Add security testing to pull requests in Azure Repos
Edward Thompson
6 mai 2019
0 minutes de lectureThis post highlights best practice #7 — add security testing to PRs — from our series of 8 security best practices for Azure Repos.
Adding security testing to pull requests in Azure Repos
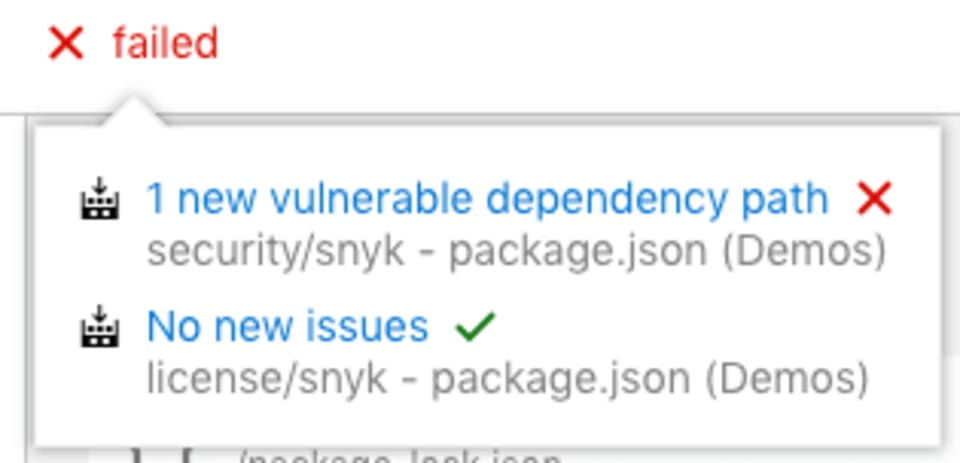
By adding Snyk’s native integration with Azure Repos, each pull request will be tested to ensure new vulnerabilities aren’t introduced into the code base. Policies can be defined to configure the severity level of a vulnerability that fails the merge. The following image displays a failed PR due to new vulnerabilities that it would have added:
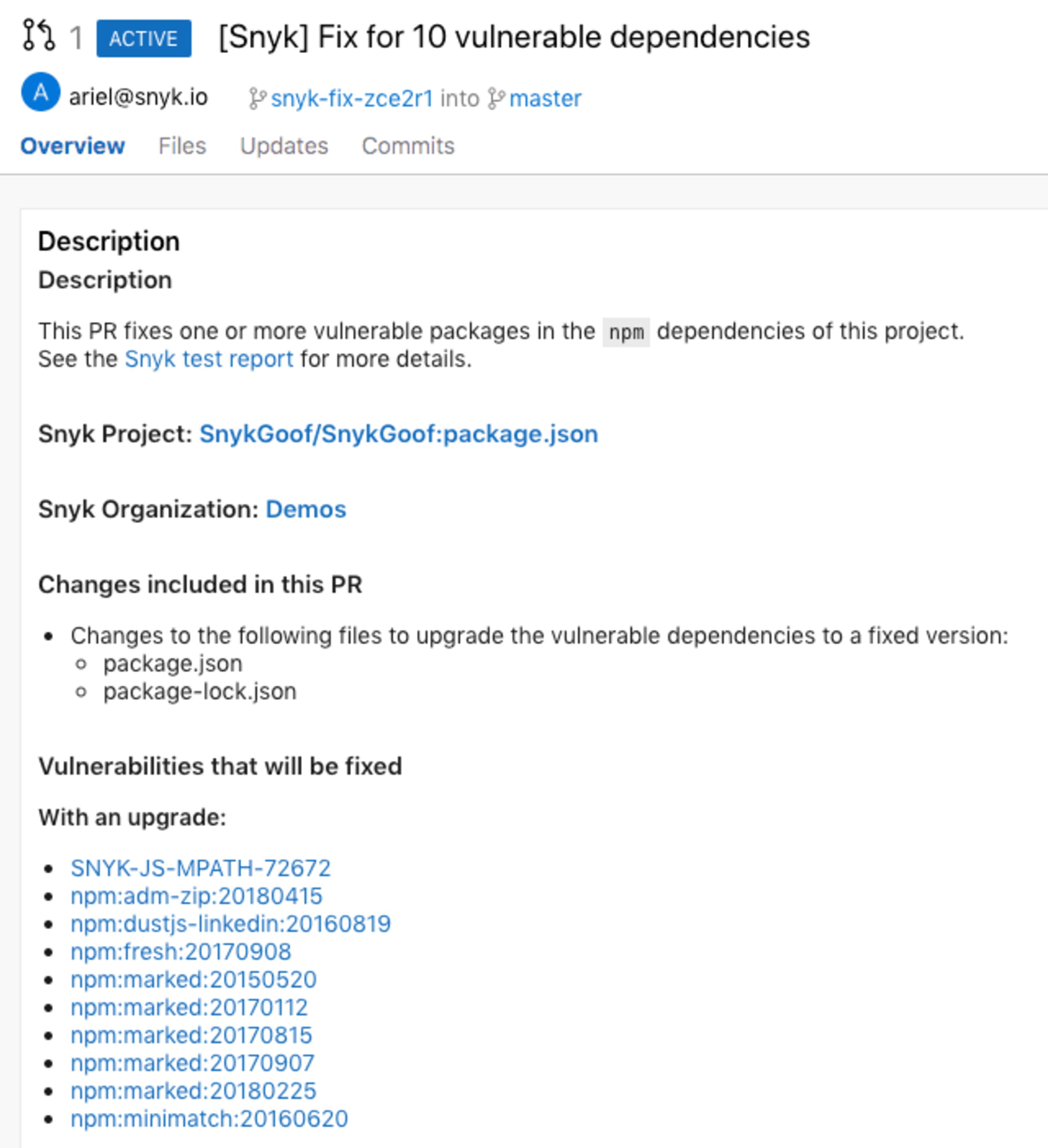
If Snyk finds a vulnerability it provides developers with the needed tools in order to triage and fix the vulnerabilities. Snyk calculates the required fix for both direct and transitive dependencies and automatically populates a fix pull request with the required upgrades or patches, all from within the Azure Repos workflow. The following image displays a fix PR created by Snyk.
* The functionality of Fix PR and testing new PRs is in closed beta. Please contact us if you would like to join it.
Continue reading the list of 8 security best practices for working with Azure Repos:
If you haven’t done so yet, make sure you download this cheat sheet now and pin it up, so your future decisions are secure decisions.