Detecting application vulnerabilities in container images
Danielle Inbar
18 mai 2020
0 minutes de lectureSnyk now makes it even easier for you to detect vulnerabilities in container images, by identifying vulnerable application dependencies alongside the operating system vulnerability.

Lost provenance and third-party images
Snyk today provides the ability to detect vulnerabilities in your Java, .NET, Python, Go, etc. application dependencies, as well as in your container images. But, until now, we've left those as separate commands in our CLI.
That works well when you're testing your application dependencies, building images, and then testing the container operating system vulnerabilities as part of a tightly integrated pipeline. But what about the third-party images you're running where you never had the source code? Or that image in your registry which you're not quite sure what version of the software it has installed.
A single scan to find all your vulnerabilities
Previously, when we scanned a container image, we'd show something like:
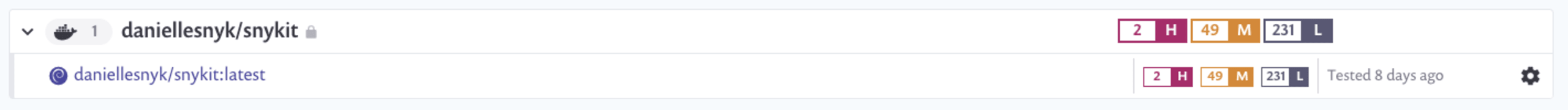
Here you can see the image name, an icon representing the base image operating system, and the number of high, medium, and low vulnerabilities. Scanning the same image today will show:

Here you can see we've also detected applications in the images and found some vulnerabilities present in their dependencies as well.
This feature builds on Snyk's world-class vulnerability database, which contains vulnerabilities from a wide range of public and private sources, including the work of our very own research team.
Availability
We're starting to roll this new feature out across our container integrations now, starting with our support for container registries. If you're using Amazon ECR, Docker Hub, GCR, ACR, or Artifactory you can use this today. We'll add support to our Kubernetes integration and CLI tools next but we like getting features into your hands quickly.
We've also started with a subset of languages, focused mainly on dynamic languages at the moment. Today we have support for Python, JavaScript, PHP, and Ruby. In time, we'd like to support all the languages we support elsewhere.
For new Snyk users and for those with free Snyk accounts we're enabling this feature by default. For Snyk Container customers we're erring on the side of caution, as we don't want to introduce unexpected noise into how you report on vulnerabilities in Snyk. Whether you are a free or paid user you can enable or disable this functionality in the settings page:

Let us know what you think
As always, please let us know what you think about this new feature, and what you'd like to see next.
La sécurité des conteneurs au service des développeurs
Snyk détecte et corrige automatiquement les vulnérabilités des images de conteneurs et des charges de travail Kubernetes.
