-
Notifications
You must be signed in to change notification settings - Fork 9.1k
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Trivy security scan detects a CRITICAL vulnerability in latest Docker image. #7445
Trivy security scan detects a CRITICAL vulnerability in latest Docker image. #7445
Comments
|
Hi @tunguyen9889, Thanks for reporting this. Can I ask you to follow our security policy guidelines next time you report similar issues? Thanks! We'll update |
|
Hi @char0n, Thanks for your quick response! And sorry for missing the guideline for security report. I will take note and follow the process next time. Anyway, you might need to make sure this step https://github.com/swagger-api/swagger-ui/blob/master/Dockerfile#L7 will install latest Best, |
Yep, already tested, and after next release this will be autofixed. So we should be fine just by releasing the new versions this week. |
|
Damn, $ docker run --rm aquasec/trivy:latest --exit-code 0 --severity HIGH,CRITICAL swaggerapi/swagger-ui:v3.52.0Node |
|
Yea, we had to force update nodejs in our custom image to avoid it I think we can enforce the version like this https://superuser.com/a/1058665 |
|
So the Dockerfile commands will be: right? |
|
The Dockerfile command will be: |
|
Thanks! Will try this in next release. |
|
Original error reported in this issue is gone in swagger-ui@4.0.0-rc.0 the same applies for swagger-ui@3.52.1 (that is just being released). But we have additional Unfortunately the command |
|
We had a hack in our internal image to force upgrade all packages to latest version using this command: |
|
Did a following change to our Released this change as Running gives me following output So we're looking fine. I'll do the same changes in v3 release, and we'll be finally able to close this issue. |
|
Results for v3: $ docker run --rm aquasec/trivy:latest --exit-code 0 --severity HIGH,CRITICAL swaggerapi/swagger-ui:v3.52.2Closing the issue as it has been resolved for now. @tunguyen9889 thanks for collaboration on this! |
|
SwaggerEditor@4.x is now green as well: $ docker run --rm aquasec/trivy:latest --exit-code 0 --severity HIGH,CRITICAL swaggerapi/swagger-editor:v4.0.0-rc.0 |
|
Swagger Editor@3.x is now green as well: $ docker run --rm aquasec/trivy:latest --exit-code 0 --severity HIGH,CRITICAL swaggerapi/swagger-editor:v3.18.2 |
|
Thanks @char0n for the fixes! |
* chore(release): cut the v3.50.0 release * chore(deps): bump ws from 6.2.1 to 6.2.2 Bumps [ws](https://github.com/websockets/ws) from 6.2.1 to 6.2.2. - [Release notes](https://github.com/websockets/ws/releases) - [Commits](https://github.com/websockets/ws/commits) --- updated-dependencies: - dependency-name: ws dependency-type: indirect ... Signed-off-by: dependabot[bot] <support@github.com> * chore(deps-dev): bump autoprefixer from 10.2.5 to 10.2.6 Bumps [autoprefixer](https://github.com/postcss/autoprefixer) from 10.2.5 to 10.2.6. - [Release notes](https://github.com/postcss/autoprefixer/releases) - [Changelog](https://github.com/postcss/autoprefixer/blob/main/CHANGELOG.md) - [Commits](postcss/autoprefixer@10.2.5...10.2.6) Signed-off-by: dependabot[bot] <support@github.com> * chore(deps): bump dompurify from 2.2.8 to 2.2.9 Bumps [dompurify](https://github.com/cure53/DOMPurify) from 2.2.8 to 2.2.9. - [Release notes](https://github.com/cure53/DOMPurify/releases) - [Commits](cure53/DOMPurify@2.2.8...2.2.9) --- updated-dependencies: - dependency-name: dompurify dependency-type: direct:production update-type: version-update:semver-patch ... Signed-off-by: dependabot[bot] <support@github.com> * fix(ui): parameter placeholder should only display `name` (swagger-api#7123) * remove `description` from parameter placeholder * chore(deps-dev): bump jest from 26.6.3 to 27.0.4 (swagger-api#7334) Bumps [jest](https://github.com/facebook/jest) from 26.6.3 to 27.0.4. - [Release notes](https://github.com/facebook/jest/releases) - [Changelog](https://github.com/facebook/jest/blob/master/CHANGELOG.md) - [Commits](jestjs/jest@v26.6.3...v27.0.4) --- updated-dependencies: - dependency-name: jest dependency-type: direct:development update-type: version-update:semver-major ... Signed-off-by: dependabot[bot] <support@github.com> Co-authored-by: dependabot[bot] <49699333+dependabot[bot]@users.noreply.github.com> * fix(sample-gen): oas3 form-data object should generate example (swagger-api#7355) * fix(try-it-out): button and inner text spacing (swagger-api#7357) * chore(deps-dev): add sass@1.35.1, remove node-sass (swagger-api#7362) * chore: prep repo for node.js v10 EOL (swagger-api#7359) * feat(oas3): Show file upload for schema binary format (swagger-api#7325) * fix(ux): display actual content type instead of hard-coded application/octet-stream * feat(ux): show file upload when schema has "format: binary", fixes swagger-api#5636 * feat(ux): show file upload when schema has "format: base64" According to swagger-api#7325 (comment) the uploaded file should be converted to base64 automatically. * feat(ux): add cypress tests for displaying an upload button * chore(deps-dev): bump @babel/plugin-proposal-class-properties (swagger-api#7364) Bumps [@babel/plugin-proposal-class-properties](https://github.com/babel/babel/tree/HEAD/packages/babel-plugin-proposal-class-properties) from 7.13.0 to 7.14.5. - [Release notes](https://github.com/babel/babel/releases) - [Changelog](https://github.com/babel/babel/blob/main/CHANGELOG.md) - [Commits](https://github.com/babel/babel/commits/v7.14.5/packages/babel-plugin-proposal-class-properties) --- updated-dependencies: - dependency-name: "@babel/plugin-proposal-class-properties" dependency-type: direct:development update-type: version-update:semver-minor ... Signed-off-by: dependabot[bot] <support@github.com> Co-authored-by: dependabot[bot] <49699333+dependabot[bot]@users.noreply.github.com> * chore(release): cut the v3.51.0 release * chore(deps-dev): bump cypress from 6.7.1 to 7.5.0 (swagger-api#7366) * chore(deps-dev): bump eslint-plugin-mocha from 8.1.0 to 9.0.0 (swagger-api#7336) Bumps [eslint-plugin-mocha](https://github.com/lo1tuma/eslint-plugin-mocha) from 8.1.0 to 9.0.0. - [Release notes](https://github.com/lo1tuma/eslint-plugin-mocha/releases) - [Changelog](https://github.com/lo1tuma/eslint-plugin-mocha/blob/master/CHANGELOG.md) - [Commits](lo1tuma/eslint-plugin-mocha@8.1.0...9.0.0) --- updated-dependencies: - dependency-name: eslint-plugin-mocha dependency-type: direct:development update-type: version-update:semver-major ... Signed-off-by: dependabot[bot] <support@github.com> Co-authored-by: dependabot[bot] <49699333+dependabot[bot]@users.noreply.github.com> * chore(deps-dev): bump lint-staged from 10.5.4 to 11.0.0 (swagger-api#7256) Bumps [lint-staged](https://github.com/okonet/lint-staged) from 10.5.4 to 11.0.0. - [Release notes](https://github.com/okonet/lint-staged/releases) - [Commits](lint-staged/lint-staged@v10.5.4...v11.0.0) Signed-off-by: dependabot[bot] <support@github.com> Co-authored-by: dependabot[bot] <49699333+dependabot[bot]@users.noreply.github.com> * chore(deps-dev): bump release-it from 13.7.1 to 14.10.0 (swagger-api#7367) * also bump @release-it/conventional-changelog to 3.0.1 * chore(deps-dev): bump @babel/plugin-transform-runtime Bumps [@babel/plugin-transform-runtime](https://github.com/babel/babel/tree/HEAD/packages/babel-plugin-transform-runtime) from 7.14.3 to 7.14.5. - [Release notes](https://github.com/babel/babel/releases) - [Changelog](https://github.com/babel/babel/blob/main/CHANGELOG.md) - [Commits](https://github.com/babel/babel/commits/v7.14.5/packages/babel-plugin-transform-runtime) --- updated-dependencies: - dependency-name: "@babel/plugin-transform-runtime" dependency-type: direct:development update-type: version-update:semver-patch ... Signed-off-by: dependabot[bot] <support@github.com> * chore(deps): bump @babel/runtime-corejs3 from 7.14.0 to 7.14.7 Bumps [@babel/runtime-corejs3](https://github.com/babel/babel/tree/HEAD/packages/babel-runtime-corejs3) from 7.14.0 to 7.14.7. - [Release notes](https://github.com/babel/babel/releases) - [Changelog](https://github.com/babel/babel/blob/main/CHANGELOG.md) - [Commits](https://github.com/babel/babel/commits/v7.14.7/packages/babel-runtime-corejs3) --- updated-dependencies: - dependency-name: "@babel/runtime-corejs3" dependency-type: direct:production update-type: version-update:semver-patch ... Signed-off-by: dependabot[bot] <support@github.com> * chore(deps): bump @braintree/sanitize-url from 5.0.1 to 5.0.2 Bumps [@braintree/sanitize-url](https://github.com/braintree/sanitize-url) from 5.0.1 to 5.0.2. - [Release notes](https://github.com/braintree/sanitize-url/releases) - [Changelog](https://github.com/braintree/sanitize-url/blob/main/CHANGELOG.md) - [Commits](braintree/sanitize-url@v5.0.1...v5.0.2) --- updated-dependencies: - dependency-name: "@braintree/sanitize-url" dependency-type: direct:production update-type: version-update:semver-patch ... Signed-off-by: dependabot[bot] <support@github.com> * chore(deps-dev): bump @babel/plugin-proposal-optional-chaining Bumps [@babel/plugin-proposal-optional-chaining](https://github.com/babel/babel/tree/HEAD/packages/babel-plugin-proposal-optional-chaining) from 7.14.2 to 7.14.5. - [Release notes](https://github.com/babel/babel/releases) - [Changelog](https://github.com/babel/babel/blob/main/CHANGELOG.md) - [Commits](https://github.com/babel/babel/commits/v7.14.5/packages/babel-plugin-proposal-optional-chaining) --- updated-dependencies: - dependency-name: "@babel/plugin-proposal-optional-chaining" dependency-type: direct:development update-type: version-update:semver-patch ... Signed-off-by: dependabot[bot] <support@github.com> * chore(ga): cache cypress binary (swagger-api#7377) * chore(ga): cache cypress binary * chore(ga): add