360 degrees of application security with Snyk
Soumen Mukherjee
24 de abril de 2024
0 minutos de leituraApplication development is a multistage process. The App goes through various stages, each with its own area of focus. However, application security, a.k.a. AppSec, is constant throughout all the stages.
For example, when a developer codes, it’s expected that the code will be secure. Similarly, the artifacts that are worked upon or generated as an end output of the respective stages are all required to be secure.
In such scenarios, what comes as an enterprise nightmare is the situation of dealing with a myriad of tools and platforms, each performing a specific function as part of the stage security control. Having multiple and different tools is not only prohibitively expensive but also poses a challenge to the IT team for the management and governance of assets. Similarly, multiple tools imply multiple integrations during the build pipeline, which further slows down or adds more cycles to the build process. The development community also hates such a scenario since multiple tools mean working in different windows, and each tool comes with its own learning curve and access and collaboration issues.
But all this has a solution. If we have a platform that provides all the required stage gate controls across the secure development life cycle, then it solves all the problems outlined above. So today, we’ll have a brief look into various features of the Snyk platform and how it provides 360 degrees of application security.
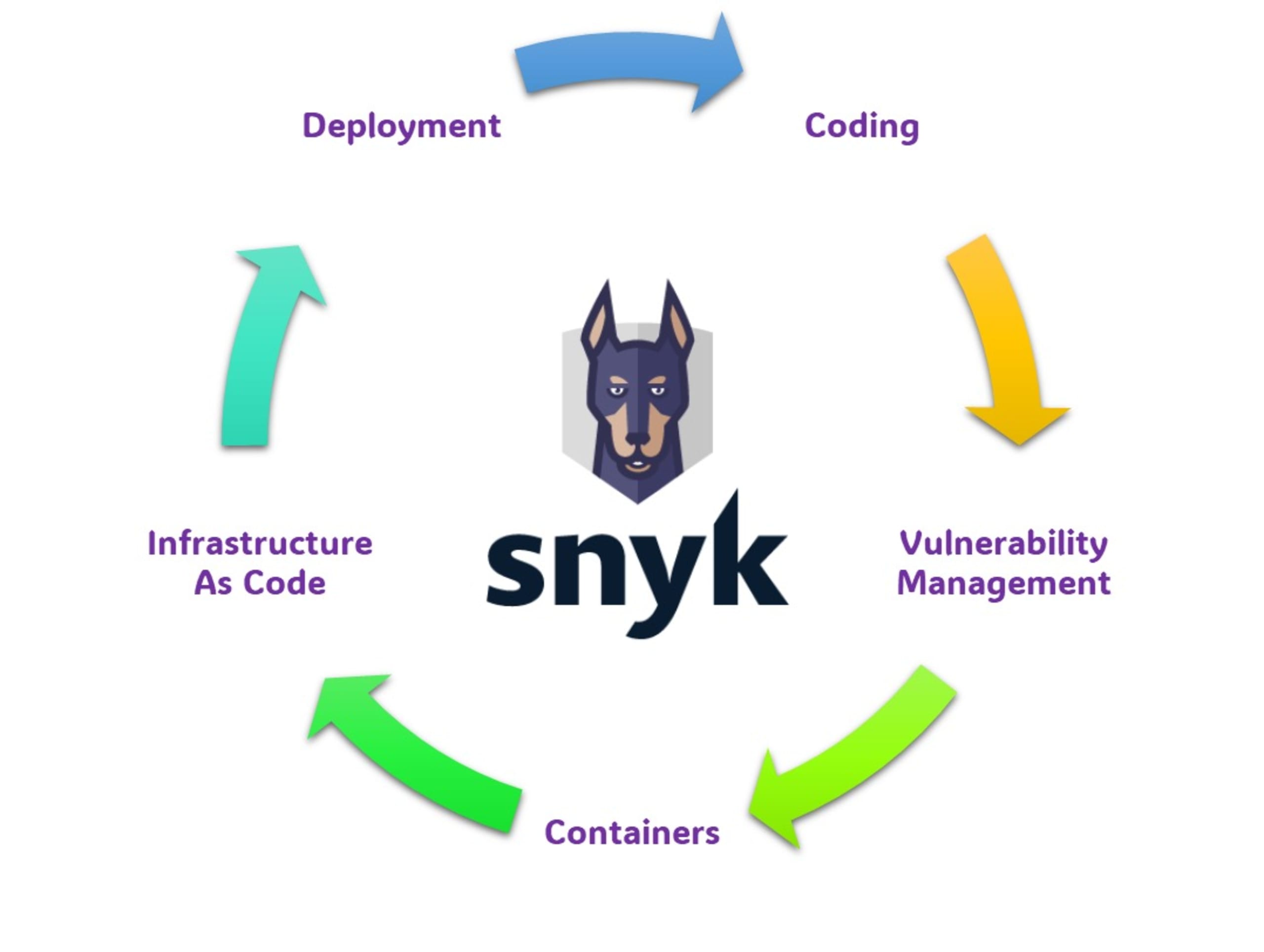
Coding
As a Security Architect, when you want to formulate a development toolchain for addressing secure coding, you start by making sure that the developers are aware of the secure coding standards. Then it is a gradual process that takes time and repeated human interventions. Snyk gives you a way to shift left with Snyk Code, where the developers are using the Snyk extension for your IDE to get a piece of first-hand information about the vulnerabilities that they might be incorporating through errors and omissions during the coding process. Snyk Extension is supported with all the popular IDEs available in the ecosystem today.
