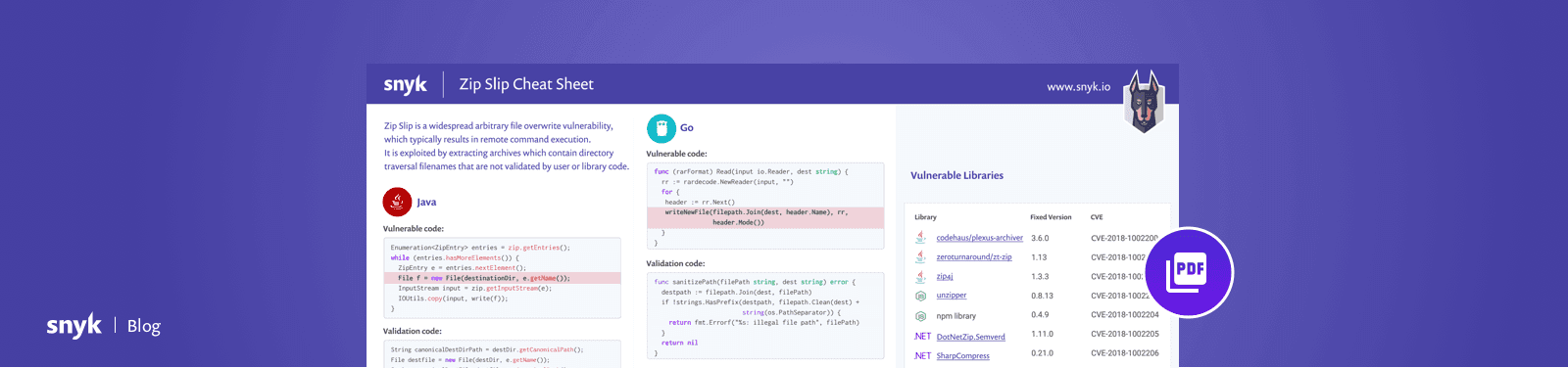
Zip Slip Vulnerability Cheat Sheet
28 de junho de 2018
0 minutos de leituraFollowing our last two cheat sheets on Local Type Inference in Java and GitHub Security best practices, I’m pleased to continue our series of handy, printable, cheat sheets with a more specific security vulnerability that has affected many thousands of applications. This month’s cheat sheet focuses on the Zip Slip vulnerability. On 5th June 2018, after months of research work with many very well known archive management libraries and projects, we publicly disclosed an Arbitrary File Overwrite vulnerability, dubbed Zip Slip. The vulnerability has manifested itself many times over several decades, but recently has become much more prevalent in high profile codebases across many ecosystems.
Zip Slip is a form of a Directory Traversal that can be exploited by extracting files from an archive. The premise of the Directory Traversal vulnerability is that an attacker can gain access to parts of the file system outside of the target folder in which they should reside. The attacker can then overwrite executable files and either invoke them remotely or wait for the system or user to call them, thus achieving Remote Command Execution on the victim’s machine. The vulnerability can also cause damage by overwriting configuration files or other sensitive resources, and can be exploited on both client (user) machines and servers.
To see an example exploit of this vulnerability, watch the short video below showing how sensitive files might be overwritten, leading to Remote Code Execution [embed]https://www.youtube.com/watch?v=l1MT5lr4p9o\[/embed\]This cheat sheet covers four of the main ecosystems that were most affected by the Zip Slip vulnerability. For each ecosystem, we show example vulnerable code snippets, followed by validation code that can fix this issue. Rather than duplicate here all of the content we put together about this vulnerability, it’s better to direct you straight to our research and GitHub repo:
Zip Slip Research page - Contains background information about Zip Slip as well as information about Directory Traversal attacks in general. Covers what an exploitable application flow might look like, and what you can do to see if you are vulnerable. Also looks through example vulnerable code snippets for all ecosystems we researched as well as suggested sample validation code.
Zip Slip Community repo - For the latest status on Zip Slip-vulnerable libraries, or to contribute by adding or updating vulnerable codebases, head on over to our community GitHub repo and submit a PR!Snyk helps you find and fix known vulnerabilities in your dependencies.
To get started for free, sign up for a free Snyk account and test your application to see if you’re vulnerable to Zip Slip or any other known vulnerabilities.