Snyk transformed cloud security in 2022 with developer-first solution
Lauren Place
11 de janeiro de 2023
0 minutos de leituraSnyk Cloud update
This blog has been updated to reflect Snyk Cloud’s renaming to Snyk IaC. All cloud-related capabilities are now included in Snyk IaC or the greater Snyk platform.
At Snyk, we’re best known for pioneering developer-first application security, empowering developers to find and fix vulnerabilities in their code early in the development lifecycle. We revolutionized the AppSec market by breaking down silos of tools, people, and processes between security and development teams by enabling security checks to happen from the moment code is written, versus the “deploy, detect, and respond” model used by many security tools.
And we realized that painful paradigm still exists for cloud security. The current generation of cloud security tools caters to IT security teams and still follows the same “deploy, detect, then respond” model to be used with IT-owned workloads and infrastructure. Silos exist between infrastructure as code (IaC), application, and cloud security tools. Fixes are often slow and frustrations run high because these cloud security tools catch issues too late in the infrastructure lifecycle and lack the ability to trace the cloud issues back to code (IaC).
Here at Snyk, we believe most modern, custom-developed apps should treat the cloud as code that controls the platform services integrated into those apps, so a developer-led security motion is best. This means securing programmable infrastructure (IaC and containers) pre-production and empowering developers to drive fixes at scale by enabling cloud fixes to be done in IaC —all with context from deployed cloud environments
In 2022, we completed our acquisition of Fugue and leveraged our new team members and technology to bolstering the capabilities of Snyk IaC. Snyk takes a developer-first, application-centric approach to finding and fixing vulnerabilities in cloud infrastructure from the time infrastructure is defined in code, through to when resources are running in the cloud. Let's dive into a recap of the exciting releases we’ve had over the past year…
