Tools for infrastructure drift detection
William Beuil
15 de março de 2022
0 minutos de leituraAviso de descontinuidade Detecção de desvios em recursos gerenciados
A detecção de desvios em recursos gerenciados, incluindo snyk iac describe --only-managed and snyk iac describe --drift, foi descontinudada. A data de fim de vida útil da detecção de desvios de recursos gerenciados foi 30 de setembro de 2023.
Predicting infrastructure drift is like predicting snowfall in winter… you know it will happen at some point but you can't predict exactly when. And just like snowfall, having a way to detect it as early as possible is what will make you the most prepared and your infrastructure more secure!
In this article, we’ll explore the principles of drift detection, the different kinds of drift and why they happen, and tools to help detect drift with a simple example.
What is drift detection?
To understand the need of a drift detection tooling, you need to get your head around what is infrastructure drift. In brief, you can think of it as a deviation of your whole infrastructure from your configuration file.
For the sake of this blog post, we’ll focus on Hashicorp Terraform as our infrastructure as code (IaC) software tool to deploy our cloud resources. Within the Terraform world, drift or the deviations of your infrastructure is when your state file differs from what you have applied in your cloud provider.
This is where proper tooling to detect those drifts can significantly improve your security posture — imagine a perfect world where you get alerts if someone manually changes your security group instead of using Terraform. Also, wouldn't it be awesome to have alerts on newly created resources outside of your Terraform?
Managed vs. Unmanaged resources
To illustrate my perfect world above, we will differentiate between two kinds of drifts:
Drifts on resources managed by IaC
Since we do have the configuration file and state files of all resources applied and deployed to your cloud provider, your IaC tool is usually well served to help you on this task of detecting changes made outside of it or not yet applied.
Drifts on resources unmanaged by IaC
On the other hand, this type of drift is not easy to detect since your configuration or state file doesn't have those resources defined in the first place.
Why does drift happen?
Drift happens for so many obvious reasons but Hashicorp explains it better than anyone else:
"Within the context of your configuration, it happens when adding or removing resources or changing resource definitions. External to your configuration, drift occurs when resources have been terminated or have failed, and when changes have been made manually or via other automation tools."


Christie Koehler
Developer Advocate, HashiCorp
Let's take a look at real examples of two types of drift and their impact. A drift on a managed resource could be someone manually changing the versioning of your Terraform configured Amazon S3 bucket. Whereas, a drift on an unmanaged resource could be someone manually adding an S3 bucket outside of Terraform (e.g. in the AWS console). (See our previous article for tips to manage drift from manual changes.)
Which tools can help us detect those drifts?
Let's focus now on tools to help you detect drifts on managed and unmanaged resources. For the rest of this post, we will use the same simple Terraform example explained above:
We're just going to change in the console its versioning attribute to false to add drift to it. In addition, we're going to manually create the same S3 bucket on the AWS Console.
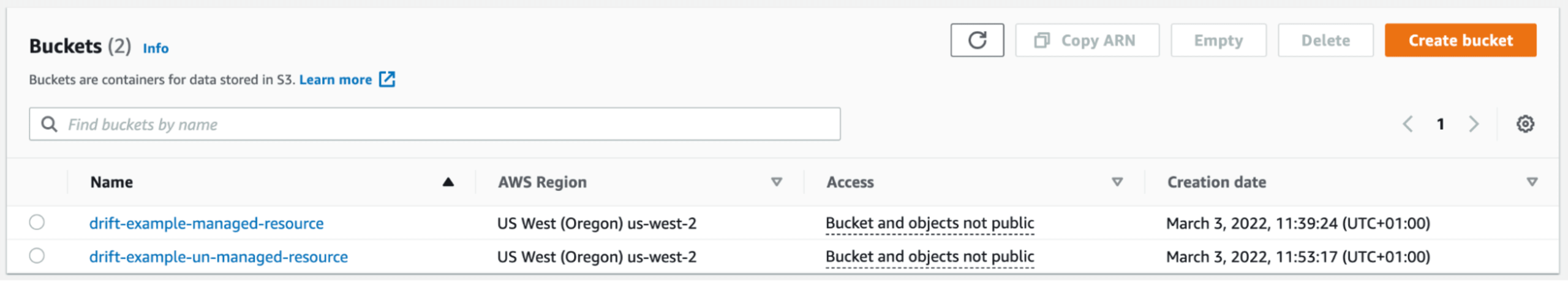
Now let's take a look at three tools for managing drift:
1. terraform plan
The terraform plan command is a simple description of what needs to be applied so that you end up with your desired implementation. Let's see the output of this command on our actual infrastructure:
Terraform says that it found a drift on its managed resource and explained what the change was (e.g. versioning from true to false). And after that, it outputs what it will do if we decide to apply the plan (e.g. versioning back to true).
Pros:
Consistent way to detect drifts on managed resources
Support all Terraform resources
Cons:
No way to detect drifts on unmanaged resources
Don't support plan on multiple state files
2. CloudQuery
CloudQuery is an open source cloud asset inventory powered by SQL. Basically, by default, they extract all your resources from your desired cloud providers, format, and load them into PostgreSQL. They create a drift detection command on top of it, so as to "turn this drift problem into a data problem," as they say.
