npm Supply Chain Attack via Open Source maintainer compromise
8 septembre 2025
0 minutes de lectureOn Monday, September 8th, a highly regarded open source developer, ~qix, was compromised via a phishing email. ~qix is an author and maintainer behind a large number of popular npm packages and found himself caught by this attack after responding to a message from the email address of support [at] npmjs [dot] help.
This resulted in the attacker taking over his npm account and having access to publish malicious versions of packages to which Qix had privileged access.
September 9th update: added new npm packages found to be impacted.
September 10th update: added new npm package found to be impacted.
What happened?
The open source developer fell victim to a phishing email that allowed an attacker to gain access to their npm account. This enabled the attacker to inject malicious code into many highly popular npm packages, creating a supply chain attack.
At this time, this is the only known open source maintainer that was targeted. However, there could be other high target developers who were impacted that have not been reported yet.
How was it executed?
The attacker used social engineering to send a phishing email targeting a prolific open source developer. The email tricked the developer into authenticating and bypassing security controls that afforded account access to the attacker. The attacker then had the ability to inject malware into any of the popular open source packages to which the developer possessed privileged permissions to and therefore publish new versions of those packages containing the malware.
The malicious code listens for network traffic when run in the context of a browser and focuses on crypto transactions. The malicious code injected into the packages activates a hook whenever a Web3 wallet is present. Once activated, the code intercepts and modifies any transaction with ETH value and points it to another address presumably controlled by the attacker. The malicious code also listens for swap/transfer transactions to tamper with as well.
What data was targeted?
The attacker was targeting crypto wallets available via user browsers to drain funds by redirecting transactions or approvals the user signed to the attacker’s addresses. No other data is believed to be targeted by the attack at this time.
Affected packages and versions
Timeline of the attack
~1:00pm UTC: First set of detected compromised packages published
