Want to avoid a data breach? Employ secrets detection
16 septembre 2024
0 minutes de lectureAs a software developer, ensuring the security of your applications is paramount. A crucial part of this task involves managing secrets and employing a secrets detection tool. In this context, secrets refer to sensitive data such as API keys, database credentials, encryption keys, and other confidential information. Their unauthorized access or exposure can lead to catastrophic consequences, including data breaches and severe business losses.
Hardcoded secrets are a common occurrence in development. They offer a quick and easy way to authenticate with external services, databases, or other components that require access control. For instance, it's not uncommon to see API keys or database credentials hardcoded directly into applications, especially during the early stages of development.
This approach may seem like a time-saver, but it introduces a slew of security risks that can easily be avoided through secrets detection.
But what if you could stop a data breach by detecting secrets early during development? Here’s a screenshot of the Snyk InteliJ IDE extension detecting the use of hardcoded secrets and other database credentials used in a JavaScript application:
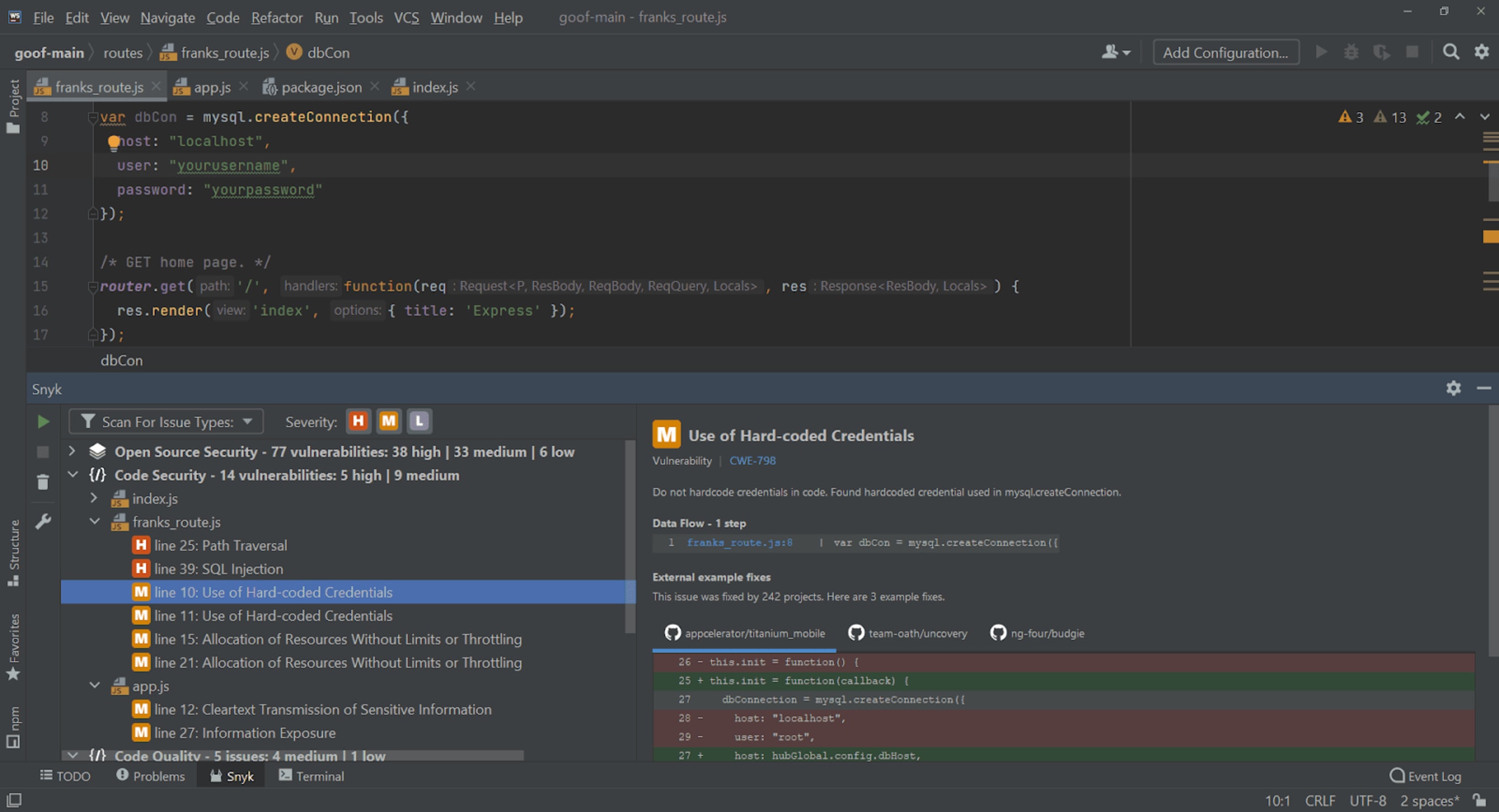
Developers, DevOps, and security personnel continually strive to ensure that secrets are adequately protected, controlled, and monitored throughout their lifecycle. However, as application architectures become more complex and distributed, managing secrets securely and efficiently becomes a significant challenge.
