Getting started with Snyk for secure Python development
Daniel Berman
4 août 2021
0 minutes de lectureIf you’re a Python developer looking to easily secure your applications, you’re in the right place! Snyk helps you secure all the code making up your Python app — your own code, the open source libraries you’re pulling in, your containers, and your infrastructure as code (IaC) — by integrating seamlessly into your existing development workflows.
The Snyk platform is comprised of four products, each designed to help you secure the different building blocks in your Python app in the most frictionless way possible:
Snyk Code for finding and fixing security and quality issues in your own Python code.
Snyk Open Source for finding and fixing security vulnerabilities, and license issues, in the open source Python packages being pulled in to build your app.
Snyk Container for finding and fixing security vulnerabilities in your Python container images.
Snyk Infrastructure as Code for finding and fixing security vulnerabilities in the code configuring the deployment of your Python apps.
In this article, we’ll take a look at how easy it is to integrate Snyk’s security testing into the way you’re already working. Snyk’s Free plan is more than enough for testing out the different steps described below and indeed for any small-scale project.
Securing your Python app from the get-go
As a developer, the earlier you catch issues, the easier it is to fix them. Fixing a critical vulnerability after you’ve already packaged and shipped your code is simply more time-consuming than fixing it earlier in the process.
Pro tip: Snyk is free to try and use for open source. To use Snyk Open Source or Snyk Code using an IDE plugin, you do not have to give Snyk access to your GitHub repositories. The easiest way to test Snyk is to set up a free account and scan an open source repository. No installation is required and the integration is done in seconds.
Snyk provides you with a number of ways to secure your code very early on in development — in your IDE, using Advisor, and the Snyk CLI.
IDEs
You can also use Snyk to secure your code within your IDE. Snyk’s plugin for PyCharm, for example, supports both Snyk Open Source and Snyk Code, and helps you easily find and fix known vulnerabilities in your open source dependencies as well as any security issues and bugs in your own code.
The plugin is easy to set up, and can be downloaded and installed like any other JetBrains plugin directly from within your IDE.
Go to Preferences, then Plugins from within PyCharm, search for Snyk in the JetBrains marketplace, and click OK to download and install the plugin.
Next, connect the plugin with your Snyk account. To do this click the Connect your IDE to Snyk button in the plugin’s view and follow the prompts to authenticate.
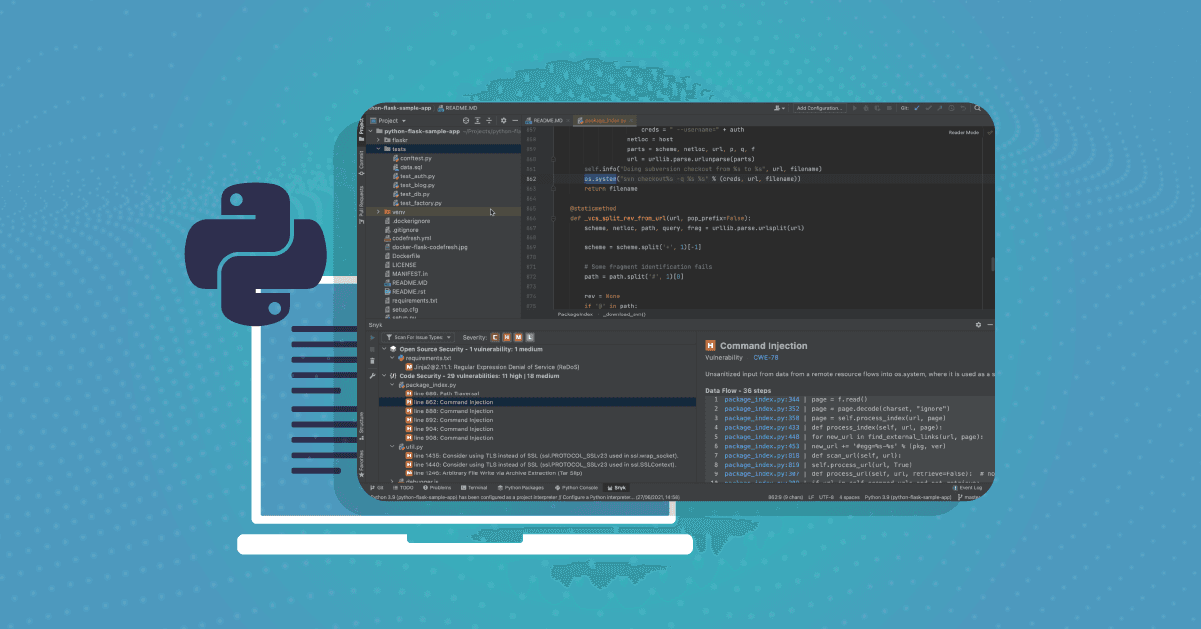
That’s it! All you have to do now is run a Snyk test. Hit the Analyze now! button to commence Snyk’s security testing. Within a few seconds, the plugin provides a list of all the different types of issues identified, bucketed into three categories:
Open Source Security: known vulnerabilities in both the direct and in-direct (transitive) open source dependencies you are pulling into the project
Code Security: security weaknesses identified in your own code
Code Quality: code quality issues in your own code

