IntelliJ plugin to fix vulnerable dependencies
October 2, 2018
0 minutes de lectureSnyk has now released an IntelliJ plugin that enables developers to find and fix vulnerabilities in their dependencies from right within their IDE!
As part of Snyk’s commitment to empowering developers to own security, a lot has been investedin making comprehensive Git integrations (with Github, GitLab, BitBucket) so that finding and fixing vulnerabilities happens as an integral part of the development process.
It has been a key part of Snyk’s success, as it enabled scanning every pull request as well as continuously monitoring any change in the code repositories.
We now want to enable developers to tackle vulnerabilities even before they check in their code, in the environment where they spend most of their time. Built to run inside IntelliJ and directly on the JVM, you can now have the Snyk open source security testing and actionable remediation advice without needing to step outside of IntelliJ - no Node installation required.
The plugin supports all Maven projects and is free.
Getting Started
The Snyk plugin is a standard IntelliJ plugin, a quick reminder on how it can be installed.
Navigate to IntelliJ IDEA > Preferences > Plugins.
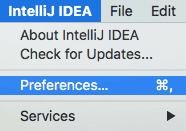
Search for Snyk and install the Snyk Vulnerability Scanning plugin:
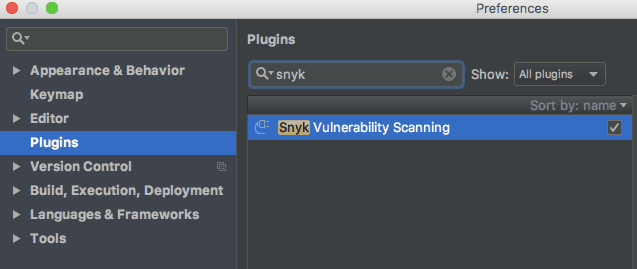
Then accept the privacy notices, restart IntelliJ IDE and the Snyk plugin will appear as a small tab on the bottom right.
You may need to login to Snyk through your GitHub account if you haven’t done so yet. Once done, you can easily choose which project to scan:
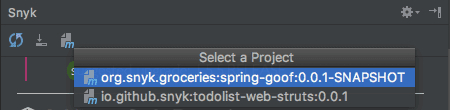
Finding and Fixing Vulnerabilities
Once a project is scanned, you’ll get a list of all the vulnerabilities that were found. Here’s an example from a simple spring demo application:
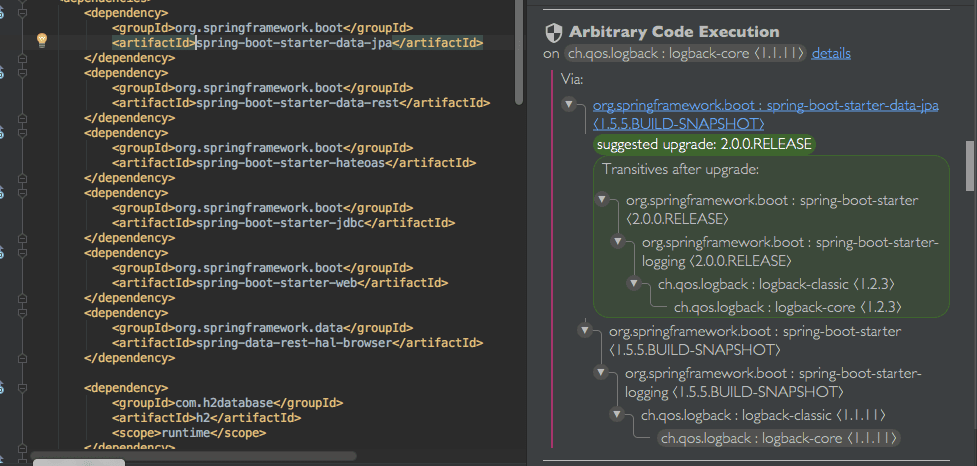
For each vulnerability, you can see the title with the type of vulnerability as well as a details link to gain more in depth details on the vulnerable version ranges, the way it can be exploited, etc.
You’ll see in gray the open source dependency that introduced the vulnerability, and do note that many times it may be a transitive dependency, as in the example below. You’ll be able to see the full dependency path that had led from the direct dependency you added to the vulnerable one (including all the packages on the way).
The Snyk IntelliJ plugin will provide upgrade recommendation (shown in bold green), which will be the minimal version you should upgrade to that will rid you of that vulnerability. Even cooler, you can see the full dependency tree as it will look once you upgrade (in the green box).
Clicking the direct dependency will take you right to the place in your pom.xml where it’s defined, and then you can easily apply the upgrade.
More to come...
We plan on adding support beyond Maven also to Gradle and Sbt at first, as well as supporting additional IDEs you may be using. We also assume we’ll be getting feedback from our beloved community, which we’ll bake in as well. Happy coding!
Assurez la sécurité de vos dépendances open source
Snyk fournit des PR de correction en un clic pour les dépendances open source vulnérables et leurs dépendances transitives.





