To know more on how to get started with Snyk Extension in your IDE, visit the Snyk Extension Documentation.
Alternately, as another control gate for the code, you can set up your code repo to have direction integration with Snyk, where Snyk periodically scans your code repo for the new changes since the last scan and outlines any vulnerable code that it comes across. Snyk supports integration with all major on-prem and cloud code repository solutions available.
To learn more about how you can get started quickly, visit the Snyk Code documentation.
Vulnerability risk management
Much of today’s software is foundationally driven by the numerous third-party frameworks that it consumes. This model has its own benefits for the business. Reusable pieces of code can help speed up the application development process and add functionality, but they’re also a double-edged sword as they may contain vulnerabilities or malicious code that can lead to severe security incidents for its users. Again, as a security architect, if you want to adopt some technical controls that align with the shift left strategy, Snyk provides a complete toolset to empower your developers by scanning the open source packages for vulnerabilities during development with the Snyk Extension for IDE.
Also, since vulnerabilities in third-party packages can bubble up at any time in the future, Snyk’s code repository integration gives the AppSec team the information they need to assess the severity of any new vulnerability and open a PR on the fly for the corresponding development team to fix and merge into the main branch.
To learn more on how Snyk fix PRs and merge requesat work, visit the Snyk documentation.
Container vulnerability management
Container-driven development is the norm today. Containers are not restricted only to the cloud environment but are an integral part of on-prem deployment across enterprises and are actively used in the embedded world with appliances/devices running a highly customized version of Linux as the operating system, with a minimum footprint as required to host the containers in a closed and secured environment.
While all this is good, it offers no protection against container vulnerability exploits due to poor code or third-party packages used in the application — or the third-party and native packages for the respective base images of the containers.
Container image vulnerabilities typically arise from insecure libraries or other dependencies imported into a container image. Images could also contain malicious code inserted during a software supply chain attack or a similar breach of the development environment.
Many of these issues can be identified early in the development cycle by using Snyk Container. You can integrate Snyk with various container repositories or connect the containers through the build pipelines. It is important to outline here that we can also leverage Snyk Extension features for IDE to identify issues arising from poorly written docker files or the use of malicious images as part of the base artifact.
To see the full length and breadth of Snyk Container’s features visit the Snyk documentation.
Infrastructure as code security
With the advent of DevOps, Infrastructure as Code came to prominence. However, studies show that a majority of security vulnerabilities in cloud-based applications primarily trace their origin to a misconfiguration of security settings.
Infrastructure as code (IaC) security is the approach to cloud security that involves embedding consistent cloud security coverage throughout the software development life cycle. This helps to detect misconfigurations early, preventing vulnerabilities at runtime. IaC security can be enforced in code repositories, CI/CD tools, or as early as the developer IDE.
IaC security involves addressing cloud configuration issues in IaC rather than deployed cloud resources. This includes:
Identifying misconfigurations: Scanning IaC to identify variables with missing or incorrect settings.
Defining security policies: IaC can be used to define security policies and to enforce those policies when changes are made to the infrastructure.
By virtue of its integrations with code repositories and build automation solutions, the Snyk CLI and Snyk Extensions for IDE provide the necessary tools to enforce shift left security through the development life cycle.
To know more about Snyk Infrastructure as Code, visit the Snyk documentation.
Post-deployment vulnerability risk management
The application security responsibility does not end with the secure and successful deployment of the application. It is a continuous process of monitoring the deployed assets on the infrastructure for new vulnerabilities that keep popping up in the numerous third-party packages and components that modern-day solutions use.
Understanding the ecosystem within which the modern-day solutions are deployed is also important. Kubernetes, a.k.a K8S, is the most popular and preferred environment in which the applications get deployed. Still, the challenge here is how to monitor the runtime pod/cluster for vulnerabilities and raise appropriate flags with the corresponding stakeholders to identify potential threats to the environment. If this wasn’t enough, the presence of multiple cloud providers adds to the challenge in its own sense.
The Snyk platform offers a unique proposition whereby Snyk can integrate with Kubernetes across all major cloud server providers, enabling you to import and scan your running workloads. This helps you identify vulnerabilities in their associated images and configurations that can make those workloads less secure. Post workloads import, Snyk continues to monitor them and to identify additional security issues as new images are deployed and the workload configuration changes. Snyk provides the Snyk Controller, which, once installed in the corresponding cluster, provides near real time visibility to the application security on the state of vulnerabilities in the running workloads.
To know more about the Snyk Kubernetes integration feature, visit the Snyk documentation.