Securing cloud infrastructure from the source
Empowering developers to proactively secure the cloud through code (IaC) is a key component of Snyk’s cloud security vision. And to accomplish this we needed to secure IaC from the start from the moment code is first written — the IDE.
In 2022, we introduced support for IaC security checks in our Snyk VS Code extension, Jetbrains, and Eclipse plugins, allowing developers to get fast, free, and actionable feedback for securing their code, open source dependencies, and IaC configurations from directly within their IDE of choice. Snyk IDE extensions support all Snyk IaC formats including Terraform, CloudFormation, ARM templates, and Kubernetes.
Also along the lines of our mission to help developers secure infrastructure earlier in the SDLC, we introduced our introduced our Terraform Cloud and Enterprise integration, enabling users to automate IaC security checks and enforcements with Terraform run tasks.
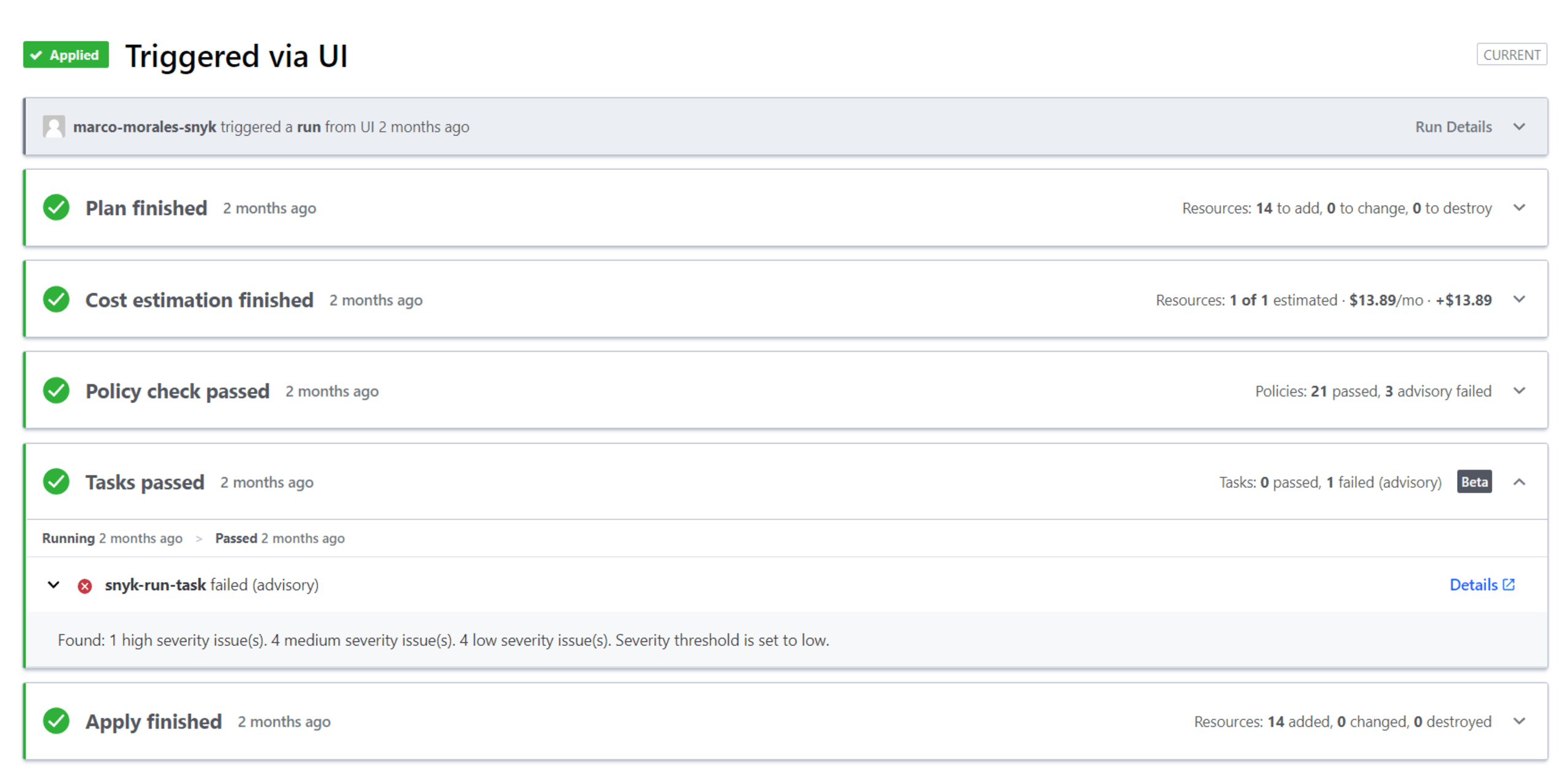
Unifying security across the SDLC, from code to cloud
Up until now, many organizations have had separate tools and processes around securing the cloud, applications and IaC. This creates challenges for developers and security teams, with conflicting results, required rework in managing them, and the lack of a single, consistent view of security posture across the software development lifecycle (SDLC).
Snyk IaC is powered by a unified policy engine for all IaC and cloud workflows, so security engineers can apply Snyk security rules once, and enforce them everywhere. Snyk’s unified policy engine is built on Open Policy Agent (OPA), with consistent checks of IaC and cloud configurations at every stage of testing whether it's in local development in the CLI/ IDE, automated scanning of Git repositories, testing, and gating in the CI/CD, or checks in your running cloud environments. For cloud environments, Snyk provides a quick and easy agentless onboarding with AWS and Google Cloud environments supported in the UI and API, and Azure support coming soon in the new year!