cypress_cache_folder * chore(ga): add cache node modules to artifact-bundle * fix(sample-gen): parameter array missing items fallback (swagger-api#7376) * fixes swagger-api#7375 * chore(deps-dev): bump @babel/preset-env from 7.14.2 to 7.14.7 Bumps [@babel/preset-env](https://github.com/babel/babel/tree/HEAD/packages/babel-preset-env) from 7.14.2 to 7.14.7. - [Release notes](https://github.com/babel/babel/releases) - [Changelog](https://github.com/babel/babel/blob/main/CHANGELOG.md) - [Commits](https://github.com/babel/babel/commits/v7.14.7/packages/babel-preset-env) --- updated-dependencies: - dependency-name: "@babel/preset-env" dependency-type: direct:development update-type: version-update:semver-patch ... Signed-off-by: dependabot[bot] <support@github.com> * chore(deps-dev): bump eslint-plugin-import from 2.23.3 to 2.23.4 Bumps [eslint-plugin-import](https://github.com/benmosher/eslint-plugin-import) from 2.23.3 to 2.23.4. - [Release notes](https://github.com/benmosher/eslint-plugin-import/releases) - [Changelog](https://github.com/benmosher/eslint-plugin-import/blob/master/CHANGELOG.md) - [Commits](import-js/eslint-plugin-import@v2.23.3...v2.23.4) --- updated-dependencies: - dependency-name: eslint-plugin-import dependency-type: direct:development update-type: version-update:semver-patch ... Signed-off-by: dependabot[bot] <support@github.com> * chore(deps-dev): bump @babel/cli from 7.14.3 to 7.14.5 Bumps [@babel/cli](https://github.com/babel/babel/tree/HEAD/packages/babel-cli) from 7.14.3 to 7.14.5. - [Release notes](https://github.com/babel/babel/releases) - [Changelog](https://github.com/babel/babel/blob/main/CHANGELOG.md) - [Commits](https://github.com/babel/babel/commits/v7.14.5/packages/babel-cli) --- updated-dependencies: - dependency-name: "@babel/cli" dependency-type: direct:development update-type: version-update:semver-patch ... Signed-off-by: dependabot[bot] <support@github.com> * chore(deps-dev): bump @babel/plugin-proposal-nullish-coalescing-operator Bumps [@babel/plugin-proposal-nullish-coalescing-operator](https://github.com/babel/babel/tree/HEAD/packages/babel-plugin-proposal-nullish-coalescing-operator) from 7.14.2 to 7.14.5. - [Release notes](https://github.com/babel/babel/releases) - [Changelog](https://github.com/babel/babel/blob/main/CHANGELOG.md) - [Commits](https://github.com/babel/babel/commits/v7.14.5/packages/babel-plugin-proposal-nullish-coalescing-operator) --- updated-dependencies: - dependency-name: "@babel/plugin-proposal-nullish-coalescing-operator" dependency-type: direct:development update-type: version-update:semver-patch ... Signed-off-by: dependabot[bot] <support@github.com> * chore(deps-dev): bump @babel/core from 7.14.2 to 7.14.6 Bumps [@babel/core](https://github.com/babel/babel/tree/HEAD/packages/babel-core) from 7.14.2 to 7.14.6. - [Release notes](https://github.com/babel/babel/releases) - [Changelog](https://github.com/babel/babel/blob/main/CHANGELOG.md) - [Commits](https://github.com/babel/babel/commits/v7.14.6/packages/babel-core) --- updated-dependencies: - dependency-name: "@babel/core" dependency-type: direct:development update-type: version-update:semver-patch ... Signed-off-by: dependabot[bot] <support@github.com> * chore(deps-dev): bump @babel/preset-react from 7.13.13 to 7.14.5 Bumps [@babel/preset-react](https://github.com/babel/babel/tree/HEAD/packages/babel-preset-react) from 7.13.13 to 7.14.5. - [Release notes](https://github.com/babel/babel/releases) - [Changelog](https://github.com/babel/babel/blob/main/CHANGELOG.md) - [Commits](https://github.com/babel/babel/commits/v7.14.5/packages/babel-preset-react) --- updated-dependencies: - dependency-name: "@babel/preset-react" dependency-type: direct:development update-type: version-update:semver-minor ... Signed-off-by: dependabot[bot] <support@github.com> * chore(deps-dev): bump @jest/globals from 26.6.2 to 27.0.6 (swagger-api#7393) Bumps [@jest/globals](https://github.com/facebook/jest/tree/HEAD/packages/jest-globals) from 26.6.2 to 27.0.6. - [Release notes](https://github.com/facebook/jest/releases) - [Changelog](https://github.com/facebook/jest/blob/master/CHANGELOG.md) - [Commits](https://github.com/facebook/jest/commits/v27.0.6/packages/jest-globals) --- updated-dependencies: - dependency-name: "@jest/globals" dependency-type: direct:development update-type: version-update:semver-major ... Signed-off-by: dependabot[bot] <support@github.com> Co-authored-by: dependabot[bot] <49699333+dependabot[bot]@users.noreply.github.com> * chore(deps-dev): bump @babel/register from 7.13.16 to 7.14.5 Bumps [@babel/register](https://github.com/babel/babel/tree/HEAD/packages/babel-register) from 7.13.16 to 7.14.5. - [Release notes](https://github.com/babel/babel/releases) - [Changelog](https://github.com/babel/babel/blob/main/CHANGELOG.md) - [Commits](https://github.com/babel/babel/commits/v7.14.5/packages/babel-register) --- updated-dependencies: - dependency-name: "@babel/register" dependency-type: direct:development update-type: version-update:semver-minor ... Signed-off-by: dependabot[bot] <support@github.com> * chore(deps-dev): bump eslint from 7.27.0 to 7.29.0 Bumps [eslint](https://github.com/eslint/eslint) from 7.27.0 to 7.29.0. - [Release notes](https://github.com/eslint/eslint/releases) - [Changelog](https://github.com/eslint/eslint/blob/master/CHANGELOG.md) - [Commits](eslint/eslint@v7.27.0...v7.29.0) --- updated-dependencies: - dependency-name: eslint dependency-type: direct:development update-type: version-update:semver-minor ... Signed-off-by: dependabot[bot] <support@github.com> * chore(deps-dev): bump nightwatch from 1.6.4 to 1.7.7 Bumps [nightwatch](https://github.com/nightwatchjs/nightwatch) from 1.6.4 to 1.7.7. - [Release notes](https://github.com/nightwatchjs/nightwatch/releases) - [Commits](nightwatchjs/nightwatch@v1.6.4...v1.7.7) --- updated-dependencies: - dependency-name: nightwatch dependency-type: direct:development update-type: version-update:semver-minor ... Signed-off-by: dependabot[bot] <support@github.com> * chore(release): cut the v3.51.1 release * chore(deps-dev): bump jest from 27.0.4 to 27.0.6 Bumps [jest](https://github.com/facebook/jest) from 27.0.4 to 27.0.6. - [Release notes](https://github.com/facebook/jest/releases) - [Changelog](https://github.com/facebook/jest/blob/master/CHANGELOG.md) - [Commits](jestjs/jest@v27.0.4...v27.0.6) --- updated-dependencies: - dependency-name: jest dependency-type: direct:development update-type: version-update:semver-patch ... Signed-off-by: dependabot[bot] <support@github.com> * chore(deps-dev): bump webpack-cli from 4.7.0 to 4.7.2 Bumps [webpack-cli](https://github.com/webpack/webpack-cli) from 4.7.0 to 4.7.2. - [Release notes](https://github.com/webpack/webpack-cli/releases) - [Changelog](https://github.com/webpack/webpack-cli/blob/master/CHANGELOG.md) - [Commits](https://github.com/webpack/webpack-cli/compare/webpack-cli@4.7.0...webpack-cli@4.7.2) --- updated-dependencies: - dependency-name: webpack-cli dependency-type: direct:development update-type: version-update:semver-patch ... Signed-off-by: dependabot[bot] <support@github.com> * chore(deps-dev): bump mini-css-extract-plugin from 1.6.0 to 1.6.2 Bumps [mini-css-extract-plugin](https://github.com/webpack-contrib/mini-css-extract-plugin) from 1.6.0 to 1.6.2. - [Release notes](https://github.com/webpack-contrib/mini-css-extract-plugin/releases) - [Changelog](https://github.com/webpack-contrib/mini-css-extract-plugin/blob/master/CHANGELOG.md) - [Commits](webpack-contrib/mini-css-extract-plugin@v1.6.0...v1.6.2) --- updated-dependencies: - dependency-name: mini-css-extract-plugin dependency-type: direct:development update-type: version-update:semver-patch ... Signed-off-by: dependabot[bot] <support@github.com> * chore(deps-dev): bump postcss from 8.2.15 to 8.3.5 Bumps [postcss](https://github.com/postcss/postcss) from 8.2.15 to 8.3.5. - [Release notes](https://github.com/postcss/postcss/releases) - [Changelog](https://github.com/postcss/postcss/blob/main/CHANGELOG.md) - [Commits](postcss/postcss@8.2.15...8.3.5) --- updated-dependencies: - dependency-name: postcss dependency-type: direct:development update-type: version-update:semver-minor ... Signed-off-by: dependabot[bot] <support@github.com> * ci(dependabot): disable dependabot until V4 RC * fix(deps): bump swagger-client to v3.14.1 (swagger-api#7440) This sets minimum Node.js version to >=12.4 and fixes problem with swagger-ui.js build fragment. Refs swagger-api#7436 * chore(release): cut the v3.51.2 release * chore(deps-dev): bump cypress from 7.5.0 to 7.7.0 Bumps [cypress](https://github.com/cypress-io/cypress) from 7.5.0 to 7.7.0. - [Release notes](https://github.com/cypress-io/cypress/releases) - [Changelog](https://github.com/cypress-io/cypress/blob/develop/.releaserc.base.js) - [Commits](cypress-io/cypress@v7.5.0...v7.7.0) --- updated-dependencies: - dependency-name: cypress dependency-type: direct:development update-type: version-update:semver-minor ... Signed-off-by: dependabot[bot] <support@github.com> * chore(package): allow swagger-client version ranges (swagger-api#7441) * ci: disable dependabot merge workflow Refs swagger-api#7341 * feat(js-yaml): update our main YAML parser to v4.1.0 Closes swagger-api#6804 * chore(deps): bump swagger-client to v3.15.0 * chore(release): cut the v3.52.0 release * chore(deps-dev): bump eslint-plugin-react from 7.23.2 to 7.24.0 Bumps [eslint-plugin-react](https://github.com/yannickcr/eslint-plugin-react) from 7.23.2 to 7.24.0. - [Release notes](https://github.com/yannickcr/eslint-plugin-react/releases) - [Changelog](https://github.com/yannickcr/eslint-plugin-react/blob/master/CHANGELOG.md) - [Commits](jsx-eslint/eslint-plugin-react@v7.23.2...v7.24.0) --- updated-dependencies: - dependency-name: eslint-plugin-react dependency-type: direct:development update-type: version-update:semver-minor ... Signed-off-by: dependabot[bot] <support@github.com> * build(docker): fix docker image Node.js security issue Refs swagger-api#7445 * ci: use max Node.js version of 16.8 Node.js version 16.9 relesed 3 days ago gives cryptic errors. We'll wait untill this is fixed upstream. * fix(security): bump swagger-client to v3.16.1 Refs swagger-api#7473 * fix(build-security): do not expose hostname to build framents (swagger-api#7491) Refs swagger-api#7446 * chore(release): cut the v3.52.1 release * chore(deps-dev): bump chromedriver from 90.0.1 to 91.0.1 Bumps [chromedriver](https://github.com/giggio/node-chromedriver) from 90.0.1 to 91.0.1. - [Release notes](https://github.com/giggio/node-chromedriver/releases) - [Commits](giggio/node-chromedriver@90.0.1...91.0.1) --- updated-dependencies: - dependency-name: chromedriver dependency-type: direct:development update-type: version-update:semver-major ... Signed-off-by: dependabot[bot] <support@github.com> * chore(deps): bump url-parse from 1.5.1 to 1.5.2 Bumps [url-parse](https://github.com/unshiftio/url-parse) from 1.5.1 to 1.5.2. - [Release notes](https://github.com/unshiftio/url-parse/releases) - [Commits](unshiftio/url-parse@1.5.1...1.5.2) --- updated-dependencies: - dependency-name: url-parse dependency-type: direct:production ... Signed-off-by: dependabot[bot] <support@github.com> * fix(security): fix security issue in prismjs dep (swagger-api#7493) Refs swagger-api#7492 * fix(Dockerfile): fix security issue in docker image Refs swagger-api#7445 * chore(release): cut the v3.52.2 release * fix(try-it-out): fix the width of image responses (swagger-api#7495) Refs swagger-api#5578 * fix(sample-gen): generate the correct number of properties (swagger-api#7432) This commit fixes correct number of additionalProperties when minProperties is used. * docs(configuration): fix wrong property name languagesMask property is not recognized by SwaggerUI. languages property is recognized propertly. Refs swagger-api#7505 * chore(security): fix security vulnerabilities in dev deps (swagger-api#7510) * fix(a11n): provide proper a11n for response example tabs (swagger-api#7464) - Update tabs to use <button> elements instead of <a> - Add aria roles for tablist, tabs, and tabpanel - Add aria attributes for additional a11y compliance and screen reader accessibility - Replace ids with data-name attribute for tabpanels - Add cypress test 7463 and update swos-63 - Move tabs test file to tests/a11y directory - Rename test file to be more descriptive of what is being tested. - Add id attributes to both tabs and tabpanels to leverage aria-controls and aria-labelledby attributes Co-authored-by: Calvin Gonzalez <calvin.gonzalez@oddball.io> Co-authored-by: Vladimir Gorej <vladimir.gorej@gmail.com> Closes swagger-api#7463 Refs swagger-api#7350 * chore(docker): automatic updates + nightly security check (swagger-api#7515) Refs swagger-api#7514 * chore(release): cut the v3.52.3 release * fix(ux): update the buttons of the example tabs to be displayed as links (swagger-api#7517) Fixes small visual regression introduced in swagger-api#7464. Refs swagger-api#7464 * chore(deps-dev): fix security vulnerabilities in dep tree * refactor: remove IE7 CSS hack (swagger-api#7526) Remove IE specific start hack: https://stackoverflow.com/a/14927670/808699 that was targeting IE 5.5 to 7. * fix(paths): break long paths with <wbr> (swagger-api#7516) - use <wbr> instead of ZERO-WIDTH SPACE (U+200B) to break segments - remove no-longer-needed onCopyCapture listener which previously stripped ZWSPs - update's deep-link.jsx's `text` prop type to accept `PropType.node` to allow the above. Closes swagger-api#7513 Co-authored-by: Vladimir Gorej <vladimir.gorej@gmail.com> * fix(UI): correct width of HTTP request method names (swagger-api#7527) Closes swagger-api#7479 * fix: fix issue with highlight code scrolling causing console error (swagger-api#7497) (swagger-api#7519) Co-authored-by: Mahtis Michel <mathis.michel@outlook.de> Refs swagger-api#7497 * refactor(highlight-code): declare properties explicitly Refs swagger-api#7497 * fix: rename request snippets configuration props (swagger-api#7535) Closes swagger-api#7534 * fix: remove redundant whitespaces in API key auth popup (swagger-api#7538) * chore(release): cut the v3.52.4 release * fix(highlight-code): handle mousewheel events properly (swagger-api#7554) SyntaxHighlighter component doesn't support ref. We had to use different approach to finds it's DOM Node using ref of the root Node of the render tree for HighlightCode component. Refs swagger-api#7497 * chore(release): cut the v3.52.5 release * fix(ui): eliminate copy button icon misaligned in Firefox (swagger-api#7542) Closes swagger-api#7481 * chore(deps): bump vm2 from 3.9.3 to 3.9.5 (swagger-api#7565) Bumps [vm2](https://github.com/patriksimek/vm2) from 3.9.3 to 3.9.5. - [Release notes](https://github.com/patriksimek/vm2/releases) - [Changelog](https://github.com/patriksimek/vm2/blob/master/CHANGELOG.md) - [Commits](patriksimek/vm2@3.9.3...3.9.5) --- updated-dependencies: - dependency-name: vm2 dependency-type: indirect ... Signed-off-by: dependabot[bot] <support@github.com> Co-authored-by: dependabot[bot] <49699333+dependabot[bot]@users.noreply.github.com> Co-authored-by: Vladimir Gorej <vladimir.gorej@gmail.com> * chore(deps): bump DOMPurify to latest version v2.3.3 (swagger-api#7572) * docs(LICENSE): apply Apache 2.0 License correctly (swagger-api#7574) Closes swagger-api#6635 * chore(deps): fix security vulnerabilities * chore(deps): update react & react-dom to v17.0.2 Refs swagger-api#7341 * test(just-test-in-node): fix npm script Before the script exited with error thrown. Enzyme was updated to v3.11.0 and custom adapter for react@17 is used. Refs swagger-api#7341 * test(test:unit-jest): fix all failing tests for this script We needed to align new cheerio and enzyme APIS with tests. Refs swagger-api#7341 * test(e2e-cypress): fix all failing tests for this script Problem was with an obsolete and no longer supported Perf tool for React. Reference to it have been removed. Refs swagger-api#7341 * chore(deps-dev): update redux-immutable to v4.0.0 Refs swagger-api#7341 * chore(deps): update redux-immutable-pure-component to 2.2.0 Refs swagger-api#7341 * chore(deps): update redux to v4.1.0 Refs swagger-api#7341 * chore(deps): update react-redux to v7.2.4 * chore(deps): update react-inspector to v5.1.1 Refs swagger-api#7341 * build(swagger-ui-react): align version of React with SwaggerUI Refs swagger-api#7341 * chore(package-lock): update lock file to reflect deps * chore(release): prepare release scripts for v4 beta pre-release * chore(package): tweak automated-release script #1 * chore(release): cut the v4.0.0-beta.0 release * chore(release-it): allow releasing consecutive beta releases Refs swagger-api#7341 * chore(deps): replace react-motion library for obj. literal Refs swagger-api#7341 * chore(deps-dev): update react-test-renderer to v17.0.2 Refs swagger-api#7341 * chore(security): fix transitive deps using npm audit Refs swagger-api#7341 * chore(package-lock): add integrity check info Refs swagger-api#7341 * chore(deps): replace @kyleshockey/* deps with originals @kyleshockey/object-assign-deep - replaced by lodash/merge. If behavior not be compatible well use lodash/mergeWith. @kyleshockey/xml - by installing stream library directly, we can use origin xml library without the fork. Refs swagger-api#7341 * chore(deps): update react-debounce-input to v3.2.4 Refs #swagger-api#7341 * test: remove support for nighwatch e2e tests We still ratain nighwatch test cases and need to port them to Cypress. Test cases were broken and did not run any more. Refs swagger-api#7341 * chore(release): cut the v4.0.0-beta.1 release * chore(package-lock): transform to lockfileVersion=2 * fix(deps): update swagger-client to v3.14.1 Refs swagger-api#7341 Refs swagger-api#7436 * chore(deps): rebase on top of master Refs swagger-api#7379 * chore(package-lock): regenerate to fix corruption Refs swagger-api#7341 * chore(deps): pickup deps changes from master Refs swagger-api#7341 * chore: bump to v4.0.0-beta.2 * chore(release): cut the v4.0.0-beta.3 release * refactor: prefix lifecycle methods with UNSAFE_ Refs swagger-api#7341 * fix(servers): compensate when server list contains a null value Refs swagger-api/swagger-editor#2761 Refs swagger-api/swagger-editor#2710 Refs swagger-api#7341 * chore(release): cut the v4.0.0-beta.4 release * fix(security): bump swagger-client to v3.16.1 Refs swagger-api#7473 * chore(release): end beta phase and start RC * chore(release): cut the v4.0.0-rc.0 release * chore(release): continue with RC pre-releases * chore(deps): bump url-parse from 1.5.1 to 1.5.3 Refs swagger-api#7492 * fix(security): fix security issue in prismjs dep Refs swagger-api#7492 * chore(deps-dev): fix all fixable security issues in dev deps Refs swagger-api#7492 * chore(release): cut the v4.0.0-rc.1 release * chore(deps): remove unused stream library Refs swagger-api#7499 Refs swagger-api#7341 * build(webpack): remove duplicates from the build Refs swagger-api#7341 * chore(release): cut the v4.0.0-rc.2 release * refactor(highlight-code): add UNSAFE prefix for lifecycle methods Refs swagger-api#7497 * fix(param-body): fix loosing focus in Try It when typing (swagger-api#7548) Originally reported as SWOS-418 Closes swagger-api#7477 * chore(release): cut the v4.0.0-rc.3 release * feat: allow using functional components with hooks * fix(highlight-code): handle mousewheel events properly SyntaxHighlighter component doesn't support ref. We had to use different approach to finds it's DOM Node using ref of the root Node of the render tree for HighlightCode