What are secrets in software development?
In the realm of software development, the term "secrets" refers to sensitive data that, if exposed, can lead to unauthorized access and misuse of systems and data. These secrets may include:
Passwords: These are secret phrases or strings of characters used for user authentication to prove identity or gain access to a resource.
API Keys: API keys are unique identifiers used to authenticate a user, developer, or calling program to an API.
Tokens: A token is a piece of data created by the server and can contain information to identify a user, the validity of the token, and the issued time. A good example would be JSON Web Tokens (JWT).
Common mistakes developers make with secrets
Developers often make certain mistakes when dealing with secrets. Here are a few common ones:
Hardcoding secrets: Developers often hardcode secrets into the application's source code. This practice is highly insecure as anyone with access to the codebase can potentially retrieve these secrets.
Improper storage of secrets: Storing secrets in plain text files, configuration files, or databases without any form of encryption is another common mistake.
Insufficient secrets rotation: Regularly changing or rotating secrets is a good security practice. However, many developers overlook this, leaving the same secrets in place for extended periods.
Exploring the consequences of poor secrets management
The consequences of poor secrets management are far-reaching and severe, which highlights the importance of employing secrets detection mechanisms in your software development lifecycle.
Data breaches: The most immediate and dangerous consequence of poor secrets management is the possibility of a data breach. An attacker gaining access to exposed secrets can easily infiltrate your systems, access sensitive data, and even gain control over your infrastructure. For example, they can use API keys to impersonate your application, database credentials to steal or manipulate data, or certificates to break the encryption you have in place. Data breaches can lead to significant financial losses, damage to reputation, and legal consequences.
Regulatory non-compliance: In an era where data privacy and security regulations are becoming increasingly stringent, poor secrets management can lead to non-compliance issues. Violations of regulations such as GDPR, CCPA, and HIPAA can result in hefty fines and legal penalties.
Loss of business competitiveness: Secrets often provide access to proprietary algorithms, business logic, and strategic data. Their exposure can lead to loss of competitive advantage and intellectual property theft.
Here's an example of how easy it is to expose a secret in a Git repository:
Even though the secret was removed in the second commit, it's still present in the repository history and can be retrieved by anyone with access to it.
To avoid these consequences and enhance your application security posture, it is essential to employ secrets detection and management solutions. Tools such as Snyk can help you identify exposed secrets in your codebase early in the development process when developers install the Snyk IDE extension or during the CI/CD pipeline when you integrate Snyk's secrets detection capabilities.
The mechanics of secrets detection
Secrets detection is the process of identifying confidential information or "secrets" such as API keys, passwords, and tokens that could potentially be exposed in your codebase. The exposure or misuse of these secrets could lead to unauthorized access or data breaches.
Secrets detection is crucial in preventing data breaches by identifying and flagging potentially exposed secrets before they can be exploited. If a secret is accidentally committed to a public repository, for example, it can be detected and removed before it is discovered by malicious actors. The key to effective secrets detection is using automated scanning tools that can trawl through your codebase to locate and flag any potential secrets. One way this is accomplished is by using regular expressions (regex) and known patterns to identify potential secrets.
For example, an API key could be detected by a pattern like this:
This is a simplistic example, but the concept is the same: by looking for known patterns, it's possible to identify potential secrets in your code. In real-world scenarios, secrets detection tools like Snyk use far more sophisticated techniques to detect secrets.

Integrating secrets detection into the CI/CD pipeline
To fully leverage the benefits of secrets detection, it should be integrated into your Continuous Integration/Continuous Deployment (CI/CD) pipeline. Doing this lets you catch any potential secrets at the earliest stage of the development process.
For example, you can configure your CI/CD pipeline to run a secrets detection scan every time a new commit is pushed. If any secrets are detected, the pipeline can be set to fail, alerting the team to the issue.
In this example, the snyk code test command runs a secrets detection scan as the first step in the pipeline. If any secrets are detected, the pipeline will fail, and the build and deploy steps will not be run.
Implementing secrets detection with Snyk
Data breaches can be disastrous, harming your reputation and customer trust, and potentially leading to financial penalties. If exposed, secrets, such as API keys, tokens, and passwords, can provide malicious actors with an easy pathway into your system. One effective way to protect against this is to implement secrets detection in your development pipeline. This chapter will guide you on how to employ Snyk's SAST to avoid committing secrets and prevent potential data breaches.
Introduction to Snyk's secrets detection capabilities
Snyk provides robust secrets detection as part of its comprehensive application security offering. It can scan your code repositories for potential secrets and securely notify you of these findings. This feature is built into the Snyk Code product, which provides real-time feedback and suggestions as you code.
The secrets detection feature in Snyk works by using sophisticated patterns and heuristics. These are designed to locate potential secrets in your code that could be exploited by attackers.
Setting up Snyk IDE extensions for real-time secrets detection
To start using Snyk's secrets detection capabilities, you need to set up the Snyk IDE extension. This extension integrates Snyk's features directly into your development environment, providing real-time feedback and suggestions as you code.
To set up the IDE extension:
Go to the Extensions section in your IDE (Visual Studio Code, IntelliJ, etc.)
Search for 'Snyk'
Install the Snyk extension
Start the plugin or restart your IDE
Once the Snyk extension is installed, it will automatically start scanning your code for potential secrets during development.
Best practices for using Snyk to avoid committing secrets
When using Snyk for secrets detection, it is important to follow some best practices.
Never commit secrets to your code repositories. Even if you are using private repositories, there is always a risk of exposure. If a secret is detected by Snyk, make sure to remove it from your code and invalidate the secret if possible.
Use environment variables for storing secrets. Instead of hardcoding secrets into your code, use environment variables. This makes it easier to manage secrets and reduces the risk of them being committed to your code repository.
Regularly scan your code repositories with Snyk. Regular scans help to ensure that no secrets slip through the cracks. You can set up automated scans with Snyk to make this process easier.
Educate your team on the importance of secrets management. Everyone on your team should understand the risks of committing secrets and the importance of using Snyk's secrets detection capabilities.
Following these best practices and using Snyk can significantly reduce the risk of secrets exposure and potential data breaches. Remember, security is not a one-time task but a continuous process. Start your journey to better security by signing up for Snyk here.
Visit Snyk's learn resources for more information about secrets management, tools and best practices
Advanced strategies for secrets management
In the world of application security and software development, managing secrets like API keys, passwords, and certificates is an important task. Effective secrets management aids in compliance and prevents data breaches. Here, we delve into some advanced strategies that can enhance your secrets management efforts.
Employing environment variables for secrets management
One secure method of managing secrets is through the use of environment variables. Environment variables can be utilized in many programming languages and allow you to separate secrets from your codebase. This is crucial for preventing accidental exposure of secrets, especially in open-source projects.
Here's an example in Python:
In this example, SECRET_KEY is an environment variable that stores the secret key. The os.environ.get() function fetches the value of the environment variable. If the environment variable is not found, it returns None.
The use of secrets management tools and services
Leveraging secrets management tools and services can significantly improve the security of your secrets. Tools like HashiCorp Vault and cloud services like AWS Secrets Manager or Azure Key Vault help to securely store and tightly control access to secrets.
Here's an example of how to retrieve a secret from AWS Secrets Manager using AWS SDK for Python:
In this example, my_secret is the name of the secret stored in AWS Secrets Manager. The get_secret_value() function retrieves the secret.
Automating rotation of secrets
Automating the rotation of secrets is a crucial aspect of secrets management. Regularly changing secrets can prevent a potential attacker from using an old secret to gain unauthorized access.
This can be done using secrets management services like AWS Secrets Manager, which supports automatic rotation of secrets for Amazon RDS, Amazon DocumentDB, and Amazon Redshift.
Here's an example of how to configure automatic rotation of secrets in AWS Secrets Manager:
In this example, my_secret is the name of the secret to be rotated, my_lambda_function is the AWS Lambda function that performs the rotation, and AutomaticallyAfterDays is the frequency of rotation in days.
To enhance your application security, consider using a security product like Snyk. Snyk provides a secrets detection feature that can identify secrets in your codebase and prevent them from being exposed. You can sign up for Snyk here.
The strategies discussed here are among many that can enhance secrets management. Combining these with other proactive security measures can significantly bolster your application's defense against threats, ensuring your software development and compliance efforts are secure and effective.
Historical data breaches due to exposed secrets
Data breaches have been a persistent issue in the realm of application security and software development. Exposed secrets, or credentials, are a common cause, leading to unauthorized access and data leaks. In this section, we'll examine some historical data breaches that were the result of exposed secrets, and discuss the lessons learned and the importance of secrets detection.
Uber data breach: The outcome of exposed credentials
In 2016, Uber experienced a significant data breach, exposing the data from 57 million customers and drivers. The cause? Exposed AWS credentials on a private GitHub repository used by its developers. The attackers gained access to these credentials, subsequently accessing Uber's AWS account and downloading a large amount of sensitive data.
This incident underscores the importance of secure credential storage and the risk of storing such secrets in code repositories, even private ones.
Cloudflare: The impact of a stolen Okta auth token
In 2019, Cloudflare was the victim of a major data breach. The breach occurred due to an Okta authentication token stolen from a Cloudflare employee on GitHub. The attacker used this token to access internal Cloudflare systems, exposing sensitive customer data.
This incident illustrates the potential risks of storing secret keys, such as authentication tokens, in code repositories, even if they are considered secure.
Codecov: How hardcoded secrets led to a massive breach
In 2021, Codecov, a platform used by developers for code coverage reports, experienced a significant data breach where attackers exploited a bug in their Docker image creation process. This bug led to the exposure of hardcoded secrets. The attackers used these secrets to modify Codecov's Bash Uploader script, enabling them to export sensitive data from users' environments.
The lesson from this incident? Hardcoded secrets pose a significant risk. To mitigate such risks, it's best to use tools like Snyk for secrets detection and management.
Sumo Logic: Lessons learned
In 2023, Sumo Logic, a cloud-based log management company, announced a security breach involving the compromise of its AWS account, detected on November 3rd, 2023. Despite the unauthorized access via a compromised credential, the company has confirmed that its networks and systems remain unaffected, with customer data securely encrypted. In response, Sumo Logic has secured the affected infrastructure and updated potentially exposed credentials.
Github: The case of an exposed private SSH key
In one of the most ironic incidents, GitHub, the platform widely used for code hosting, experienced a data breach due to an exposed SSH private key. The key was accidentally committed to a public repository and was used by an unauthorized user to access GitHub's internal systems.
This incident, like many of the ones discussed above, highlights the importance of proper secrets management and detection in preventing data breaches.