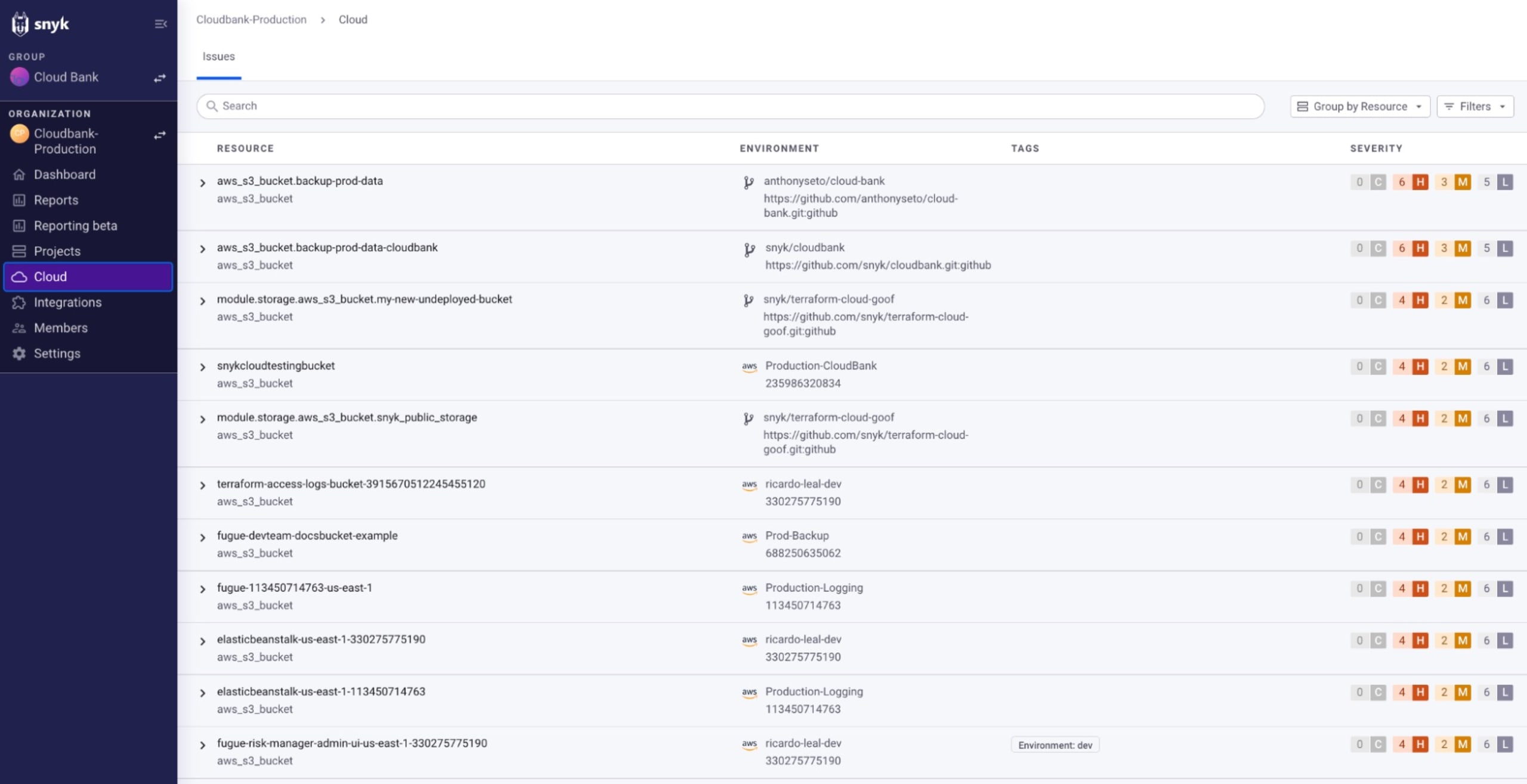
Snyk IaC also has unified, consistent interfaces for viewing issues, resources, and environments. Additional drill-down filters can help prioritize remediations and development efforts on the most critical issues whether it's filtering for a specific production environment or showing only critical_and _high severity issues.
