Docker Hub authentication: Is 2021 the year you enable 2FA on Docker Hub?
15 de março de 2021
0 minutos de leituraJudging by the reactions I saw in the audience during my past talks on “Securing Containers By Breaking In”, as well as recent reactions on Twitter, not many know about Docker Hub’s fairly recent multi-factor authentication feature.
In October 2019, in order to improve the Docker Hub authentication mechanism, Docker rolled out a beta release of two-factor authentication (also known as 2FA). This new capability further strengthens the software supply-chain security of the primary and largest hub of docker container images and applications.
One of the topics I discussed during my talks was the state of 2FA availability for maintainers and developers across the npm registry and the Docker Hub registry. I was aiming to gauge the audience’s reaction to the following slide which declares that not a single account on Docker Hub had enabled 2FA!

What’s behind this number?
Simply put, Docker Hub authentication didn’t support multi factor mechanisms up until October 2019. If we look at other registries to draw some comparisons - data shared about the npmjs registry in January 2020 shows that only 9.27% of all developers enabled 2FA. Given the fact that 2FA was introduced on npmjs in late 2017, developers are lagging behind on their software supply chain security.
Docker Hub rolling 2FA
Given Docker Hub’s position as the primary software registry for container images, hosting millions of docker images, software supply chain security clearly needs to be taken seriously.
The Docker team’s announcement on the Github repository about their plans to roll out 2FA support for Docker Hub authentication was warmly welcomed by the community.
In October 2019 the beta version of 2FA support for Docker Hub was officially announced, and available for users to enable.
Enable Two-Factor Docker Hub Authentication
We have previously outlined 10 Docker Image Security Best Practices to follow. The support of 2FA in Docker Hub authentication is a significant step forward in docker image security and software supply-chain. It is in your project’s best interest if you enabled it. This way, you reduce the risk that an attacker can compromise your account and inject malicious docker container images to the container registry.
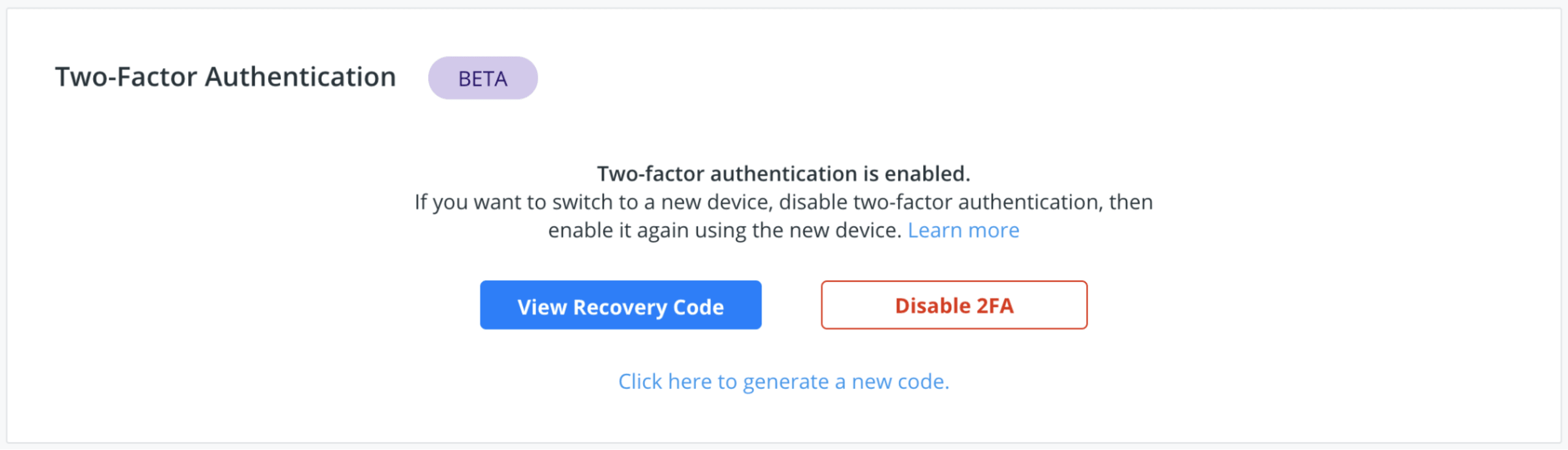
How to enable Two-Factor Authentication on Docker?
To enable 2FA, head over to your account’s security settings on Docker Hub and follow the guidelines on enabling 2FA. Once you’re done, consider sharing the good news and spreading the word!
Your container image security
Is 2FA for Docker Hub enough for security?
Securing access to your image repositories is great, now let’s talk about the images themselves. Snyk Container Scanner allows developers to scan images for CVEs right from your desktop, a real game changer for developer first security. Try if for yourself by installing the Snyk CLI and running this simple command (replace node:latest with your image tag):
If you have the Dockerfile for your image available, you can get ever more details by adding --file Dockerfile to the above command. You can read more advanced command line usage on Snyk’s Container CLI documentation site.
Snyk Container scanning can also integrate directly with your Docker Hub repositories, providing full observability into security vulnerabilities pushed there. It also can monitor and alert you to vulnerabilities found in your images in the future, even if you haven’t changed or pushed new images there.
Snyk is free for open-source and provides a free tier for private projects too, so you can sign up with Snyk to test and fix your Docker images. Of course, don’t stop there - import your application projects too!
Developer-first container security
Snyk finds and automatically fixes vulnerabilities in container images and Kubernetes workloads.
More Docker security practices to follow up on:
