How to detect the ExternalIP Kubernetes vulnerability in your Kubernetes configurations with Snyk
December 10, 2020
0 minutos de leituraOn Tuesday, a Kubernetes vulnerability was announced affecting all Kubernetes versions where a hostile user may be able to intercept traffic if external IP addresses are being used on services. Snyk has added a new check to Snyk Infrastructure as Code (Snyk IaC) to check your Kubernetes deployment definitions and notify you if you are vulnerable to this type of attack.
Unfortunately, due to the nature of CVE-2020-8554, it is not patchable and the recommended workaround is to not use external IP addresses. Multi-tenant clusters, in particular, are at risk of attack because this vulnerability may allow one tenant to see another tenant’s traffic if users have the right to create ClusterIPs or patch LoadBalancer services.
Snyk Infrastructure as Codeprovides security feedback in your Kubernetes development process, by scanning your Kubernetes configuration files for any security issues, enabling you to keep your infrastructure secure as you write your definitions. We regularly release new security rules, based on recommended security practices and our own research. To address this vulnerability we published a new security rule, Service is using an external IP, to tell you whether your Kubernetes environments may be vulnerable to CVE-2020-8554.
In the example below we have detected the use of externalIPs which shows that this particular deployment may be vulnerable to this CVE. The recommended workaround is to remove the usage of externalIPs altogether, which you can validate by making the necessary change and rescanning the file to see that the issue is resolved.
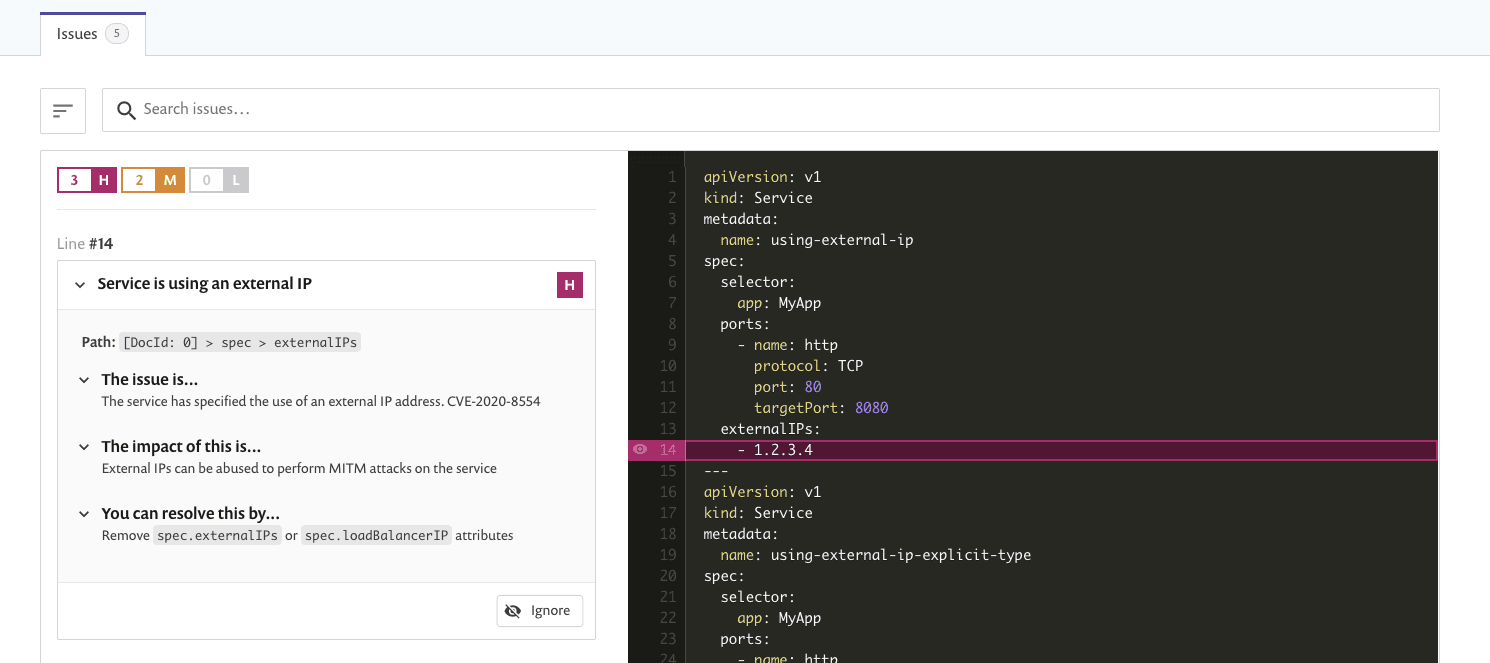
Snyk IaC detects CVE-2020-8554 in a Kubernetes service configuration.
If you are an existing Snyk IaC user, this check is available now and you will automatically see any vulnerable configuration results on your next test from imported Git repositories or by running snyk iac test on the command line. If you are not yet a Snyk IaC user, you can start using Snyk IaC for free and quickly check your Kubernetes configuration definitions to see if you are vulnerable.
If Snyk IaC finds configurations using externalIPs, you should audit your usage to determine your risk. If your clusters are not multi-tenant or you've locked down roles such that most users would not be able to use or patch these settings, you might elect to ignore the result from Snyk IaC and/or tune the Snyk IaC rule _Service is using an external IP_to lower the severity rating. If your workloads depend on externalIPs and you feel you are at risk, you can use admission controllers and/or OPA Gatekeeper to restrict external IP usage based on CIDR lists.
Additional resources:
Kubernetes man in the middle using LoadBalancer or ExternalIPs (CVE-2020-8554)
The New Stack: Unfixable Kubernetes Security Hole Means Potential Man-in-the-Middle Attacks
To see how secure your Kubernetes configuration is and if you are vulnerable to this issue, get started with Snyk for free.
Infraestrutura segura desde o código-fonte
A Snyk automatiza a segurança e a conformidade da IaC em fluxos de trabalho e detecta recursos descompassados e ausentes.





