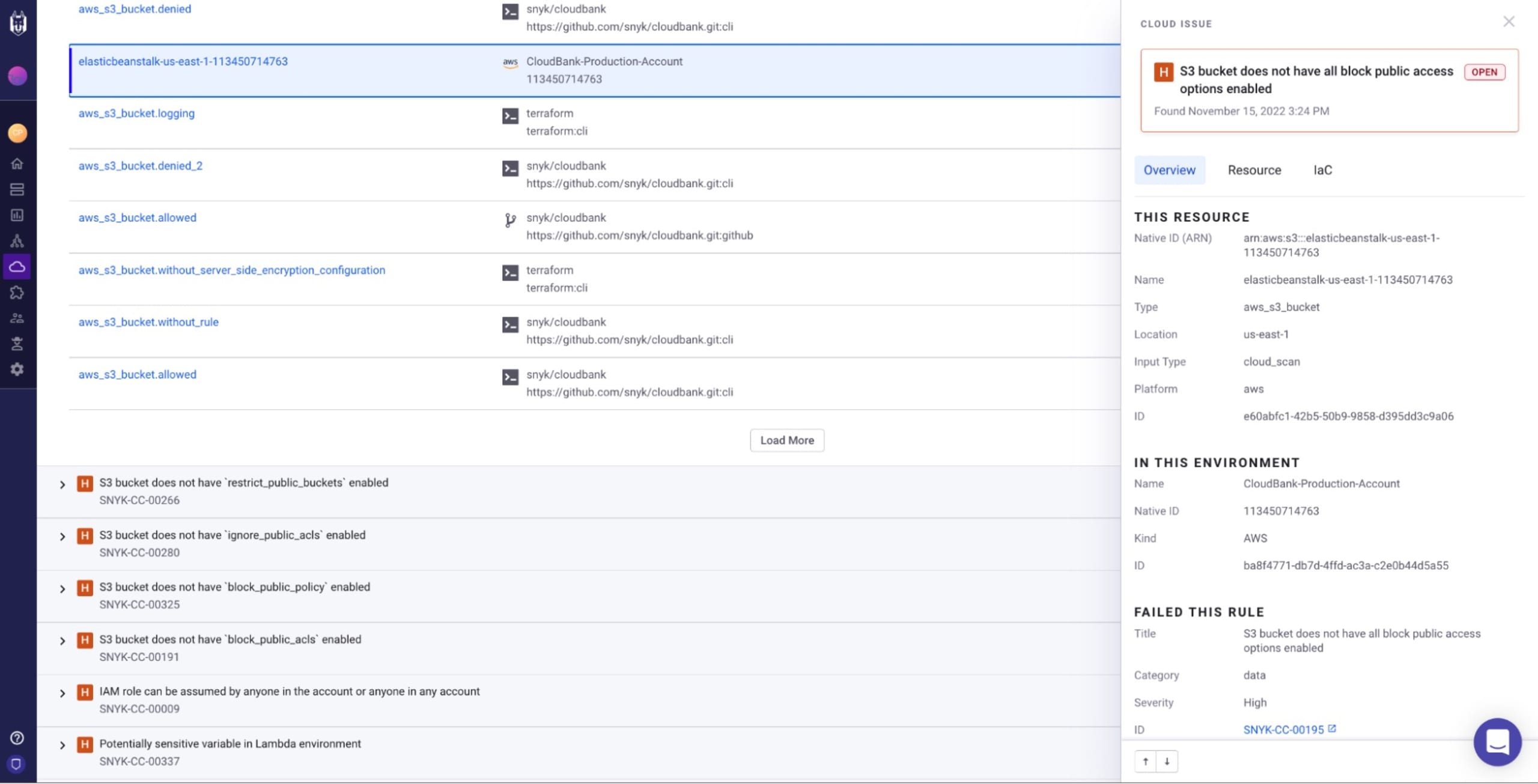
Bringing cloud back to code, providing context for developers
Visibility into the cloud is one important aspect of cloud security, but in the end, you are only as secure as the fixes you’ve made in code. So in 2022, we focused our efforts on bringing cloud context back to code, helping to contextualize and prioritize cloud issues for developers.
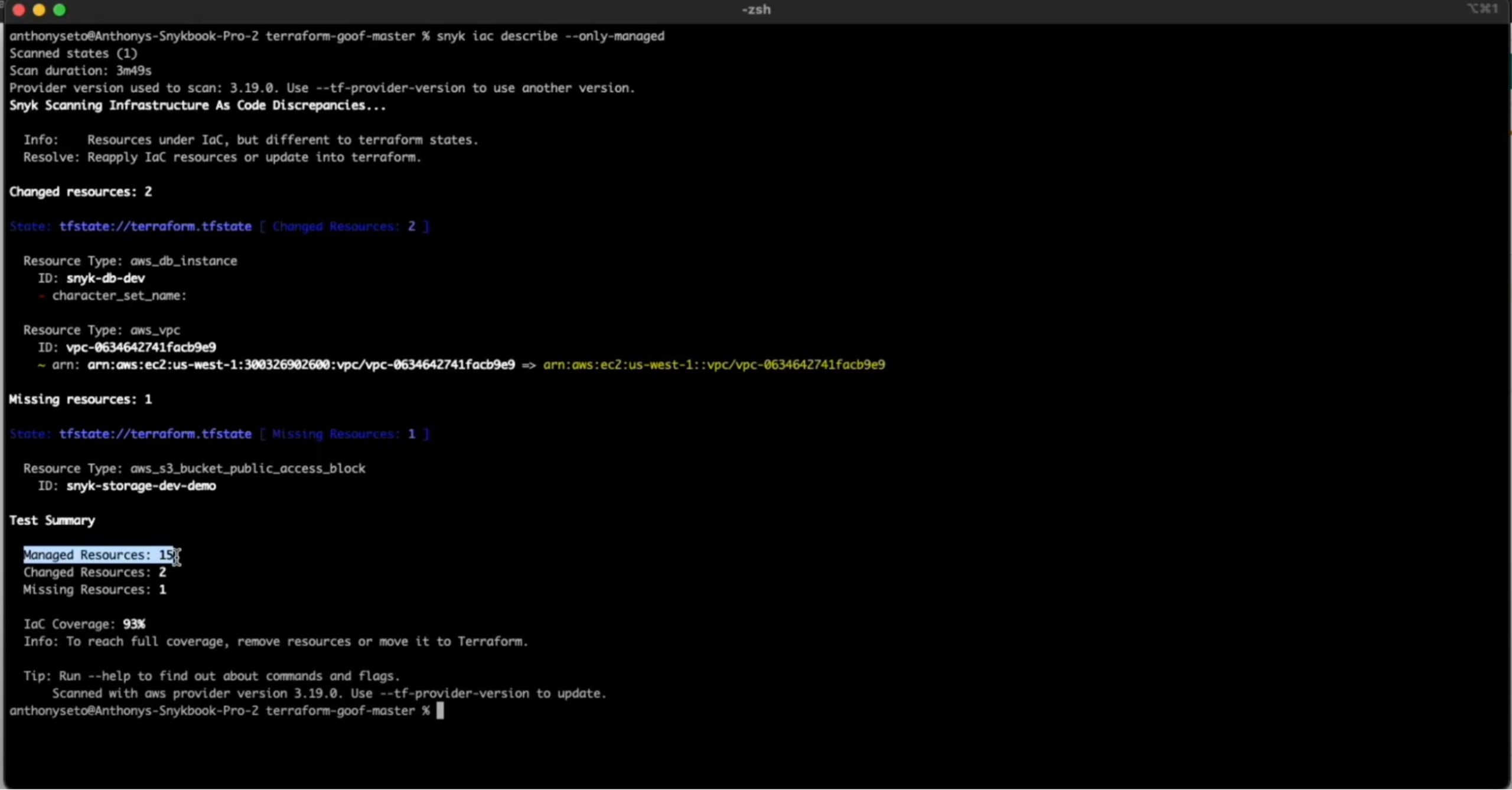
In May of 2022, we announced drift detection capabilities for Snyk IaC, enabling developers to identify configuration drift in their cloud environments. Leveraging the CLI, Snyk IaC uses read-only permissions to compare what's defined in IaC to resource configurations in the cloud. Snyk reports on:
Configuration drift: Cloud resources that were originally configured and deployed via IaC but have now deviated from their intended state (e.g. a bad actor or someone with access to change things directly)
Unmanaged resources: Cloud resources that are not defined in code and therefore are not subject to the same level of security feedback during the development process.
% of IaC coverage in your cloud environment:Total percentage of resources that are managed (and therefore held to security and compliance standards) by IaC
Traditional SAST and static analysis tools for IaC raise a large number of false positives, creating alert fatigue for security and platform development teams alike. In November of 2022, we also released cloud context for IaC issues to reduce false positives in IaC issues.
