Arbitrary code execution in Grunt
21 septembre 2020
0 minutes de lectureWelcome to the Snyk Monthly Vulnerability Profile. In this series, Snyk looks back on the vulnerabilities discovered by or reported to ourSecurity Research Team. We choose one noteworthy vulnerability from the past month and tell the story behind the discovery, research, and disclosure of the vulnerability. We highlight the researchers, developers, and users who are helping identify and remediate vulnerabilities across the open source community.
This month we’re looking at an arbitrary code execution vulnerability discovered in the popular Grunt JavaScript package.
Vulnerability: arbitrary code execution in js-grunt
CVEs assigned: CVE-2020-7729
Snyk Analyst: George Gkitsas
Discovered by: Snyk Research Team
The Snyk research team discovered and disclosed an arbitrary code execution vulnerability in the popular Grunt JavaScript package.
As part of their ongoing efforts to help make open source software more secure, the team identifies patterns of insecure coding practices that can lead to vulnerabilities. As they are able to identify certain patterns they can then craft rules that can be used by tools such as linters to look through popular packages to determine if those vulnerabilities exist.
The arbitrary code execution vulnerability in the Grunt package was identified in this way. So, let’s take a deeper look at the details of the vulnerability, how it was discovered, and how the research team worked with the package maintainer to ensure the vulnerability was remediated.
Digging into the specifics of the arbitrary code execution vulnerability
George Gkitsas was working on an effort to develop new linter rules to discover vulnerabilities in the JavaScript ecosystem. In this case, George was working on detecting when packages use the vulnerable load() function from the js-yaml package to parse a yaml document from a string. A newer, non-vulnerable version of the method called safeLoad() is the recommended way to parse such strings.
George experimented with a linter rule that could be used to identify the pattern within JavaScript packages. By reviewing the results and making revisions to the rule he was able to reduce the number of false-positive detections to an acceptable level where the rule could be added to automated that Snyk runs on a regular basis to identify potentially vulnerable packages in the open source ecosystem.
Snyk regularly selects the top 1,000 most popular packages based on the total number of downloads and scans them for indicators of various vulnerabilities. In this case, the Grunt package was indicated as having a vulnerability due to the use of the load() function. However, just identifying a package with an automated linter isn’t sufficient of course.
The next step is to investigate the finding and confirm that the code is truly vulnerable and that the detection is not a false positive. George was able to easily examine the code that was identified and confirm that it was indeed vulnerable. However, the research team doesn’t stop there. It’s also important to confirm that the vulnerability is actually in code that is reachable and therefore exploitable. Vulnerable code that cannot be effectively exploited isn’t nearly a serious of a risk. So, George built a quick proof of concept and confirmed that the code was indeed vulnerable.
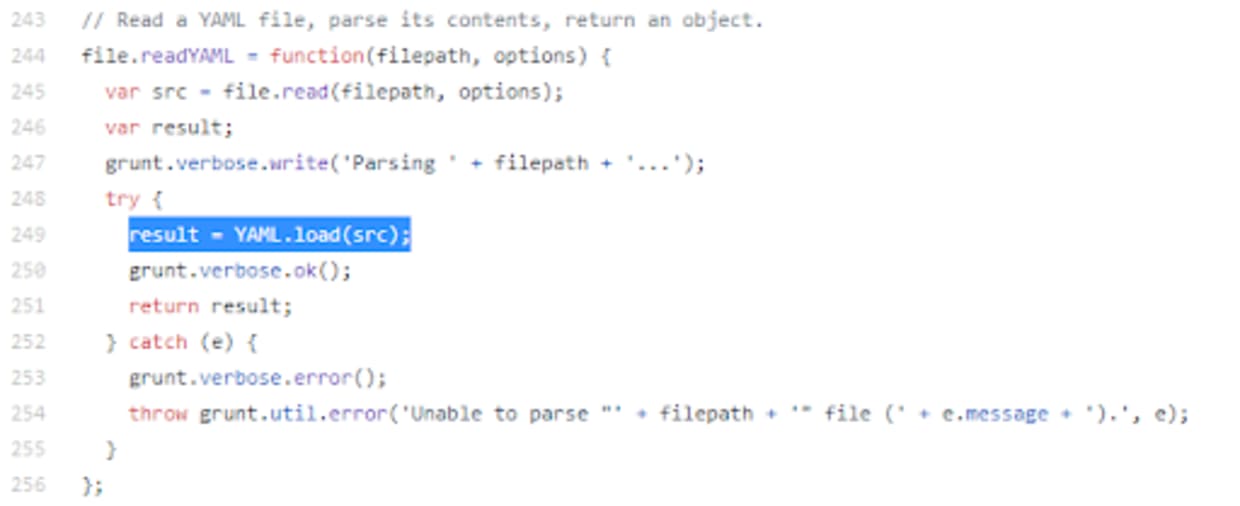
Confirmed: CVE-2020-7729
Upon confirming that the vulnerable code could indeed be exploited, George assigned CVE-2020-7729 to document the vulnerability and reached out to the package maintainer via email. The maintainer responded in under an hour indicating his interest in understanding the details of what Snyk had discovered. He requested additional information and later confirmed back that it was indeed a vulnerability.
