Scanning ARM templates for misconfigurations with the Snyk CLI
November 10, 2021
0 minutes de lectureManaging application resources at scale can be tricky business. As such, many DevOps and AppSec teams turn to using a declarative framework rather than writing individual scripts to deploy, manage, and maintain access controls for their resources.
For Azure environments, Azure Resource Manager (ARM) is this management layer that allows teams to manage their infrastructure as code (IaC) through declarative ARM templates. It enables teams to centralize the management, deployment, and security of Azure resources, and has increased in popularity over the years. From our latest State of Cloud Native Application Security report, over 30% of the teams reported they use Azure Resource Manager as their IaC tool of choice.
Given the massive popularity of ARM, we’re excited to announce you can now use Snyk Infrastructure as Code (Snyk IaC) to find and fix misconfigurations in ARM JSON files. By fixing these issues early in the software development lifecycle, security and developer teams alike can eliminate slow, manual code reviews or the tedious process of remediating a vulnerability much later in the process.
Let’s walk through some example workflows with Snyk IaC and ARM.
Using the Snyk CLI to scan ARM templates
For testing purposes, we’ve prepared this example repository which contains ARM template files in both JSON and Bicep format. You can then clone the repository and test the ARM files using the Snyk CLI.
To get started with the Snyk CLI, you can create a free account and then install Snyk CLI using npm. If you have Node.js installed locally, you can install it by running: npm install snyk@latest -g
If you are using Yarn: yarn global add snyk
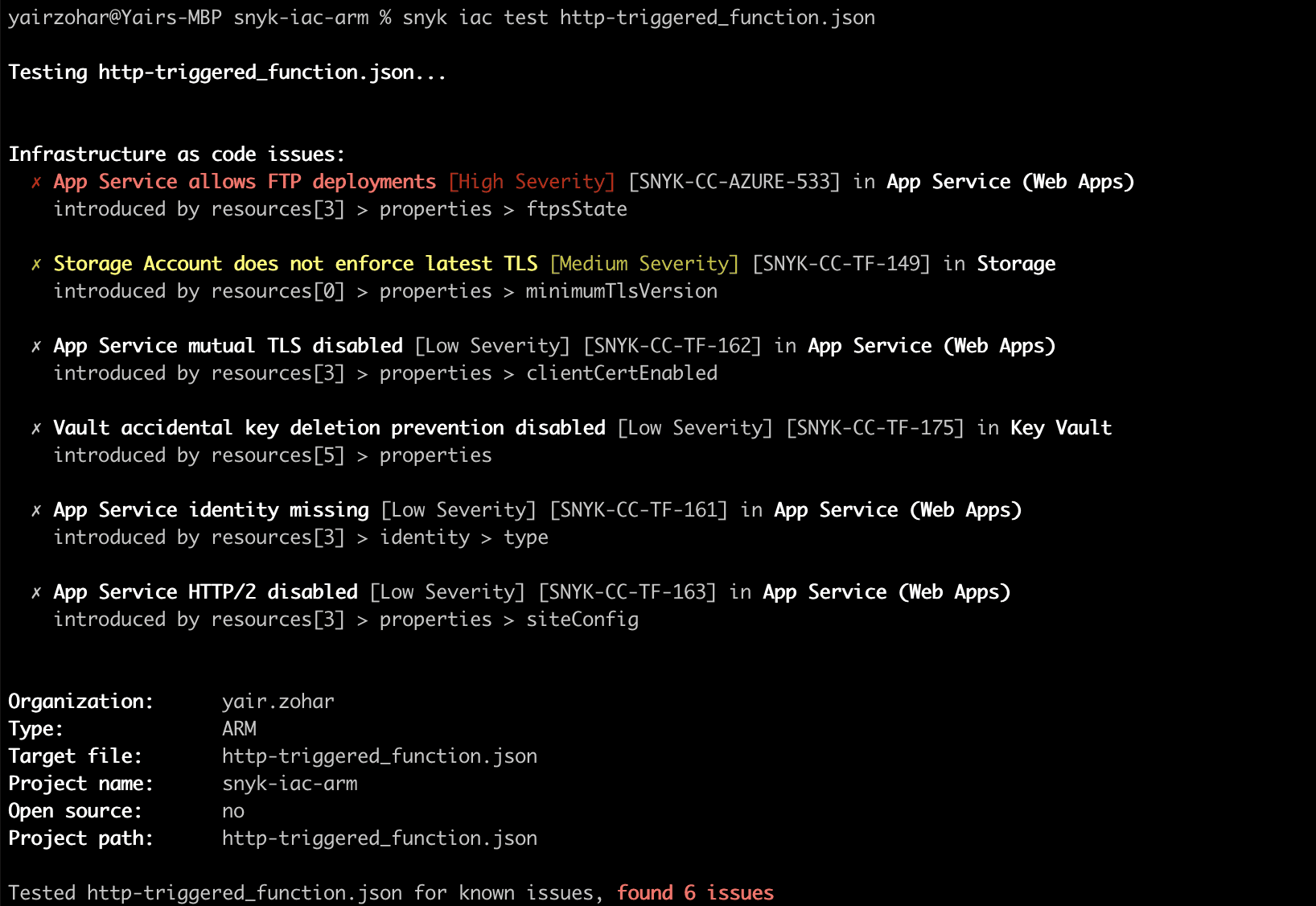
Identifying misconfigurations in ARM Bicep files
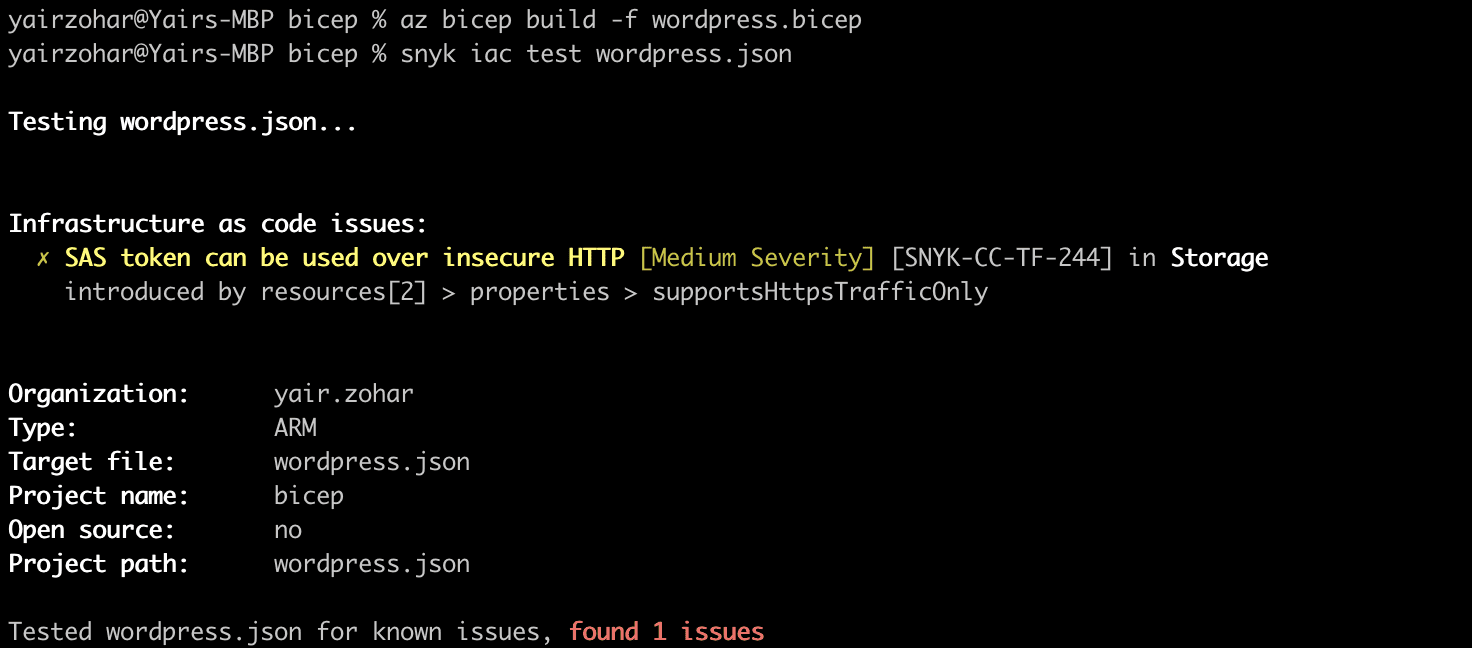
Bicep is a domain-specific language (DSL) that uses declarative syntax to deploy Azure resources. It provides concise syntax, reliable type safety, and support for code reuse. In addition to ARM JSON files scanning, you can also scan Bicep files by converting them to JSON by using the Bicep CLI.