component. Refs swagger-api#7497 * fix(root-inject): handle errors in functional components properly * chore(deps): update swagger-client to 3.17.0 version * chore(nvm): use recommended version of Node.js@16.8.x * chore(deps): fix all security vulnerabilities Refs swagger-api#7341 * chore(deps-dev): update husky to 7.0.2 version * chore(release): cut the v4.0.0-rc.4 release * chore(deps): bump DOMPurify to latest version v2.3.3 * chore(deps): fix security vulnerabilities * ci: enable dependabot after v4 effort * chore(release): return release scripts back to original * chore(deps-dev): bump open from 8.2.1 to 8.4.0 Bumps [open](https://github.com/sindresorhus/open) from 8.2.1 to 8.4.0. - [Release notes](https://github.com/sindresorhus/open/releases) - [Commits](sindresorhus/open@v8.2.1...v8.4.0) --- updated-dependencies: - dependency-name: open dependency-type: direct:development update-type: version-update:semver-minor ... Signed-off-by: dependabot[bot] <support@github.com> * chore(release): cut the v4.0.0 release * chore(deps): bump nginx from 1.21-alpine to 1.21.3-alpine (swagger-api#7585) Bumps nginx from 1.21-alpine to 1.21.3-alpine. --- updated-dependencies: - dependency-name: nginx dependency-type: direct:production ... Signed-off-by: dependabot[bot] <support@github.com> Co-authored-by: dependabot[bot] <49699333+dependabot[bot]@users.noreply.github.com> Co-authored-by: Vladimir Gorej <vladimir.gorej@gmail.com> * chore(deps-dev): bump babel-loader from 8.2.2 to 8.2.3 Bumps [babel-loader](https://github.com/babel/babel-loader) from 8.2.2 to 8.2.3. - [Release notes](https://github.com/babel/babel-loader/releases) - [Changelog](https://github.com/babel/babel-loader/blob/main/CHANGELOG.md) - [Commits](babel/babel-loader@v8.2.2...v8.2.3) --- updated-dependencies: - dependency-name: babel-loader dependency-type: direct:development update-type: version-update:semver-patch ... Signed-off-by: dependabot[bot] <support@github.com> * chore(deps-dev): bump @babel/register from 7.14.5 to 7.16.0 Bumps [@babel/register](https://github.com/babel/babel/tree/HEAD/packages/babel-register) from 7.14.5 to 7.16.0. - [Release notes](https://github.com/babel/babel/releases) - [Changelog](https://github.com/babel/babel/blob/main/CHANGELOG.md) - [Commits](https://github.com/babel/babel/commits/v7.16.0/packages/babel-register) --- updated-dependencies: - dependency-name: "@babel/register" dependency-type: direct:development update-type: version-update:semver-minor ... Signed-off-by: dependabot[bot] <support@github.com> * chore(dependabot): limit PRs to max 3 * chore(deps-dev): bump postcss from 8.3.5 to 8.3.11 Bumps [postcss](https://github.com/postcss/postcss) from 8.3.5 to 8.3.11. - [Release notes](https://github.com/postcss/postcss/releases) - [Changelog](https://github.com/postcss/postcss/blob/main/CHANGELOG.md) - [Commits](postcss/postcss@8.3.5...8.3.11) --- updated-dependencies: - dependency-name: postcss dependency-type: direct:development update-type: version-update:semver-patch ... Signed-off-by: dependabot[bot] <support@github.com> * chore(deps-dev): bump git-describe from 4.0.4 to 4.1.0 Bumps [git-describe](https://github.com/tvdstaaij/node-git-describe) from 4.0.4 to 4.1.0. - [Release notes](https://github.com/tvdstaaij/node-git-describe/releases) - [Changelog](https://github.com/tvdstaaij/node-git-describe/blob/master/CHANGELOG.md) - [Commits](tvdstaaij/node-git-describe@v4.0.4...v4.1.0) --- updated-dependencies: - dependency-name: git-describe dependency-type: direct:development update-type: version-update:semver-minor ... Signed-off-by: dependabot[bot] <support@github.com> * chore(deps-dev): bump css-loader from 5.2.6 to 5.2.7 Bumps [css-loader](https://github.com/webpack-contrib/css-loader) from 5.2.6 to 5.2.7. - [Release notes](https://github.com/webpack-contrib/css-loader/releases) - [Changelog](https://github.com/webpack-contrib/css-loader/blob/master/CHANGELOG.md) - [Commits](webpack-contrib/css-loader@v5.2.6...v5.2.7) --- updated-dependencies: - dependency-name: css-loader dependency-type: direct:development update-type: version-update:semver-patch ... Signed-off-by: dependabot[bot] <support@github.com> * ci(deps): sqash & merge dependabot PRs (swagger-api#7596) * chore(deps-dev): bump eslint-plugin-import from 2.23.4 to 2.25.2 (swagger-api#7605) * chore(deps-dev): bump lint-staged from 11.0.0 to 11.2.6 (swagger-api#7606) * docs(README): add v4.0.0 into compatiblity table (swagger-api#7604) * chore(deps-dev): bump expect from 1.20.2 to 27.3.1 Closes swagger-api#7607 * fix(servers): prevent UI crash when chaning Server with variables Closes swagger-api#7525 * chore(release): cut the v4.0.1 release * fix(highlight-code): fix regression code highlight behavior Refs swagger-api#7603 * chore(deps-dev): bump sinon from 12.0.0 to 12.0.1 (swagger-api#7616) * fix: add source map of css file to swagger-ui-react (swagger-api#7601) Fixes source map of css file missing in swagger-ui-react. The source map is referenced in ./dist/swagger-ui.css, but as it does not exist in the final package creates errors in our tooling. * feat(swagger-ui-react): add showExtensions option (swagger-api#7563) Closes swagger-api#5892 * fix(swagger-ui-react): add showExtension propType Refs swagger-api#5892 * docs(configuration): document requestSnippetsEnabled config option Along with that fix formatting of request snippet value. * feat(swagger-ui-react): add request snippets configuration (swagger-api#7536) Closes swagger-api#7523 * chore(deps-dev): bump @wojtekmaj/enzyme-adapter-react-17 (swagger-api#7622) * feat(swagger-ui-react): add support of filter prop (swagger-api#7547) Co-authored-by: Mahtis Michel <mathis.michel@outlook.de> Co-authored-by: Vladimir Gorej <vladimir.gorej@gmail.com> Closes swagger-api#7546 * chore(release): cut the v4.1.0 release * chore(deps): bump react-copy-to-clipboard from 5.0.3 to 5.0.4 (swagger-api#7623) * chore(deps-dev): bump @babel/plugin-proposal-class-properties (swagger-api#7621) * chore(deps-dev): bump eslint-plugin-react from 7.24.0 to 7.27.0 Bumps [eslint-plugin-react](https://github.com/yannickcr/eslint-plugin-react) from 7.24.0 to 7.27.0. - [Release notes](https://github.com/yannickcr/eslint-plugin-react/releases) - [Changelog](https://github.com/yannickcr/eslint-plugin-react/blob/master/CHANGELOG.md) - [Commits](jsx-eslint/eslint-plugin-react@v7.24.0...v7.27.0) --- updated-dependencies: - dependency-name: eslint-plugin-react dependency-type: direct:development update-type: version-update:semver-minor ... Signed-off-by: dependabot[bot] <support@github.com> * chore(deps): fix security vulneraiblity in json-merger * chore(deps): bump @babel/runtime-corejs3 from 7.14.8 to 7.16.3 (swagger-api#7636) * chore(deps): bump nginx from 1.21.3-alpine to 1.21.4-alpine Bumps nginx from 1.21.3-alpine to 1.21.4-alpine. --- updated-dependencies: - dependency-name: nginx dependency-type: direct:production update-type: version-update:semver-patch ... Signed-off-by: dependabot[bot] <support@github.com> * ci: optimize speed of CI (swagger-api#7649) Refs swagger-api#7627 * chore(deps-dev): bump json-server from 0.16.3 to 0.17.0 (swagger-api#7651) * chore(deps-dev): bump cssnano from 5.0.4 to 5.0.11 (swagger-api#7652) * chore(deps-dev): bump eslint-plugin-jest from 24.4.0 to 25.2.4 (swagger-api#7629) Bumps [eslint-plugin-jest](https://github.com/jest-community/eslint-plugin-jest) from 24.4.0 to 25.2.4. - [Release notes](https://github.com/jest-community/eslint-plugin-jest/releases) - [Changelog](https://github.com/jest-community/eslint-plugin-jest/blob/main/CHANGELOG.md) - [Commits](jest-community/eslint-plugin-jest@v24.4.0...v25.2.4) --- updated-dependencies: - dependency-name: eslint-plugin-jest dependency-type: direct:development update-type: version-update:semver-major ... Signed-off-by: dependabot[bot] <support@github.com> Co-authored-by: dependabot[bot] <49699333+dependabot[bot]@users.noreply.github.com> Co-authored-by: Vladimir Gorej <vladimir.gorej@gmail.com> * chore(deps-dev): bump @babel/plugin-proposal-nullish-coalescing-operator (swagger-api#7656) * chore(deps-dev): bump @babel/plugin-transform-runtime (swagger-api#7655) * chore(deps-dev): bump cypress from 7.7.0 to 9.0.0 Bumps [cypress](https://github.com/cypress-io/cypress) from 7.7.0 to 9.0.0. - [Release notes](https://github.com/cypress-io/cypress/releases) - [Changelog](https://github.com/cypress-io/cypress/blob/develop/.releaserc.base.js) - [Commits](cypress-io/cypress@v7.7.0...v9.0.0) --- updated-dependencies: - dependency-name: cypress dependency-type: direct:development update-type: version-update:semver-major ... Signed-off-by: dependabot[bot] <support@github.com> * chore(deps-dev): bump autoprefixer from 10.3.1 to 10.4.0 (swagger-api#7659) * chore(deps-dev): bump @babel/eslint-parser from 7.14.3 to 7.16.3 (swagger-api#7660) * chore(deps): bump redux from 4.1.0 to 4.1.2 (swagger-api#7663) * chore(deps-dev): bump @commitlint/config-conventional Bumps [@commitlint/config-conventional](https://github.com/conventional-changelog/commitlint/tree/HEAD/@commitlint/config-conventional) from 12.1.4 to 15.0.0. - [Release notes](https://github.com/conventional-changelog/commitlint/releases) - [Changelog](https://github.com/conventional-changelog/commitlint/blob/master/@commitlint/config-conventional/CHANGELOG.md) - [Commits](https://github.com/conventional-changelog/commitlint/commits/v15.0.0/@commitlint/config-conventional) --- updated-dependencies: - dependency-name: "@commitlint/config-conventional" dependency-type: direct:development update-type: version-update:semver-major ... Signed-off-by: dependabot[bot] <support@github.com> * chore(deps-dev): bump husky from 7.0.2 to 7.0.4 (swagger-api#7664) Bumps [husky](https://github.com/typicode/husky) from 7.0.2 to 