New language-specific Snyk Top 10 for open source vulnerabilities
15 de março de 2023
0 minutos de leituraDevelopers use open source code because it facilitates fast development. In fact, the vast majority of code in modern applications is open source. But just like any other code, open source libraries are open to vulnerabilities that can negatively affect a wide range of end-user products. So with widespread usage of open source, it's important for teams to be aware of the risks that can be hidden in the libraries they use.
Start with the OWASP Top 10
The Open Web Application Security Project (OWASP) is an online community that provides free and open resources for web application security. Every few years, they release their OWASP Top 10 list of the most critical types of security vulnerabilities out in the wild. The list includes examples of weaknesses, how malicious actors can exploit them, and suggests methods to reduce or eliminate these vulnerabilities.
And if you hadn't seen, Snyk Learn recently released a OWASP Top 10 learning path, which is a collection of free, hands-on lessons that cover the vulnerabilities and their mitigation steps.
Supplement with Snyk Top 10 open source vulnerability lists
To further support security-conscious developers, and in the spirit of (and, really, in supplement to) OWASP, we released a Snyk Top 10: Open Source Vulnerabilities report late last year that covered the top types of vulnerabilities found most frequently in user scans.
We're excited to announce that we've now released language-specific Snyk Top 10 cheat sheets for Java, JavaScript, Go, .NET, PHP, Python, and Ruby. Download these sheets and the original report today.
Each sheet contains the 10 most frequently occurring critical and high severity vulnerabilities for the language, the top occurrence of each type, and the mitigation steps for that specific vulnerability. So download the sheets for the languages you use most and keep them handy.
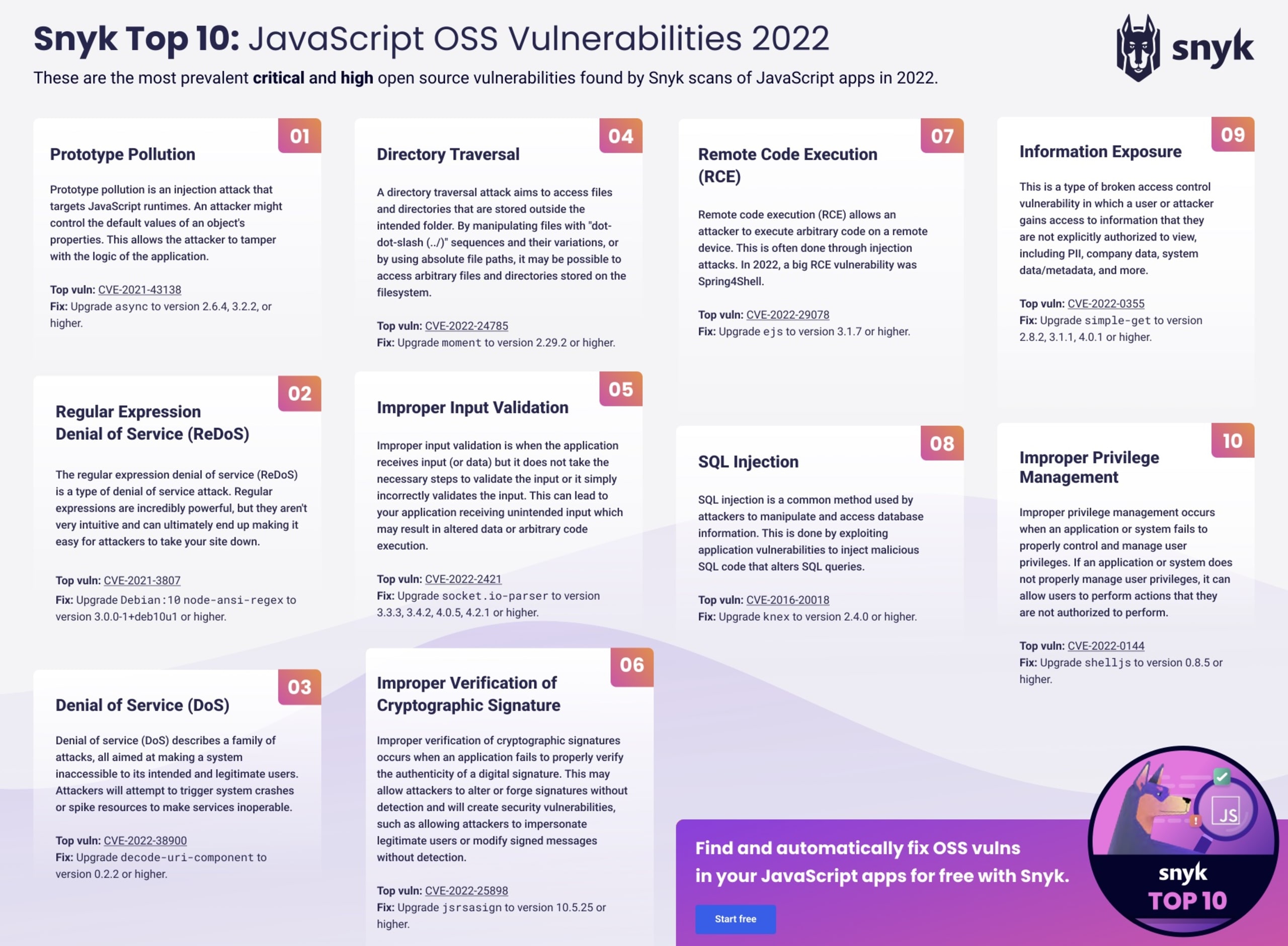
As an example, here is the Snyk Top 10 cheat sheet for JavaScript. Download the PDF or browse the other available languages.
But wait, there's more (from Snyk Learn)
Snyk Learn has just released a new learning path focused on the Snyk Top 10 vulnerabilities. The lessons in this learning path include denial of service, remote code execution, deserialization of untrusted data, and many more.

The new learning path from Snyk Learn provides comprehensive training on the Snyk Top 10 vulnerabilities, including how to identify and fix them. The course is designed for developers, security engineers, and other IT professionals who want to improve their knowledge and skills in software security.
In addition to the Snyk Top 10 learning path, Snyk Learn offers a range of other lessons to help developers improve their security skills. These include lessons on code injection, broken access control, insecure hashes, and many more. Visit Snyk Learn to get all the security knowledge you need in a bit-sized format with interactive widgets along the way! Let’s make your code safer.
Stay open, stay safe
Open source has been an amazing enabler of digital transformation, but we can't just use it blindly. Developers need to know the risks that they take on with OSS, as well as how to mitigate those risks. The Snyk Top 10 is one more way to help keep you safe while maintaining release velocity. Another way is with Snyk itself.
With Snyk Open Source, you can easily find and fix the vulnerabilities in the open source libraries your applications use — as well as the transitive dependencies within those libraries. The fix is typically as simple as upgrading. Snyk Open Source also finds and addresses licensing issues in (or caused by) these open source libraries.
Create a free account today and secure your open source software.
Snyk Top 10
Learn about the top vulnerabilities
Read our Snyk Top 10 report and cheat sheets to know what security vulnerabilities are most common in the wild.
