Cybersecurity Venture’s 2023 Software Supply Chain Attack Report
10 octobre 2023
0 minutes de lectureCybersecurity Ventures predicts the global cost of software supply chain attacks will reach nearly $138 billion by 2031.
Most enterprises' critical infrastructure and operational pipelines rely on an intricate web of software, online services, and cloud applications. This level of complexity makes supply chain risk management one of (if not the) biggest challenges for CISOs today.
Today, malicious actors choose to exploit software supply chain vulnerabilities rather than just target end users. These SSC attacks have caused some of the most notable cybersecurity incidents and data breaches in recent years.
Software supply chain security attacks will continue to escalate in the coming years, potentially costing businesses a staggering $138 billion by 2031. These stats and other key findings from the Snyk-sponsored 2023 Software Supply Chain Attack Report underscore the pressing need to take proactive measures and secure software supply chains immediately.
Grasping today’s attack landscape
By targeting the software supply chain, cybercriminals can compromise multiple victims simultaneously, or infiltrate an entity that would’ve been difficult to reach directly. Software supply chain attacks are far more effective than other techniques, making them an ideal choice for many of today’s malicious actors.
Some of the most common supply chain attack methods and approaches include:
Social engineering
Stolen credentials
Insider threats
Cloud hijacking
A recent example of a devastating attack
SolarWinds is a SaaS provider that created Orion, software for managing and monitoring business infrastructure. In 2020, cybercriminals inserted a backdoor into a plugin that SolarWinds distributed as an Orion update. This malicious update affected around 18,000 customers, including technology firms and government agencies. The attackers then targeted high-profile organizations, including cybersecurity firm FireEye, with follow-up attacks.
The SolarWinds attack is unique because it led to consequences in the physical world. It impacted critical infrastructure providers, putting energy and manufacturing operations at risk. Because so many major businesses use Orion software in some capacity, the attack’s repercussions are still resonating today.
Rising SSC attack frequency
The number of software packages affected by supply chain attacks increased from around 700 in 2019 to more than 185,000 in 2022.
Today, organizations of all sizes — from small enterprises to Fortune 500s — depend on a diverse ecosystem of systems and software, including open source components, commercial software, proprietary applications, virtual networks, and cloud technologies.
With growing dependence on these diverse ecosystems, Gartner predicts that by 2025, 45 percent of organizations worldwide will have experienced attacks on their software supply chains — a three-fold increase from 2021.
Gartner also foresees that by 2025, 60% of supply chain organizations and their Chief Supply Chain Officers (CSCOs) will consider cybersecurity risk a significant “determinant” in digital supply chains, third-party transactions, and business engagements.
The rapidly rising frequency of software supply chain attacks is a stark reality. It’s more crucial than ever for organizations to prioritize software supply chain security — before a link in part of their supply chain gets compromised.
Costly consequences
Today’s software supply chains are like intricate webs, each element serving as a potential entry point into your organization.
We can compare software to a box of brownie mix. Each ingredient in the brownie mix, such as sugar, cocoa powder, or flour, came from its own separate supply chain. In the same way, the software supply chain includes layers of code, development tools, and processes — each produced by its own software supply chain and relying on dependencies to operate. Each of these layers has the potential to compromise the security of the final digital product.