Once the CloudQuery CLI installed, let's go back to detecting our S3 bucket drifts.
The first command, as explained above, fetches all my resources from my cloud providers and puts them in a PostgreSQL table.

This output is quite interesting, as we can see that he found both my S3 buckets, one managed and one unmanaged. In addition, it found that my managed bucket has drifted but the analysis is quite strange as it found that the S3 bucket is not versioned on AWS but unknown on my state file. Probably a bug in the way they look at Terraform attributes. The other drifted attributes make me wonder what would happen if I have a non-drifted managed bucket.
I re-applied my first configuration of my bucket with terraform apply and I tested again a cloudquery fetch and cloudquery drift scan --deep --debug terraform.tfstate:
CloudQuery still found that my bucket has drifted while changing in its data table the versioning status. This is clearly a false positive that should not be taken into account as my bucket on the AWS console has versioning enabled.
Pros:
Really fast enumeration of my cloud resources with the fetch command
Unmanaged resources detected with the simple drift scan command
Support scanning multiple state files
Cons:
Unreliable output for S3 bucket drifted attributes with the
drift scan --deep --debugcommandOnly support a few backends for storing your state files (e.g. S3 and locally)
Does not support all Terraform resources
Requires a SQL database
3. driftctl
driftctl is a free and open source CLI tool that warns of infrastructure drift. It helps detect, track, and alert on both managed and unmanaged drift. Let's test this with our example. Note:driftctl is Snyk’s own open source drift detection engine.
This output tells us that driftctl found our two resources. The managed one was found with a drifted attribute which is the versioning status and the other one is our unmanaged S3 bucket.
Pros:
Drifted attributes on managed resources detected with the
driftctl scan --deep commandDetects drift on unmanaged resources with the
driftctl scan commandSupport scanning of multiple state files
Cons:
Time to scan in
--deepmode could be really long since they list all resources of an account and fetch for each resource its detailsAPI throttling errors while scanning since they rely heavily on the cloud provider API to gather all information
Does not support all Terraform resources
Considerations for drift tools
These three tools are really good at what they're doing, but let's wrap up what makes them really shine in specific scenarios.
The terraform plan command is a really powerful tool to have and to use in a scheduled pipeline for all your state files. Indeed, not only do you get the benefit of having all their resources covered by the tool, you also have a universal way of presenting drifted attributes that is pretty easy to read. The only downside here is that you can't aggregate all your state files and run the command to check for drifted resources in one place. While reporting unmanaged resources is not the tool’s job, it’s an essential function.
As for the CloudQuery command line tool, results are mixed. On one hand, their enumeration command (fetch) is just an amazing piece of technology. Indeed, you get to have for free an open source alternative to gain deep visibility into your cloud infrastructure with SQL as their query and policy engine. On the other hand, their drift detection command is quite limited. From my tests, you can't rely on finding drifts on managed resources with it. In addition, you can only use this tool for finding unmanaged resources if you find yourself in a simple scenario: you can access your state file either locally (most of the time for testing the tool) or via an S3 bucket (best practice if you want to test it in a CI). Fortunately, their drift detection command is still in alpha, so I can't wait to see this command line tool growing.
With driftctl hooked into your CI and running on a daily basis, you get a continuous way to be alerted on drifts on managed and unmanaged resources. Its range of supported backends to store state files makes it a good candidate for most infrastructure. Furthermore, you can, just like CloudQuery, filter or ignore resources that you don't care about to have a report that fits your needs. One serious weakness due to the way driftctl was designed is that huge infrastructure can find a hard time running it smoothly because of API throttling. One last thing, the execution time in --deep mode could be annoying while testing locally for large infrastructure, in a CI pipeline it's less of a problem.
Last but not least — permissions. Both driftctl and CloudQuery don't need your Terraform code but only your state file to work, which is less cumbersome. They both respect the best practice of least-privileged permissions to scan your entire cloud provider, which means you only need a read-only policy to run both commands. This is not the case obviously for the Terraform command since it needs a read-write permission to create/update/delete your infrastructure and it must read your code to know what to deploy or remove.
Next up for the Snyk IaC
If you’re interested in bringing unmanaged resources under IaC control as well as detecting drift of your managed resources, Snyk is doing just this. Drift management in Snyk IaC helps you secure infrastructure faster by reporting issues and fixes direct to developers, in developer-friendly terms. By building a faster feedback loop between cloud security and development teams, developers will be empowered to own their Terraform from code to cloud and secure infrastructure configurations post-deployment. The second part of this is also surfacing unmanaged resources across cloud environments, so you can bring them under IaC control and reduce the risk of drift from the start.
Additional Resources for Drift Management
To continue learning about drift management in regards to Terraform we have a few more writings on our blog:
Infraestrutura segura desde o código-fonte
A Snyk automatiza a segurança e a conformidade da IaC em fluxos de trabalho e detecta recursos descompassados e ausentes.