7.0.4. - [Release notes](https://github.com/typicode/husky/releases) - [Commits](typicode/husky@v7.0.2...v7.0.4) --- updated-dependencies: - dependency-name: husky dependency-type: direct:development update-type: version-update:semver-patch ... Signed-off-by: dependabot[bot] <support@github.com> Co-authored-by: dependabot[bot] <49699333+dependabot[bot]@users.noreply.github.com> Co-authored-by: Vladimir Gorej <vladimir.gorej@gmail.com> * chore(deps-dev): fix security vuln. in react-syntax-highlighter * fix: introduce Error Boundaries to handle unexpected failures (swagger-api#7671) Two new components have been updated via plugin system: ErrorBoundary and Fallback. These components can be overridden by user plugins. Refs swagger-api#7647 * chore(deps): allow updating patch and minor version for highlihter * chore(release): cut the v4.1.1 release * fix: request JumpToPath components always as container Refs swagger-api/swagger-editor#2099 * chore(release): cut the v4.1.2 release * chore(deps-dev): bump @commitlint/cli from 12.1.4 to 15.0.0 (swagger-api#7678) Bumps [@commitlint/cli](https://github.com/conventional-changelog/commitlint/tree/HEAD/@commitlint/cli) from 12.1.4 to 15.0.0. - [Release notes](https://github.com/conventional-changelog/commitlint/releases) - [Changelog](https://github.com/conventional-changelog/commitlint/blob/master/@commitlint/cli/CHANGELOG.md) - [Commits](https://github.com/conventional-changelog/commitlint/commits/v15.0.0/@commitlint/cli) --- updated-dependencies: - dependency-name: "@commitlint/cli" dependency-type: direct:development update-type: version-update:semver-major ... Signed-off-by: dependabot[bot] <support@github.com> Co-authored-by: dependabot[bot] <49699333+dependabot[bot]@users.noreply.github.com> Co-authored-by: Vladimir Gorej <vladimir.gorej@gmail.com> * chore(deps-dev): bump source-map-support from 0.5.19 to 0.5.21 (swagger-api#7681) * chore(deps-dev): bump @babel/plugin-proposal-optional-chaining (swagger-api#7682) * chore(deps-dev): bump eslint-plugin-import from 2.25.2 to 2.25.3 (swagger-api#7683) * chore(deps-dev): bump less from 4.1.1 to 4.1.2 (swagger-api#7685) * fix(security): disable reading config params from URL search params (swagger-api#7697) Reading configuration parameters from URL search params is by default no longer enabled. To re-enable it, set queryConfigEnabled configuration parameter to true. Functionally, this is a breaking change, but given we're just providing a security vulnerability patch we're considering this a PATCH version bump only. Refs swagger-api#4872 Refs GHSA-qrmm-w75w-3wpx * chore(release): cut the v4.1.3 release * R11DT-2620 - Update url-parse to 1.5.10 (#167) * update url-parse to 1.5.10 * update dist folder: npm run build result * Upgrade dompurify to 3.1.3 (#170) --------- Signed-off-by: dependabot[bot] <support@github.com> Co-authored-by: swagger-bot <swagger-bot@smartbear.com> Co-authored-by: dependabot[bot] <49699333+dependabot[bot]@users.noreply.github.com> Co-authored-by: Vasilev Pyotr <vahpetr@gmail.com> Co-authored-by: Tim Lai <timothy.lai@gmail.com> Co-authored-by: Andreas Grub <grub@posteo.de> Co-authored-by: Vladimir Gorej <vladimir.gorej@gmail.com> Co-authored-by: Helen Kosova <hkosova@users.noreply.github.com> Co-authored-by: Calvin Gonzalez <asuma76@gmail.com> Co-authored-by: Dominik Henneke <dominik.henneke@sda-se.com> Co-authored-by: silverwind <me@silverwind.io> Co-authored-by: Mingwei Samuel <mingwei.samuel@gmail.com> Co-authored-by: twjasa <twjasa@gmail.com> Co-authored-by: kristina-kovacikova <47686623+kristina-kovacikova@users.noreply.github.com> Co-authored-by: Mahtis Michel <mathis.michel@outlook.de> Co-authored-by: Sviataslau Hankovich <svyatoslav.hankovich@gmail.com> Co-authored-by: GhBogdan97 <36417662+GhBogdan97@users.noreply.github.com> Co-authored-by: Costas Kotsokalis <55377146+cksnp@users.noreply.github.com> Co-authored-by: Florian Dreier <dreier.florian@gmail.com> Co-authored-by: glebbash <glebbash@gmail.com> Co-authored-by: Andriy Semenyuk <andrewcem7@gmail.com> Co-authored-by: João Almeida Santos <joao.almeida.santos@outsystems.com> Co-authored-by: OS-alexandretome <alexandre.tome@outsystems.com>
* chore(release): cut the v3.50.0 release * chore(deps): bump ws from 6.2.1 to 6.2.2 Bumps [ws](https://github.com/websockets/ws) from 6.2.1 to 6.2.2. - [Release notes](https://github.com/websockets/ws/releases) - [Commits](https://github.com/websockets/ws/commits) --- updated-dependencies: - dependency-name: ws dependency-type: indirect ... Signed-off-by: dependabot[bot] <support@github.com> * chore(deps-dev): bump autoprefixer from 10.2.5 to 10.2.6 Bumps [autoprefixer](https://github.com/postcss/autoprefixer) from 10.2.5 to 10.2.6. - [Release notes](https://github.com/postcss/autoprefixer/releases) - [Changelog](https://github.com/postcss/autoprefixer/blob/main/CHANGELOG.md) - [Commits](postcss/autoprefixer@10.2.5...10.2.6) Signed-off-by: dependabot[bot] <support@github.com> * chore(deps): bump dompurify from 2.2.8 to 2.2.9 Bumps [dompurify](https://github.com/cure53/DOMPurify) from 2.2.8 to 2.2.9. - [Release notes](https://github.com/cure53/DOMPurify/releases) - [Commits](cure53/DOMPurify@2.2.8...2.2.9) --- updated-dependencies: - dependency-name: dompurify dependency-type: direct:production update-type: version-update:semver-patch ... Signed-off-by: dependabot[bot] <support@github.com> * fix(ui): parameter placeholder should only display `name` (swagger-api#7123) * remove `description` from parameter placeholder * chore(deps-dev): bump jest from 26.6.3 to 27.0.4 (swagger-api#7334) Bumps [jest](https://github.com/facebook/jest) from 26.6.3 to 27.0.4. - [Release notes](https://github.com/facebook/jest/releases) - [Changelog](https://github.com/facebook/jest/blob/master/CHANGELOG.md) - [Commits](jestjs/jest@v26.6.3...v27.0.4) --- updated-dependencies: - dependency-name: jest dependency-type: direct:development update-type: version-update:semver-major ... Signed-off-by: dependabot[bot] <support@github.com> Co-authored-by: dependabot[bot] <49699333+dependabot[bot]@users.noreply.github.com> * fix(sample-gen): oas3 form-data object should generate example (swagger-api#7355) * fix(try-it-out): button and inner text spacing (swagger-api#7357) * chore(deps-dev): add sass@1.35.1, remove node-sass (swagger-api#7362) * chore: prep repo for node.js v10 EOL (swagger-api#7359) * feat(oas3): Show file upload for schema binary format (swagger-api#7325) * fix(ux): display actual content type instead of hard-coded application/octet-stream * feat(ux): show file upload when schema has "format: binary", fixes swagger-api#5636 * feat(ux): show file upload when schema has "format: base64" According to swagger-api#7325 (comment) the uploaded file should be converted to base64 automatically. * feat(ux): add cypress tests for displaying an upload button * chore(deps-dev): bump @babel/plugin-proposal-class-properties (swagger-api#7364) Bumps [@babel/plugin-proposal-class-properties](https://github.com/babel/babel/tree/HEAD/packages/babel-plugin-proposal-class-properties) from 7.13.0 to 7.14.5. - [Release notes](https://github.com/babel/babel/releases) - [Changelog](https://github.com/babel/babel/blob/main/CHANGELOG.md) - [Commits](https://github.com/babel/babel/commits/v7.14.5/packages/babel-plugin-proposal-class-properties) --- updated-dependencies: - dependency-name: "@babel/plugin-proposal-class-properties" dependency-type: direct:development update-type: version-update:semver-minor ... Signed-off-by: dependabot[bot] <support@github.com> Co-authored-by: dependabot[bot] <49699333+dependabot[bot]@users.noreply.github.com> * chore(release): cut the v3.51.0 release * chore(deps-dev): bump cypress from 6.7.1 to 7.5.0 (swagger-api#7366) * chore(deps-dev): bump eslint-plugin-mocha from 8.1.0 to 9.0.0 (swagger-api#7336) Bumps [eslint-plugin-mocha](https://github.com/lo1tuma/eslint-plugin-mocha) from 8.1.0 to 9.0.0. - [Release notes](https://github.com/lo1tuma/eslint-plugin-mocha/releases) - [Changelog](https://github.com/lo1tuma/eslint-plugin-mocha/blob/master/CHANGELOG.md) - [Commits](lo1tuma/eslint-plugin-mocha@8.1.0...9.0.0) --- updated-dependencies: - dependency-name: eslint-plugin-mocha dependency-type: direct:development update-type: version-update:semver-major ... Signed-off-by: dependabot[bot] <support@github.com> Co-authored-by: dependabot[bot] <49699333+dependabot[bot]@users.noreply.github.com> * chore(deps-dev): bump lint-staged from 10.5.4 to 11.0.0 (swagger-api#7256) Bumps [lint-staged](https://github.com/okonet/lint-staged) from 10.5.4 to 11.0.0. - [Release notes](https://github.com/okonet/lint-staged/releases) - [Commits](lint-staged/lint-staged@v10.5.4...v11.0.0) Signed-off-by: dependabot[bot] <support@github.com> Co-authored-by: dependabot[bot] <49699333+dependabot[bot]@users.noreply.github.com> * chore(deps-dev): bump release-it from 13.7.1 to 14.10.0 (swagger-api#7367) * also bump @release-it/conventional-changelog to 3.0.1 * chore(deps-dev): bump @babel/plugin-transform-runtime Bumps [@babel/plugin-transform-runtime](https://github.com/babel/babel/tree/HEAD/packages/babel-plugin-transform-runtime) from 7.14.3 to 7.14.5. - [Release notes](https://github.com/babel/babel/releases) - [Changelog](https://github.com/babel/babel/blob/main/CHANGELOG.md) - [Commits](https://github.com/babel/babel/commits/v7.14.5/packages/babel-plugin-transform-runtime) --- updated-dependencies: - dependency-name: "@babel/plugin-transform-runtime" dependency-type: direct:development update-type: version-update:semver-patch ... Signed-off-by: dependabot[bot] <support@github.com> * chore(deps): bump @babel/runtime-corejs3 from 7.14.0 to 7.14.7 Bumps [@babel/runtime-corejs3](https://github.com/babel/babel/tree/HEAD/packages/babel-runtime-corejs3) from 