Recursos


Mostrando 433 - 456 de 580 recursos
How to respond to a newly discovered vulnerability
Learn how to effectively respond to newly discovered vulnerabilities with a structured approach using the Vulnerability Management Cycle. Discover the importance of tools like Snyk for centralizing, analyzing, and remediating vulnerabilities across your software development lifecycle.
JavaScript Static Analysis with ESLint and Biome
Biome, a new tool in the JavaScript ecosystem, combines code formatting and quality linting. It offers speed and performance advantages over traditional tools like ESLint and Prettier, making it a compelling alternative. With its integration into development environments like VS Code and potential adoption by major projects, Biome is poised to reshape the way JavaScript developers approach code quality and formatting.
Oops I built a feature and created an Open Redirect Vulnerability in a Deno app
Build your first Deno web application with a step-by-step guide. Learn how to implement a redirect feature while avoiding common security pitfalls like open redirect vulnerabilities. Secure your Deno app with best practices and discover how to set up a Deno development environment in GitHub Codespaces.
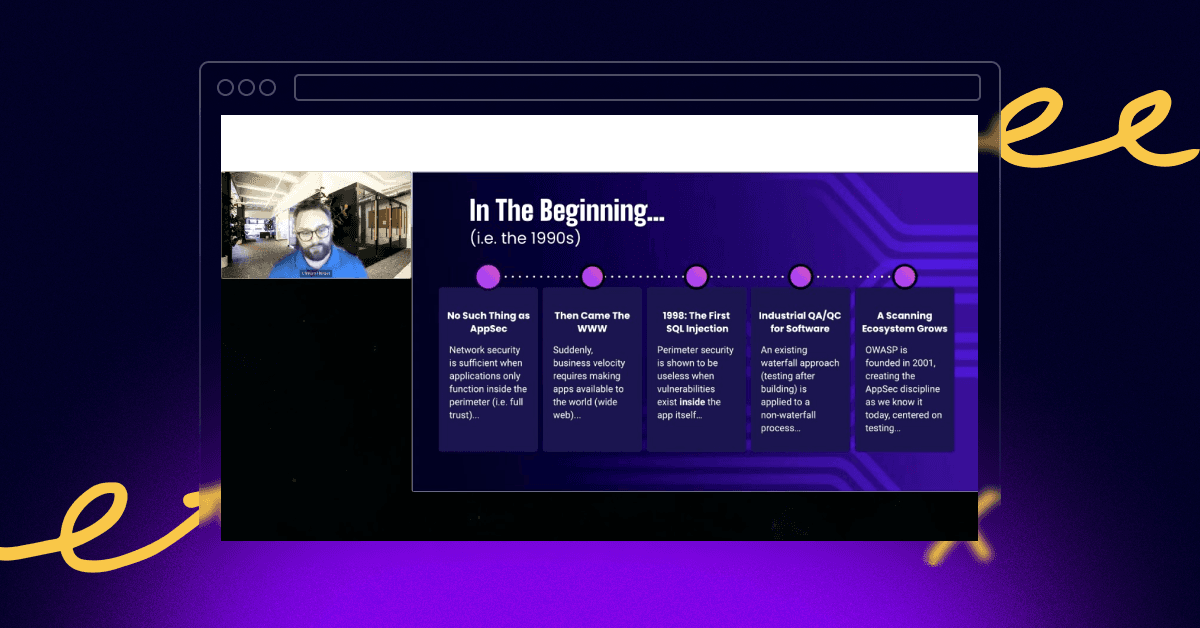
How Snyk Helps with the OWASP Software Assurance Maturity Model
Read how the OWASP Software Assurance Maturity Model (SAMM) and Snyk can work together to provide an effective approach to measuring, managing, and improving your software security. Learn about the key benefits, practical implementation steps, and the specific tools offered by Snyk to support your organization's security journey.