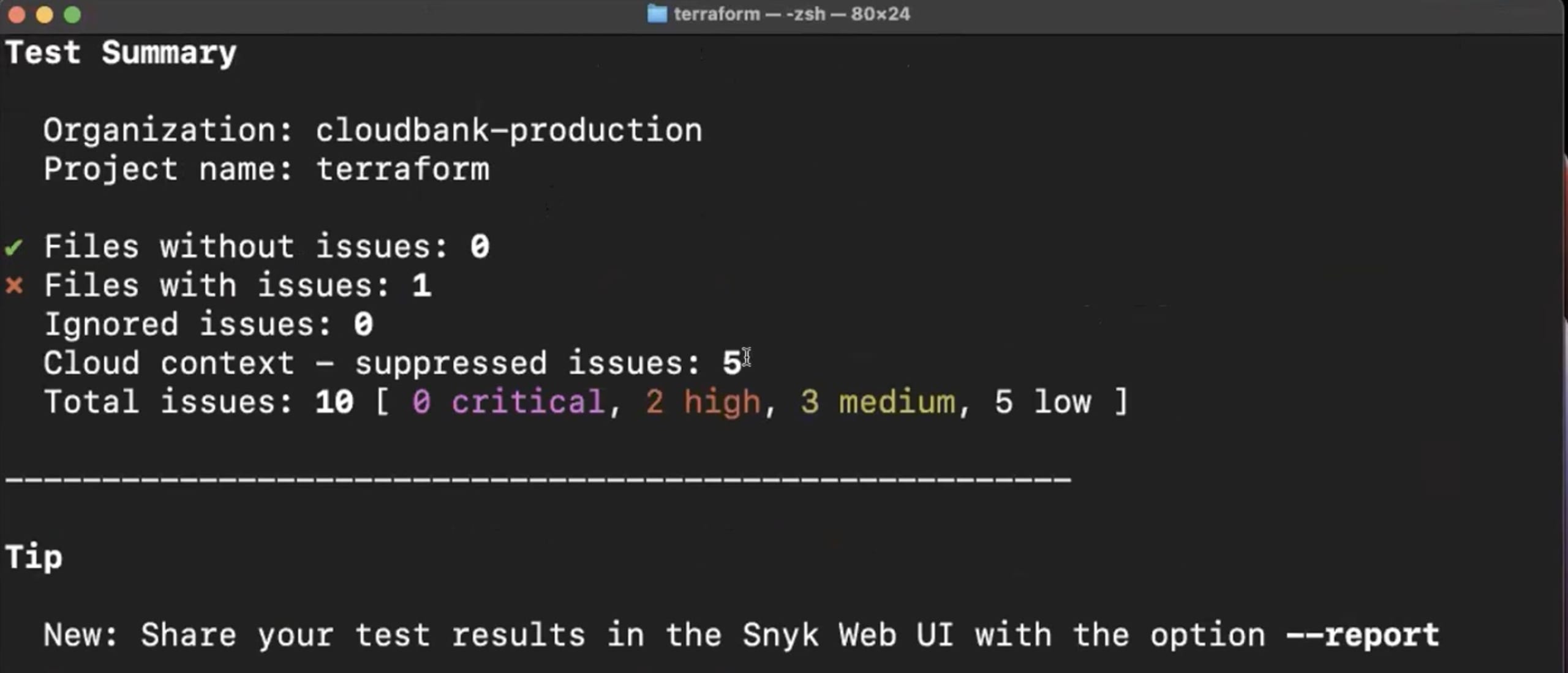
By connecting the cloud to code, Snyk’s unified policy engine will recognize and auto-suppress IaC misconfigurations that are already mitigated by cloud account settings. For example, if an issue is raised for a “publicly accessible S3 bucket”, but the AWS cloud account it is deployed to has restricted public access in its settings. Snyk will recognize this cloud context and auto-suppress the IaC issue so a false positive is not raised.
Looking forward to 2023
This year has been a monumental one as we continue delivering on our vision for a developer-led cloud security motion, and we’ve had a resounding amount of support and positive feedback from customers such as Tealium and Global Giving. The Snyk Platform in the future will combine full visibility of applications, infrastructure, and the running cloud throughout the SDLC— giving users one platform to identify areas of highest risk in the cloud to a vulnerability and deliver the fix in code to the right development team to make it go away.
In the first half of 2023, we plan on enhancing our capabilities to tie back cloud issues to the code assets that created them, enabling cloud security fixes directly in IaC, and enhanced drift detection reporting.
We will continue to build security and compliance posture views and reports to support security teams, as well as the ability to enforce security policies across the SDLC with custom rules.
For infrastructure as code specifically, we’ll continue strengthening our ruleset and engine’s filtering capabilities with greater support for Terraform workflows, new IaC formats supported, and cloud context-aware issues to minimize false positives and focus development times on just the critical alerts.
Thank you for your interest in Snyk, we hope you have a happy new year!