For issues identified in your own code, for example, the plugin details the data flow, pointing to the relevant files and lines in your code leading to the issue. You can click on the file name to quickly open the file at the exact line introducing the issue. Data flow analysis helps you identify problems and how they flow across the application to make complex issues easy to understand and follow.
But the plugin doesn’t stop at that. In addition to showing what is wrong in the code, the plugin also provides examples of how others have fixed the issue to help you take faster action.

Snyk Advisor
Snyk Advisor is a free, online, research tool that can help you decide which open source packages or container base images to use. Containing all projects from PyPi as well as Python base images from Docker Hub, you can, as a Python developer, use Snyk Advisor to research different packages and images to ascertain their general health and security status before inserting them in your project.

For the project scanned in the step above, researching the Jinja2 package would have revealed that version 3 is not only the most popular one but is also free of vulnerabilities.
CLI
The Snyk CLI is a powerful, free tool you can use to execute Snyk’s security scanning in your local development environment, either manually or as part of your CI/CD pipeline. It provides a long list of arguments you can use to extract specific details from Snyk’s scan results and to customize the testing process.
Note: Snyk CLI is based on Node.js and npm, SCOOP, or Homebrew. You need to have them installed before you can use Snyk CLI.
Setting up the Snyk CLI is simple. You can use npm or Homebrew to quickly install it and then all that’s required is to authenticate with your Snyk account:
Testing your Python project is one additional step away — simply execute the snyk test command from the root folder of the project.
For Snyk Open Source tests, you will also need to install dependencies with:
Pro tip: You can generate the requirements.txt for a project if you activate the virtual environment and use the pip freeze > requirements.txt command.
Snyk provides us with more than just a list of vulnerable dependencies and license issues but also additional remediation information such as the recommended versions to upgrade to for some of the dependencies.
In the case of the project used for this article, Snyk is flagging a medium severity vulnerability introduced by the Jinja package version 2.11.1 and is recommending a minor upgrade to version 2.11.3 to apply a fix.

You can also use the Snyk CLI to get notified about newly disclosed vulnerabilities or new fixes to existing vulnerabilities. To do this, use:
"Results are available in the Snyk app, at the URL provided, and you will be notified in case new and relevant vulnerabilities are disclosed.

You can use the same CLI to scan your Python containers for security issues and your infrastructure as code (IaC). Snyk Code support for the CLI will be available soon so stay tuned!
Using the same project, try testing the application’s container image with (you’ll need to build the image before testing):
The Snyk CLI will scan the image for issues and add some tips for upgrading the base image.

Finally, you can scan your code using Snyk Code. Using the command:
The CLI will scan the local project and display the results.