2:16pm UTC: Developer is alerted to potential account compromise on social platform Blue Sky
3:16pm UTC: Developer confirms account compromise via Blue Sky post and has alerted npm to the incident
5:17pm UTC: npm acknowledges the breach and is working on removing the compromised packages
7:59pm UTC: npm reports to developer that all impacted package versions have been taken down
Indicators of Compromise (IoC’s)
GitHub user SindreSorhus shared a quick command to check if this malware is found in your dependency tree:
For package maintainers, if you received an email from support [at] npmjs [dot] help and you followed the instructions from it you are likely impacted as well.
What Should You Do?
This is an ongoing incident, so monitor updates to this post and from the developer Qix on GitHub.
Check if the malware is found in your dependency tree using the script shared by Sindre Sorhus
Snyk Users
You can use Snyk SCA and Snyk SBOM to locate and monitor projects org-wide
If a test has not run since the advisories were published trigger a retest
CLI projects should be re-monitored to ensure your current dependency tree is detected
Snyk Reports
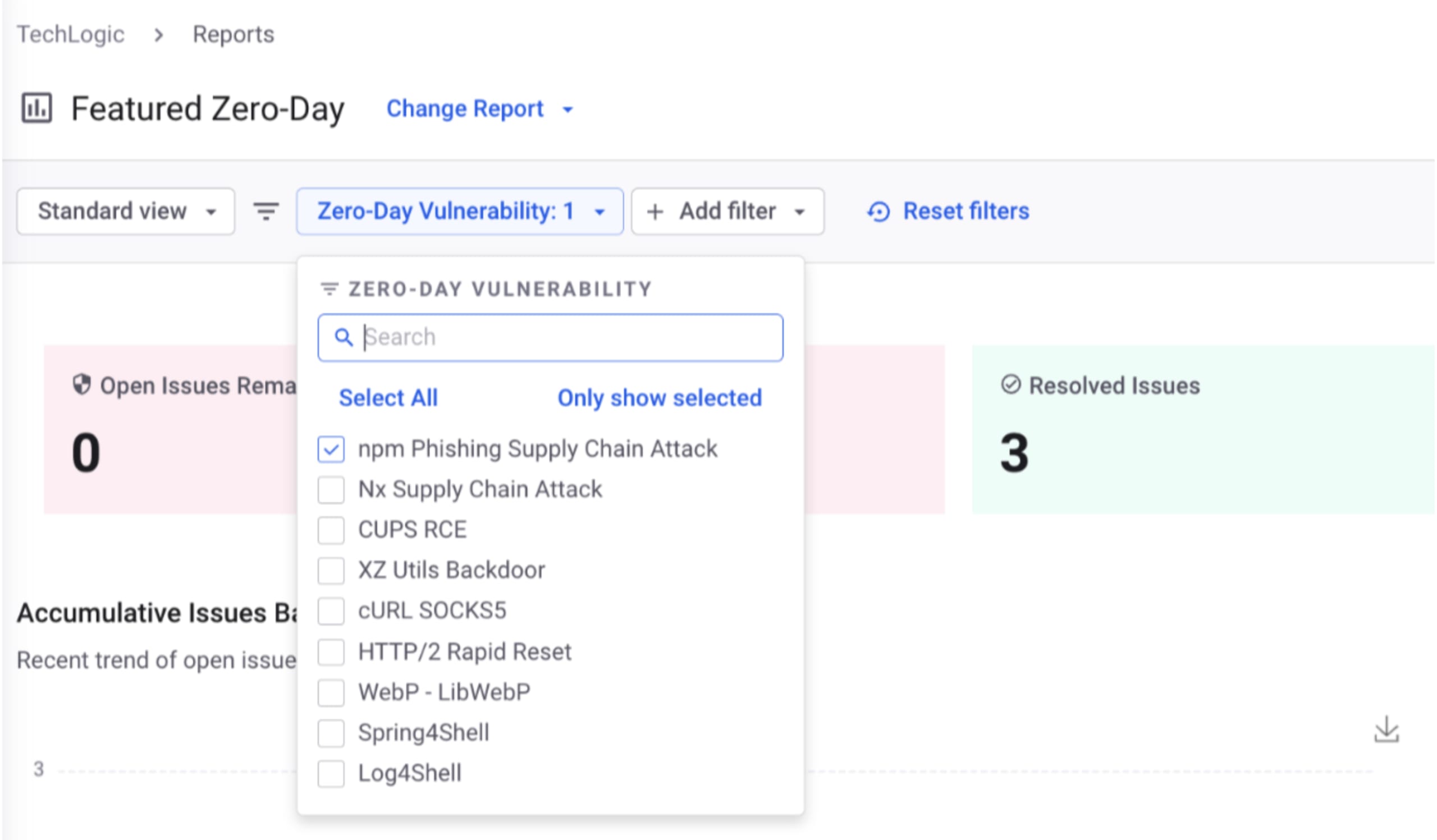
There is a report available in Snyk’s “Featured Zero-Day” report list for this set of vulnerabilities. If you have an Enterprise plan you can access this report by clicking “Reports” in the left hand navigation (both Group level and Org level reports are available). By default this presents the “Issues Detail” report but you can click the “Change Report” drop-down next to the report title and select “Featured Zero-Day”. Then on the following screen, select the "npm Phishing Supply Chain Attack" report from the Zero-Day drop-down list.
On supply chain security attacks
This comes along with a few other recent security incidents of this nature. We’ve seen CI and maintainer-account attacks allowing release hijacks before:
The ESLint/Prettier maintainers compromise (July 2025): Phishing + typosquatting (npnjs.com) harvested npm credentials and pushed malware to popular packages, another reminder to harden maintainer accounts with 2FA.
Weaponizing AI Coding Agents for Malware in the Nx Malicious Package Security Incident (August 2025)
Profitez d’une démo de Snyk pour la sécurité open source
Échangez avec nos experts de la sécurité pour voir comment Snyk peut vous aider à utiliser l’open source en toute sécurité