First, make sure you have the Bicep CLI installed, then use the command az bicep build -f {file_name}.bicep to convert any ARM configuration file from Bicep format to JSON. Once you convert the file, you can simply scan it like any other ARM JSON file.
Leveraging Snyk’s configuration security rules
Of course, IaC scanning functionality is not enough. The depth and range of security rules are important to ensure you get comprehensive security feedback and catch misconfigurations before your resources are deployed. Snyk’s dedicated Security Engineering team researches, validates, and adds new rules — with over 100+ to secure your Azure environment (and growing).
Our Security Engineering teams combine known best practices with first-party research to continuously add new rules. Best practices are derived from both cloud provider and community standards, such as CIS benchmarks, and Azure best practices. On the security research side, we leverage threat modeling techniques on key usage patterns. For instance, we examine settings in managed Kubernetes offerings to determine where weaknesses might be avoided through proper IaC hardening.
You can view the Snyk IaC rules by navigating to your Snyk organization’s Settings and selecting Infrastructure as Code on the left-hand menu. If you want to narrow the view to just Azure, you can choose Azure from the tabs under Severity settings. We endeavor to write rules that are format agnostic, so most rules you see will appear no matter which toggles you select
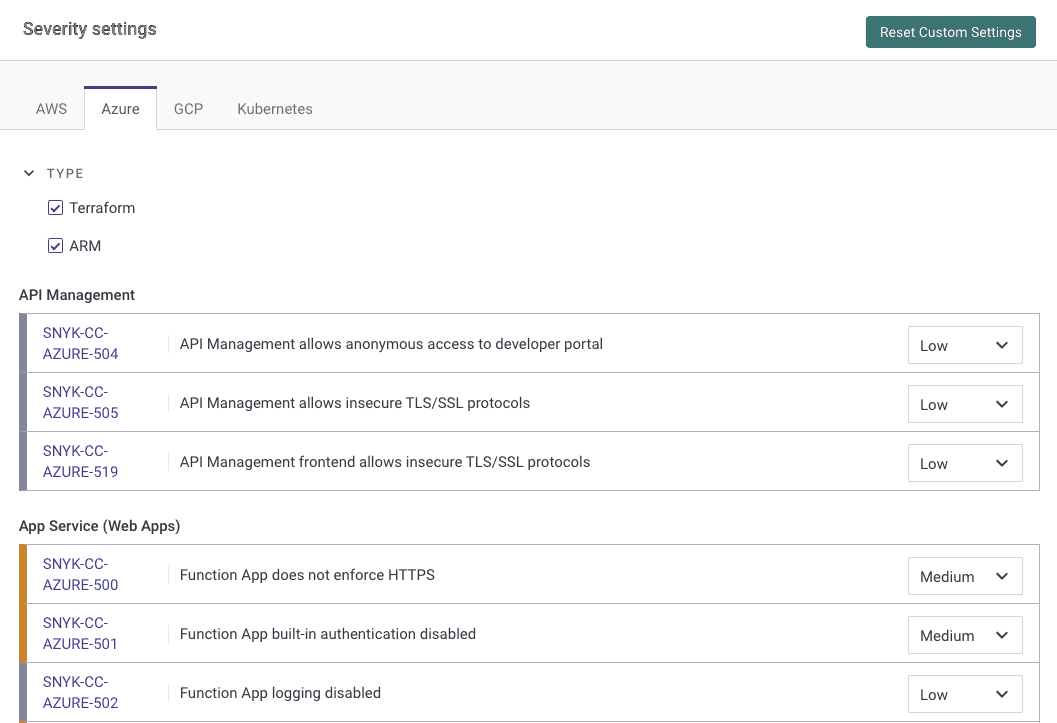
You can also view a full list of our ARM security rules publicly on the Security Rules section of our site.
Prevent ARM misconfigurations with Snyk IaC
These new features are available for everyone, including freemium users of Snyk. Getting started is simple:
Log in to your snyk.io account or sign up for free.
Verify you have the updated Snyk CLI (v.CLI 1.749.0) or install the Snyk CLI.
Scan your ARM files: You can get started with the main command to scan your IaC:
snyk iac test <path-to-file-or-folder>
You can learn more about the various scanning options we support through Snyk’s documentation or via the CLI documentation by running: snyk iac --help
If you have any feedback on how ARM support for the Snyk CLI is going for you, we’d love to hear it. Post any comments or feedback in the Snyk Community forum.
Une infrastructure sécurisée à la source
Snyk automatise la sécurité et la conformité de l’IaC dans les workflows, et détecte les ressources manquantes ou ayant dérivé.