic thanks to the recent headlines around the large language model (LLM) AI with a simple interface: ChatGPT. Although there are many efficiencies gained when AI is used in the development process, there are new security threats that are introduced. Download this cheatsheet today to learn best practices for how to leverage AI in your SDLC, securely.
6 Steps for Scaling Risk-Based AppSec Programs
Looking to strengthen your application security posture at scale? Learn how to define, manage, and scale your application security program with end-to-end visibility across your applications, coverage, and governance through these 6 key steps.