7.14.0 to 7.14.7. - [Release notes](https://github.com/babel/babel/releases) - [Changelog](https://github.com/babel/babel/blob/main/CHANGELOG.md) - [Commits](https://github.com/babel/babel/commits/v7.14.7/packages/babel-runtime-corejs3) --- updated-dependencies: - dependency-name: "@babel/runtime-corejs3" dependency-type: direct:production update-type: version-update:semver-patch ... Signed-off-by: dependabot[bot] <support@github.com> * chore(deps): bump @braintree/sanitize-url from 5.0.1 to 5.0.2 Bumps [@braintree/sanitize-url](https://github.com/braintree/sanitize-url) from 5.0.1 to 5.0.2. - [Release notes](https://github.com/braintree/sanitize-url/releases) - [Changelog](https://github.com/braintree/sanitize-url/blob/main/CHANGELOG.md) - [Commits](braintree/sanitize-url@v5.0.1...v5.0.2) --- updated-dependencies: - dependency-name: "@braintree/sanitize-url" dependency-type: direct:production update-type: version-update:semver-patch ... Signed-off-by: dependabot[bot] <support@github.com> * chore(deps-dev): bump @babel/plugin-proposal-optional-chaining Bumps [@babel/plugin-proposal-optional-chaining](https://github.com/babel/babel/tree/HEAD/packages/babel-plugin-proposal-optional-chaining) from 7.14.2 to 7.14.5. - [Release notes](https://github.com/babel/babel/releases) - [Changelog](https://github.com/babel/babel/blob/main/CHANGELOG.md) - [Commits](https://github.com/babel/babel/commits/v7.14.5/packages/babel-plugin-proposal-optional-chaining) --- updated-dependencies: - dependency-name: "@babel/plugin-proposal-optional-chaining" dependency-type: direct:development update-type: version-update:semver-patch ... Signed-off-by: dependabot[bot] <support@github.com> * chore(ga): cache cypress binary (swagger-api#7377) * chore(ga): cache cypress binary * chore(ga): add cypress_cache_folder * chore(ga): add cache node modules to artifact-bundle * fix(sample-gen): parameter array missing items fallback (swagger-api#7376) * fixes swagger-api#7375 * chore(deps-dev): bump @babel/preset-env from 7.14.2 to 7.14.7 Bumps [@babel/preset-env](https://github.com/babel/babel/tree/HEAD/packages/babel-preset-env) from 7.14.2 to 7.14.7. - [Release notes](https://github.com/babel/babel/releases) - [Changelog](https://github.com/babel/babel/blob/main/CHANGELOG.md) - [Commits](https://github.com/babel/babel/commits/v7.14.7/packages/babel-preset-env) --- updated-dependencies: - dependency-name: "@babel/preset-env" dependency-type: direct:development update-type: version-update:semver-patch ... Signed-off-by: dependabot[bot] <support@github.com> * chore(deps-dev): bump eslint-plugin-import from 2.23.3 to 2.23.4 Bumps [eslint-plugin-import](https://github.com/benmosher/eslint-plugin-import) from 2.23.3 to 2.23.4. - [Release notes](https://github.com/benmosher/eslint-plugin-import/releases) - [Changelog](https://github.com/benmosher/eslint-plugin-import/blob/master/CHANGELOG.md) - [Commits](import-js/eslint-plugin-import@v2.23.3...v2.23.4) --- updated-dependencies: - dependency-name: eslint-plugin-import dependency-type: direct:development update-type: version-update:semver-patch ... Signed-off-by: dependabot[bot] <support@github.com> * chore(deps-dev): bump @babel/cli from 7.14.3 to 7.14.5 Bumps [@babel/cli](https://github.com/babel/babel/tree/HEAD/packages/babel-cli) from 7.14.3 to 7.14.5. - [Release notes](https://github.com/babel/babel/releases) - [Changelog](https://github.com/babel/babel/blob/main/CHANGELOG.md) - [Commits](https://github.com/babel/babel/commits/v7.14.5/packages/babel-cli) --- updated-dependencies: - dependency-name: "@babel/cli" dependency-type: direct:development update-type: version-update:semver-patch ... Signed-off-by: dependabot[bot] <support@github.com> * chore(deps-dev): bump @babel/plugin-proposal-nullish-coalescing-operator Bumps [@babel/plugin-proposal-nullish-coalescing-operator](https://github.com/babel/babel/tree/HEAD/packages/babel-plugin-proposal-nullish-coalescing-operator) from 7.14.2 to 7.14.5. - [Release notes](https://github.com/babel/babel/releases) - [Changelog](https://github.com/babel/babel/blob/main/CHANGELOG.md) - [Commits](https://github.com/babel/babel/commits/v7.14.5/packages/babel-plugin-proposal-nullish-coalescing-operator) --- updated-dependencies: - dependency-name: "@babel/plugin-proposal-nullish-coalescing-operator" dependency-type: direct:development update-type: version-update:semver-patch ... Signed-off-by: dependabot[bot] <support@github.com> * chore(deps-dev): bump @babel/core from 7.14.2 to 7.14.6 Bumps [@babel/core](https://github.com/babel/babel/tree/HEAD/packages/babel-core) from 7.14.2 to 7.14.6. - [Release notes](https://github.com/babel/babel/releases) - [Changelog](https://github.com/babel/babel/blob/main/CHANGELOG.md) - [Commits](https://github.com/babel/babel/commits/v7.14.6/packages/babel-core) --- updated-dependencies: - dependency-name: "@babel/core" dependency-type: direct:development update-type: version-update:semver-patch ... Signed-off-by: dependabot[bot] <support@github.com> * chore(deps-dev): bump @babel/preset-react from 7.13.13 to 7.14.5 Bumps [@babel/preset-react](https://github.com/babel/babel/tree/HEAD/packages/babel-preset-react) from 7.13.13 to 7.14.5. - [Release notes](https://github.com/babel/babel/releases) - [Changelog](https://github.com/babel/babel/blob/main/CHANGELOG.md) - [Commits](https://github.com/babel/babel/commits/v7.14.5/packages/babel-preset-react) --- updated-dependencies: - dependency-name: "@babel/preset-react" dependency-type: direct:development update-type: version-update:semver-minor ... Signed-off-by: dependabot[bot] <support@github.com> * chore(deps-dev): bump @jest/globals from 26.6.2 to 27.0.6 (swagger-api#7393) Bumps [@jest/globals](https://github.com/facebook/jest/tree/HEAD/packages/jest-globals) from 26.6.2 to 27.0.6. - [Release notes](https://github.com/facebook/jest/releases) - [Changelog](https://github.com/facebook/jest/blob/master/CHANGELOG.md) - [Commits](https://github.com/facebook/jest/commits/v27.0.6/packages/jest-globals) --- updated-dependencies: - dependency-name: "@jest/globals" dependency-type: direct:development update-type: version-update:semver-major ... Signed-off-by: dependabot[bot] <support@github.com> Co-authored-by: dependabot[bot] <49699333+dependabot[bot]@users.noreply.github.com> * chore(deps-dev): bump @babel/register from 7.13.16 to 7.14.5 Bumps [@babel/register](https://github.com/babel/babel/tree/HEAD/packages/babel-register) from 7.13.16 to 7.14.5. - [Release notes](https://github.com/babel/babel/releases) - [Changelog](https://github.com/babel/babel/blob/main/CHANGELOG.md) - [Commits](https://github.com/babel/babel/commits/v7.14.5/packages/babel-register) --- updated-dependencies: - dependency-name: "@babel/register" dependency-type: direct:development update-type: version-update:semver-minor ... Signed-off-by: dependabot[bot] <support@github.com> * chore(deps-dev): bump eslint from 7.27.0 to 7.29.0 Bumps [eslint](https://github.com/eslint/eslint) from 7.27.0 to 7.29.0. - [Release notes](https://github.com/eslint/eslint/releases) - [Changelog](https://github.com/eslint/eslint/blob/master/CHANGELOG.md) - [Commits](eslint/eslint@v7.27.0...v7.29.0) --- updated-dependencies: - dependency-name: eslint dependency-type: direct:development update-type: version-update:semver-minor ... Signed-off-by: dependabot[bot] <support@github.com> * chore(deps-dev): bump nightwatch from 1.6.4 to 1.7.7 Bumps [nightwatch](https://github.com/nightwatchjs/nightwatch) from 1.6.4 to 1.7.7. - [Release notes](https://github.com/nightwatchjs/nightwatch/releases) - [Commits](nightwatchjs/nightwatch@v1.6.4...v1.7.7) --- updated-dependencies: - dependency-name: nightwatch dependency-type: direct:development update-type: version-update:semver-minor ... Signed-off-by: dependabot[bot] <support@github.com> * chore(release): cut the v3.51.1 release * chore(deps-dev): bump jest from 27.0.4 to 27.0.6 Bumps [jest](https://github.com/facebook/jest) from 27.0.4 to 27.0.6. - [Release notes](https://github.com/facebook/jest/releases) - [Changelog](https://github.com/facebook/jest/blob/master/CHANGELOG.md) - [Commits](jestjs/jest@v27.0.4...v27.0.6) --- updated-dependencies: - dependency-name: jest dependency-type: direct:development update-type: version-update:semver-patch ... Signed-off-by: dependabot[bot] <support@github.com> * chore(deps-dev): bump webpack-cli from 4.7.0 to 4.7.2 Bumps [webpack-cli](https://github.com/webpack/webpack-cli) from 4.7.0 to 4.7.2. - [Release notes](https://github.com/webpack/webpack-cli/releases) - [Changelog](https://github.com/webpack/webpack-cli/blob/master/CHANGELOG.md) - [Commits](https://github.com/webpack/webpack-cli/compare/webpack-cli@4.7.0...webpack-cli@4.7.2) --- updated-dependencies: - dependency-name: webpack-cli dependency-type: direct:development update-type: version-update:semver-patch ... Signed-off-by: dependabot[bot] <support@github.com> * chore(deps-dev): bump mini-css-extract-plugin from 1.6.0 to 1.6.2 Bumps [mini-css-extract-plugin](https://github.com/webpack-contrib/mini-css-extract-plugin) from 1.6.0 to 1.6.2. - [Release notes](https://github.com/webpack-contrib/mini-css-extract-plugin/releases) - [Changelog](https://github.com/webpack-contrib/mini-css-extract-plugin/blob/master/CHANGELOG.md) - [Commits](webpack-contrib/mini-css-extract-plugin@v1.6.0...v1.6.2) --- updated-dependencies: - dependency-name: mini-css-extract-plugin dependency-type: direct:development update-type: version-update:semver-patch ... Signed-off-by: dependabot[bot] <support@github.com> * chore(deps-dev): bump postcss from 8.2.15 to 8.3.5 Bumps [postcss](https://github.com/postcss/postcss) from 8.2.15 to 8.3.5. - [Release