Check out the CLI cheat sheet for more tips and tricks on the Snyk CLI.
Snyk’s IDE plugins, Snyk Advisor, and the Snyk CLI are all available for free with unlimited scanning for open source Python projects.
Integrate security into your Python repos
According to the last Python community survey conducted in 2019, 90% of Python developers use Source Code Management (SCM) systems like GitHub. It wouldn’t be surprising to see an even higher number were we to ask Python developers that question in 2021.
Since a lot of your development time and processes involve these systems, being able to easily add security into the mix without slowing down development can be extremely valuable. How so? A few examples:
To ensure you’re not introducing vulnerable code into your Python repository, what if you could automatically scan every new pull request for issues?
To ensure your Python application is healthy and up-to-date, what if you could automatically trigger pull requests for upgrading outdated Python packages?
To ensure you are quick to fix newly disclosed vulnerabilities, what if you could receive a notification and a pull request with the recommended fix needed to resolve the issue?
To automate security as part of your CI/CD process, what if you could add security testing as a GitHub Action or as part of your Bitbucket pipelines?
To ensure your proprietary code is secure, what if you could quickly scan it for security issues and identify how malicious data flows through your app overlaid on top of your own code?
Snyk provides you with all this. In just a few steps, you’ll be able to import your Python project into Snyk to ensure it’s properly protected.
Within Snyk, go to Integrations, then GitHub, and select your Python project to import it into Snyk. As it imports the new project, Snyk will automatically scan ALL the different components making up your Python project and display them as individual sub-projects on the Projects page:

Opening the deployment.yaml file, for example, provides information on issues Snyk Infrastructure as Code identified in application’s Kubernetes deployment configurations.

Once imported, your Python project is continuously monitored by Snyk. In case of new vulnerabilities in your open source dependencies, or new fixes for existing vulnerabilities, a pull request will automatically be triggered.

Snyk automatically opens pull requests in a number of other scenarios, and you can control the pace and frequency at which they are triggered to ensure you are not overwhelmed with too many pull requests. More information on Snyk’s remediation can be found in the Snyk documentation.
Snyk’s SCM integrations are available for free with unlimited scanning for open source Python projects. There is some variance between SCMs in terms of Snyk products supported.
Automating Python security as part of CI/CD
Integrating Python security testing into your CI process is a great way to catch vulnerabilities before your code gets pushed into production. This additional security gate ensures that you’ll catch issues even if you didn’t execute manual testing in your local environment.
Snyk integrates with all the leading CI/CD tools, such as Jenkins, CircleCI, and TeamCity, and as mentioned above, the Snyk CLI can be used as a step in any automated pipeline. Let’s take a look at one example: adding Snyk security testing as part of a GitHub Actions workflow.
Snyk provides an Action for all the latest versions of Python, including Python 3.6, 3.7 and 3.8. In this case, we will use the action to automate security testing for the same Python project tested throughout this article.
First, define your Snyk API token as a secret in your repository settings (Settings Secrets). Then, open the Actions tab and create a new custom workflow with the Python Snyk Action:
As expected, the same vulnerability we identified in our CLI test above failed our build:

Since the Action is based on the Snyk CLI, you can use all the arguments it supports to tweak the behavior of Snyk’s security testing as part of your CI process.
Develop fast. Stay secure!
Python is great for developers who want to move fast. It’s an extremely versatile language, it’s easy to write, and there are a wealth of open source libraries to quickly add functionality to your applications. When it's time to ship your app, Docker, Red Hat, and others provide a slew of Python container base images that are easy to use and you can even write your Kubernetes and infrastructure configurations in Python.
Moving fast and being secure are not mutually exclusive. Hopefully, this article showed how easy it is to add security into your existing Python development workflow, whether in your local development environment, as an integral part of your Git-based workflow or together with your automated build process, and most importantly — without the need to slow down!
Détecter et corriger automatiquement les vulnérabilités
Snyk fournit des PR de correction en un clic et des conseils de remédiation pour votre code, vos dépendances, vos conteneurs et votre infrastructure de cloud.