The complexity of the software supply chain underscores the need to implement robust SSC security measures. The Cybersecurity Ventures Report predicts that the global cost of software supply chain attacks on businesses will increase exponentially between 2024 and 2031. They foresee the following costs in the coming years:
2024: $51,750,000,000
2025: $59,512,500,000
2026: $68,439,375,000
2027: $78,705,281,250
2028: $90,511,073,437
2029: $104,087,734,453
2030: $119,700,894,621
2031: $137,656,028,814
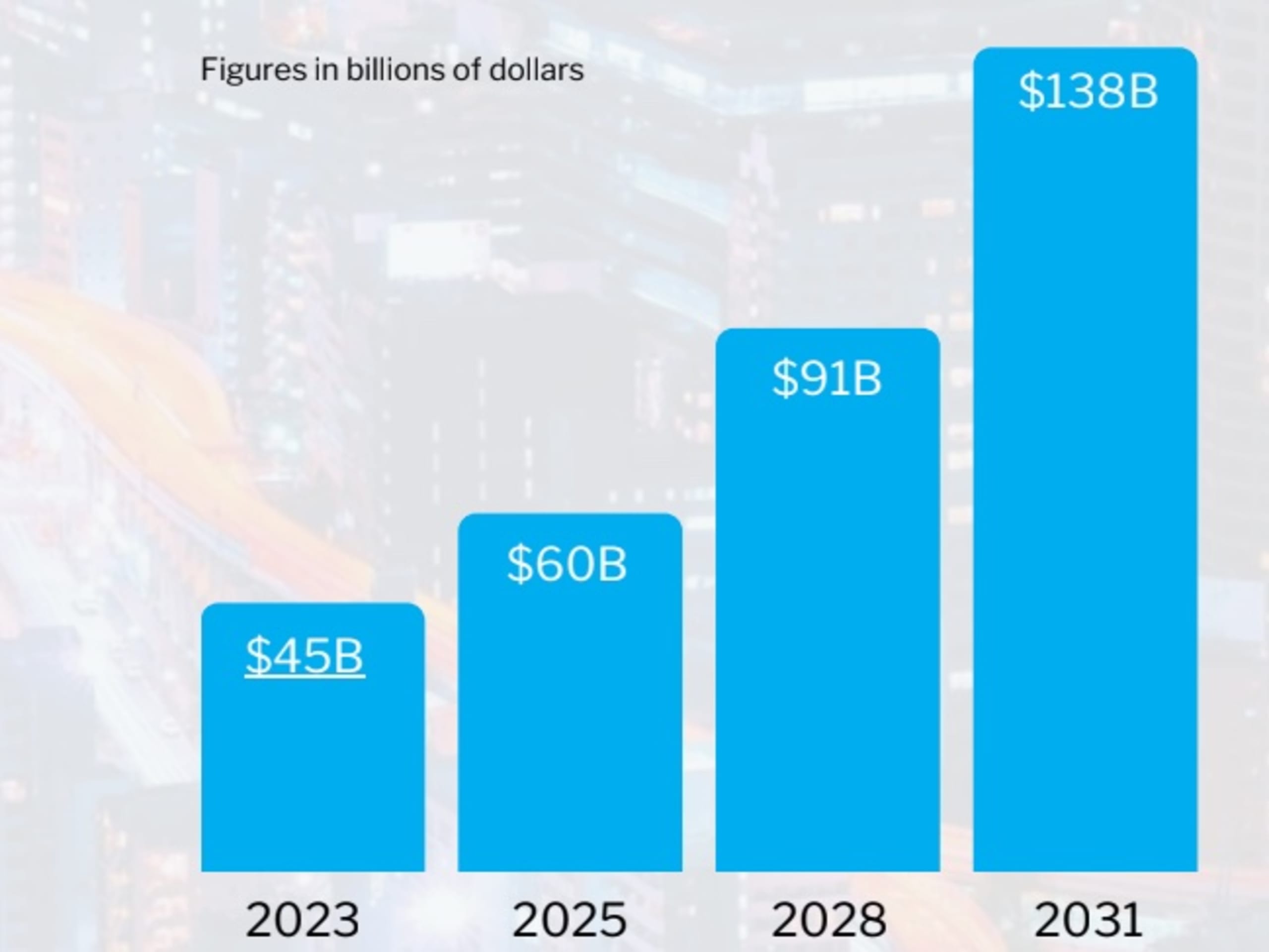
These figures emphasize the urgent need for proactive software supply chain security. It will take timely action today to protect your organization's digital assets from SSC risk tomorrow.
The time to act is now
Are you ready to better protect your applications from the next software supply chain security attack? The time to adjust your AppSec programs is now!
Developers play a critical role in securing the software supply chain and should prioritize security in their coding and product development processes to mitigate the risk of attacks. To involve your development teams, start by adopting suitable security practices, collaborating with security experts, and integrating security into the earliest stages of product development.
Snyk prioritizes developer-first security, visibility, and remediation for every critical component of the modern application, including the following:
Book a live demo to learn more about Snyk’s developer-first solutions that continue to redefine AppSec. To discover more software supply chain security stats, download the full report.