However, one element that made this particular situation unique from other vulnerabilities that are typically discovered is that the Grunt package is actually a developer tool. It is a task runner that helps developers automate repetitive tasks in their development processes. So the research team had to consider if a use case existed where someone might actually be able to exploit the code as part of an attack. After considering the ways in which Grunt is used by developers, George was able to confirm with the maintainer that there was a valid attack vector.
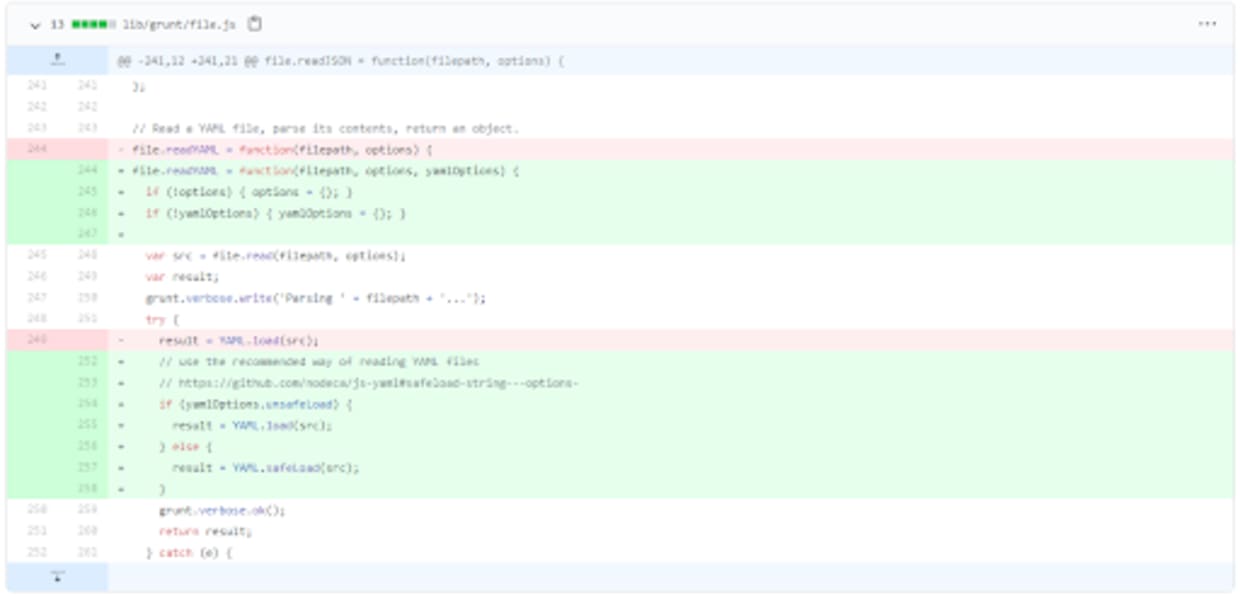
In less than a week, the maintainer released a fix for the Grunt package. Version 1.3.0 was committed to GitHub on August 17, 2020. The new code provides an option whereby the developer can either use the previous load() method or the safeLoad() method depending on the situation and the functionality required.
With the updated version now available, Snyk published the CVE and added it to the Snyk vulnerability database. Over 2,000 projects being monitored by Snyk were identified with the vulnerability and their owners notified.
Snyk's commitment to security
Ultimately, this vulnerability discovery and disclosure highlight how the efforts of the Snyk research team are helping to more quickly and effectively find security issues in open source packages. Researchers were able to identify and confirm not only the vulnerability and its exploitability but also a plausible attack vector that demonstrated the legitimate risk of the vulnerability. This is just part of Snyk’s commitment to empowering developers to stay secure while leveraging open source in their development.
Cap sur la capture du drapeau
Découvrez comment résoudre les défis de capture du drapeau en regardant notre atelier virtuel à la demande.