notes](https://github.com/postcss/postcss/releases) - [Changelog](https://github.com/postcss/postcss/blob/main/CHANGELOG.md) - [Commits](postcss/postcss@8.2.15...8.3.5) --- updated-dependencies: - dependency-name: postcss dependency-type: direct:development update-type: version-update:semver-minor ... Signed-off-by: dependabot[bot] <support@github.com> * ci(dependabot): disable dependabot until V4 RC * fix(deps): bump swagger-client to v3.14.1 (swagger-api#7440) This sets minimum Node.js version to >=12.4 and fixes problem with swagger-ui.js build fragment. Refs swagger-api#7436 * chore(release): cut the v3.51.2 release * chore(deps-dev): bump cypress from 7.5.0 to 7.7.0 Bumps [cypress](https://github.com/cypress-io/cypress) from 7.5.0 to 7.7.0. - [Release notes](https://github.com/cypress-io/cypress/releases) - [Changelog](https://github.com/cypress-io/cypress/blob/develop/.releaserc.base.js) - [Commits](cypress-io/cypress@v7.5.0...v7.7.0) --- updated-dependencies: - dependency-name: cypress dependency-type: direct:development update-type: version-update:semver-minor ... Signed-off-by: dependabot[bot] <support@github.com> * chore(package): allow swagger-client version ranges (swagger-api#7441) * ci: disable dependabot merge workflow Refs swagger-api#7341 * feat(js-yaml): update our main YAML parser to v4.1.0 Closes swagger-api#6804 * chore(deps): bump swagger-client to v3.15.0 * chore(release): cut the v3.52.0 release * chore(deps-dev): bump eslint-plugin-react from 7.23.2 to 7.24.0 Bumps [eslint-plugin-react](https://github.com/yannickcr/eslint-plugin-react) from 7.23.2 to 7.24.0. - [Release notes](https://github.com/yannickcr/eslint-plugin-react/releases) - [Changelog](https://github.com/yannickcr/eslint-plugin-react/blob/master/CHANGELOG.md) - [Commits](jsx-eslint/eslint-plugin-react@v7.23.2...v7.24.0) --- updated-dependencies: - dependency-name: eslint-plugin-react dependency-type: direct:development update-type: version-update:semver-minor ... Signed-off-by: dependabot[bot] <support@github.com> * build(docker): fix docker image Node.js security issue Refs swagger-api#7445 * ci: use max Node.js version of 16.8 Node.js version 16.9 relesed 3 days ago gives cryptic errors. We'll wait untill this is fixed upstream. * fix(security): bump swagger-client to v3.16.1 Refs swagger-api#7473 * fix(build-security): do not expose hostname to build framents (swagger-api#7491) Refs swagger-api#7446 * chore(release): cut the v3.52.1 release * chore(deps-dev): bump chromedriver from 90.0.1 to 91.0.1 Bumps [chromedriver](https://github.com/giggio/node-chromedriver) from 90.0.1 to 91.0.1. - [Release notes](https://github.com/giggio/node-chromedriver/releases) - [Commits](giggio/node-chromedriver@90.0.1...91.0.1) --- updated-dependencies: - dependency-name: chromedriver dependency-type: direct:development update-type: version-update:semver-major ... Signed-off-by: dependabot[bot] <support@github.com> * chore(deps): bump url-parse from 1.5.1 to 1.5.2 Bumps [url-parse](https://github.com/unshiftio/url-parse) from 1.5.1 to 1.5.2. - [Release notes](https://github.com/unshiftio/url-parse/releases) - [Commits](unshiftio/url-parse@1.5.1...1.5.2) --- updated-dependencies: - dependency-name: url-parse dependency-type: direct:production ... Signed-off-by: dependabot[bot] <support@github.com> * fix(security): fix security issue in prismjs dep (swagger-api#7493) Refs swagger-api#7492 * fix(Dockerfile): fix security issue in docker image Refs swagger-api#7445 * chore(release): cut the v3.52.2 release * fix(try-it-out): fix the width of image responses (swagger-api#7495) Refs swagger-api#5578 * fix(sample-gen): generate the correct number of properties (swagger-api#7432) This commit fixes correct number of additionalProperties when minProperties is used. * docs(configuration): fix wrong property name languagesMask property is not recognized by SwaggerUI. languages property is recognized propertly. Refs swagger-api#7505 * chore(security): fix security vulnerabilities in dev deps (swagger-api#7510) * fix(a11n): provide proper a11n for response example tabs (swagger-api#7464) - Update tabs to use <button> elements instead of <a> - Add aria roles for tablist, tabs, and tabpanel - Add aria attributes for additional a11y compliance and screen reader accessibility - Replace ids with data-name attribute for tabpanels - Add cypress test 7463 and update swos-63 - Move tabs test file to tests/a11y directory - Rename test file to be more descriptive of what is being tested. - Add id attributes to both tabs and tabpanels to leverage aria-controls and aria-labelledby attributes Co-authored-by: Calvin Gonzalez <calvin.gonzalez@oddball.io> Co-authored-by: Vladimir Gorej <vladimir.gorej@gmail.com> Closes swagger-api#7463 Refs swagger-api#7350 * chore(docker): automatic updates + nightly security check (swagger-api#7515) Refs swagger-api#7514 * chore(release): cut the v3.52.3 release * fix(ux): update the buttons of the example tabs to be displayed as links (swagger-api#7517) Fixes small visual regression introduced in swagger-api#7464. Refs swagger-api#7464 * chore(deps-dev): fix security vulnerabilities in dep tree * refactor: remove IE7 CSS hack (swagger-api#7526) Remove IE specific start hack: https://stackoverflow.com/a/14927670/808699 that was targeting IE 5.5 to 7. * fix(paths): break long paths with <wbr> (swagger-api#7516) - use <wbr> instead of ZERO-WIDTH SPACE (U+200B) to break segments - remove no-longer-needed onCopyCapture listener which previously stripped ZWSPs - update's deep-link.jsx's `text` prop type to accept `PropType.node` to allow the above. Closes swagger-api#7513 Co-authored-by: Vladimir Gorej <vladimir.gorej@gmail.com> * fix(UI): correct width of HTTP request method names (swagger-api#7527) Closes swagger-api#7479 * fix: fix issue with highlight code scrolling causing console error (swagger-api#7497) (swagger-api#7519) Co-authored-by: Mahtis Michel <mathis.michel@outlook.de> Refs swagger-api#7497 * refactor(highlight-code): declare properties explicitly Refs swagger-api#7497 * fix: rename request snippets configuration props (swagger-api#7535) Closes swagger-api#7534 * fix: remove redundant whitespaces in API key auth popup (swagger-api#7538) * chore(release): cut the v3.52.4 release * fix(highlight-code): handle mousewheel events properly (swagger-api#7554) SyntaxHighlighter component doesn't support ref. We had to use different approach to finds it's DOM Node using ref of the root Node of the render tree for HighlightCode component. Refs swagger-api#7497 * chore(release): cut the v3.52.5 release * fix(ui): eliminate copy button icon misaligned in Firefox (swagger-api#7542) Closes swagger-api#7481 * chore(deps): bump vm2 from 3.9.3 to 3.9.5 (swagger-api#7565) Bumps [vm2](https://github.com/patriksimek/vm2) from 3.9.3 to 3.9.5. - [Release notes](https://github.com/patriksimek/vm2/releases) - [Changelog](https://github.com/patriksimek/vm2/blob/master/CHANGELOG.md) - [Commits](patriksimek/vm2@3.9.3...3.9.5) --- updated-dependencies: - dependency-name: vm2 dependency-type: indirect ... Signed-off-by: dependabot[bot] <support@github.com> Co-authored-by: dependabot[bot] <49699333+dependabot[bot]@users.noreply.github.com> Co-authored-by: Vladimir Gorej <vladimir.gorej@gmail.com> * chore(deps): bump DOMPurify to latest version v2.3.3 (swagger-api#7572) * docs(LICENSE): apply Apache 2.0 License correctly (swagger-api#7574) Closes swagger-api#6635 * chore(deps): fix security vulnerabilities * chore(deps): update react & react-dom to v17.0.2 Refs swagger-api#7341 * test(just-test-in-node): fix npm script Before the script exited with error thrown. Enzyme was updated to v3.11.0 and custom adapter for react@17 is used. Refs swagger-api#7341 * test(test:unit-jest): fix all failing tests for this script We needed to align new cheerio and enzyme APIS with tests. Refs swagger-api#7341 * test(e2e-cypress): fix all failing tests for this script Problem was with an obsolete and no longer supported Perf tool for React. Reference to it have been removed. Refs swagger-api#7341 * chore(deps-dev): update redux-immutable to v4.0.0 Refs swagger-api#7341 * chore(deps): update redux-immutable-pure-component to 2.2.0 Refs swagger-api#7341 * chore(deps): update redux to v4.1.0 Refs swagger-api#7341 * chore(deps): update react-redux to v7.2.4 * chore(deps): update react-inspector to v5.1.1 Refs swagger-api#7341 * build(swagger-ui-react): align version of React with SwaggerUI Refs swagger-api#7341 * chore(package-lock): update lock file to reflect deps * chore(release): prepare release scripts for v4 beta pre-release * chore(package): tweak automated-release script #1 * chore(release): cut the v4.0.0-beta.0 release * chore(release-it): allow releasing consecutive beta releases Refs swagger-api#7341 * chore(deps): replace react-motion library for obj. literal Refs swagger-api#7341 * chore(deps-dev): update react-test-renderer to v17.0.2 Refs swagger-api#7341 * chore(security): fix transitive deps using npm audit Refs swagger-api#7341 * chore(package-lock): add integrity check info Refs swagger-api#7341 * chore(deps): replace @kyleshockey/* deps with originals @kyleshockey/object-assign-deep - replaced by lodash/merge. If behavior not be compatible well use lodash/mergeWith. @kyleshockey/xml - by installing stream library directly, we can use origin xml library without the fork. Refs swagger-api#7341 * chore(deps): update react-debounce-input to v3.2.4 Refs #swagger-api#7341 * test: remove support for nighwatch e2e tests We still ratain nighwatch test cases and need to port them to Cypress. Test cases were broken and did not run any more. Refs swagger-api#7341 * chore(release): cut the v4.0.0-beta.1 release * chore(package-lock): transform to lockfileVersion=2 * fix(deps): update swagger-client to v3.14.1 Refs swagger-api#7341 Refs swagger-api#7436 * chore(deps): rebase on top of master Refs swagger-api#7379 * chore(package-lock): regenerate to fix corruption Refs swagger-api#7341 * chore(deps): pickup deps changes from master Refs swagger-api#7341 * chore: bump to v4.0.0-beta.2 * chore(release): cut the v4.0.0-beta.3 release * refactor: prefix lifecycle methods with UNSAFE_ Refs swagger-api#7341 * fix(servers): compensate when server list contains a null value Refs swagger-api/swagger-editor#2761 Refs swagger-api/swagger-editor#2710 Refs swagger-api#7341 * chore(release): cut the v4.0.0-beta.4 release * fix(security): bump swagger-client to v3.16.1 Refs swagger-api#7473 * chore(release): end beta phase and start RC * chore(release): cut the v4.0.0-rc.0 release * chore(release): continue with RC pre-releases * chore(deps): bump url-parse from 1.5.1 to 1.5.3 Refs swagger-api#7492 * fix(security): fix security issue in prismjs dep Refs swagger-api#7492 * chore(deps-dev): fix all fixable security issues in dev deps Refs swagger-api#7492 * chore(release): cut the v4.0.0-rc.1 release * chore(deps): remove unused stream library Refs swagger-api#7499 Refs swagger-api#7341 * build(webpack): remove duplicates from the build Refs swagger-api#7341 * chore(release): cut the v4.0.0-rc.2 release * refactor(highlight-code): add UNSAFE prefix for lifecycle methods Refs swagger-api#7497 * fix(param-body): fix loosing focus in Try It when typing (swagger-api#7548) Originally reported as SWOS-418 Closes swagger-api#7477 * chore(release): cut the v4.0.0-rc.3 release * feat: allow using functional components with hooks * fix(highlight-code): handle mousewheel events properly SyntaxHighlighter component doesn't support ref. We had to use different approach to finds it's DOM Node using ref of the root Node of the render tree for HighlightCode component. Refs swagger-api#7497 * fix(root-inject): handle errors in functional components properly * chore(deps): update swagger-client to 3.17.0 version * chore(nvm): use recommended version of Node.js@16.8.x * chore(deps): fix all security vulnerabilities Refs swagger-api#7341 * chore(deps-dev): update husky to 7.0.2 version * chore(release): cut the v4.0.0-rc.4 release * chore(deps): bump DOMPurify to latest version v2.3.3 * chore(deps): fix security vulnerabilities * ci: enable dependabot after v4 effort * chore(release): return release scripts back to original * chore(deps-dev): bump open from 8.2.1 to 8.4.0 Bumps [open](https://github.com/sindresorhus/open) from 8.2.1 to 8.4.0. - [Release notes](https://github.com/sindresorhus/open/releases) - [Commits](sindresorhus/open@v8.2.1...v8.4.0) --- updated-dependencies: - dependency-name: open dependency-type: direct:development update-type: version-update:semver-minor ... Signed-off-by: dependabot[bot] <support@github.com> * chore(release): cut the v4.0.0 release * chore(deps): bump nginx from 1.21-alpine to 1.21.3-alpine (swagger-api#7585) Bumps nginx from 1.21-alpine to 1.21.3-alpine. --- updated-dependencies: - dependency-name: nginx dependency-type: direct:production ... Signed-off-by: dependabot[bot] <support@github.com> Co-authored-by: dependabot[bot] <49699333+dependabot[bot]@users.noreply.github.com> Co-authored-by: Vladimir Gorej <vladimir.gorej@gmail.com> * chore(deps-dev): bump babel-loader from 8.2.2 to 8.2.3 Bumps [babel-loader](https://github.com/babel/babel-loader) from 8.2.2 to 8.2.3. - [Release notes](https://github.com/babel/babel-loader/releases) - [Changelog](https://github.com/babel/babel-loader/blob/main/CHANGELOG.md) - [Commits](babel/babel-loader@v8.2.2...v8.2.3) --- updated-dependencies: - dependency-name: babel-loader dependency-type: direct:development update-type: version-update:semver-patch ... Signed-off-by: dependabot[bot] <support@github.com> * chore(deps-dev): bump @babel/register from 7.14.5 to 7.16.0 Bumps [@babel/register](https://github.com/babel/babel/tree/HEAD/packages/babel-register) from 7.14.5 to 7.16.0. - [Release notes](https://github.com/babel/babel/releases) - [Changelog](https://github.com/babel/babel/blob/main/CHANGELOG.md) - [Commits](https://github.com/babel/babel/commits/v7.16.0/packages/babel-register) --- updated-dependencies: - dependency-name: "@babel/register" dependency-type: direct:development update-type: version-update:semver-minor ... Signed-off-by: dependabot[bot] <support@github.com> * chore(dependabot): limit PRs to max 3 * chore(deps-dev): bump postcss from 8.3.5 to 8.3.11 Bumps [postcss](https://github.com/postcss/postcss) from 8.3.5 to 8.3.11. - [Release notes](https://github.com/postcss/postcss/releases) - [Changelog](https://github.com/postcss/postcss/blob/main/CHANGELOG.md) - [Commits](postcss/postcss@8.3.5...8.3.11) --- updated-dependencies: - dependency-name: postcss dependency-type: direct:development update-type: version-update:semver-patch ... Signed-off-by: dependabot[bot] <support@github.com> * chore(deps-dev): bump git-describe from 4.0.4 to 4.1.0 Bumps [git-describe](https://github.com/tvdstaaij/node-git-describe) from 4.0.4 to 4.1.0. - [Release notes](https://github.com/tvdstaaij/node-git-describe/releases) - [Changelog](https://github.com/tvdstaaij/node-git-describe/blob/master/CHANGELOG.md) - [Commits](tvdstaaij/node-git-describe@v4.0.4...v4.1.0) --- updated-dependencies: - dependency-name: git-describe dependency-type: direct:development update-type: version-update:semver-minor ... Signed-off-by: dependabot[bot] <support@github.com> * chore(deps-dev): bump css-loader from 5.2.6 to 5.2.7 Bumps [css-loader](https://github.com/webpack-contrib/css-loader) from 5.2.6 to 5.2.7. - [Release notes](https://github.com/webpack-contrib/css-loader/releases) - [Changelog](https://github.com/webpack-contrib/css-loader/blob/master/CHANGELOG.md) - [Commits](webpack-contrib/css-loader@v5.2.6...v5.2.7) --- updated-dependencies: - dependency-name: css-loader dependency-type: direct:development update-type: version-update:semver-patch ... Signed-off-by: dependabot[bot] <support@github.com> * ci(deps): sqash & merge dependabot PRs (swagger-api#7596) * chore(deps-dev): bump eslint-plugin-import from 2.23.4 to 2.25.2 (swagger-api#7605) * chore(deps-dev): bump lint-staged from 11.0.0 to 11.2.6 (swagger-api#7606) * docs(README): add v4.0.0 into compatiblity table (swagger-api#7604) * chore(deps-dev): bump expect from 1.20.2 to 27.3.1 Closes swagger-api#7607 * fix(servers): prevent UI crash when chaning Server with variables Closes swagger-api#7525 * chore(release): cut the v4.0.1 release * fix(highlight-code): fix regression code highlight behavior Refs swagger-api#7603 * chore(deps-dev): bump sinon from 12.0.0 to 12.0.1 (swagger-api#7616) * fix: add source map of css file to swagger-ui-react (swagger-api#7601) Fixes source map of css file missing in swagger-ui-react. The source map is referenced in ./dist/swagger-ui.css, but as it does not exist in the final package creates errors in our tooling. * feat(swagger-ui-react): add showExtensions option (swagger-api#7563) Closes swagger-api#5892 * fix(swagger-ui-react): add showExtension propType Refs swagger-api#5892 * docs(configuration): document requestSnippetsEnabled config option Along with that fix formatting of request snippet value. * feat(swagger-ui-react): add request snippets configuration (swagger-api#7536) Closes swagger-api#7523 * chore(deps-dev): bump @wojtekmaj/enzyme-adapter-react-17 (swagger-api#7622) * feat(swagger-ui-react): add support of filter prop (swagger-api#7547) Co-authored-by: Mahtis Michel <mathis.michel@outlook.de> Co-authored-by: Vladimir Gorej <vladimir.gorej@gmail.com> Closes swagger-api#7546 * chore(release): cut the v4.1.0 release * chore(deps): bump react-copy-to-clipboard from 5.0.3 to 5.0.4 (swagger-api#7623) * chore(deps-dev): bump @babel/plugin-proposal-class-properties (swagger-api#7621) * chore(deps-dev): bump eslint-plugin-react from 7.24.0 to 7.27.0 Bumps [eslint-plugin-react](https://github.com/yannickcr/eslint-plugin-react) from 7.24.0 to 7.27.0. - [Release notes](https://github.com/yannickcr/eslint-plugin-react/releases) - [Changelog](https://github.com/yannickcr/eslint-plugin-react/blob/master/CHANGELOG.md) - [Commits](jsx-eslint/eslint-plugin-react@v7.24.0...v7.27.0) --- updated-dependencies: - dependency-name: eslint-plugin-react dependency-type: direct:development update-type: version-update:semver-minor ... Signed-off-by: dependabot[bot] <support@github.com> * chore(deps): fix security vulneraiblity in json-merger * chore(deps): bump @babel/runtime-corejs3 from 7.14.8 to 7.16.3 (swagger-api#7636) * chore(deps): bump nginx from 1.21.3-alpine to 1.21.4-alpine Bumps nginx from 1.21.3-alpine to 1.21.4-alpine. --- updated-dependencies: - dependency-name: nginx dependency-type: direct:production update-type: version-update:semver-patch ... Signed-off-by: dependabot[bot] <support@github.com> * ci: optimize speed of CI (swagger-api#7649) Refs swagger-api#7627 * chore(deps-dev): bump json-server from 0.16.3 to 0.17.0 (swagger-api#7651) * chore(deps-dev): bump cssnano from 5.0.4 to 5.0.11 (swagger-api#7652) * chore(deps-dev): bump eslint-plugin-jest from 24.4.0 to 25.2.4 (swagger-api#7629) Bumps [eslint-plugin-jest](https://github.com/jest-community/eslint-plugin-jest) from 24.4.0 to 25.2.4. - [Release notes](https://github.com/jest-community/eslint-plugin-jest/releases) - [Changelog](https://github.com/jest-community/eslint-plugin-jest/blob/main/CHANGELOG.md) - [Commits](jest-community/eslint-plugin-jest@v24.4.0...v25.2.4) --- updated-dependencies: - dependency-name: eslint-plugin-jest dependency-type: direct:development update-type: version-update:semver-major ... Signed-off-by: dependabot[bot] <support@github.com> Co-authored-by: dependabot[bot] <49699333+dependabot[bot]@users.noreply.github.com> Co-authored-by: Vladimir Gorej <vladimir.gorej@gmail.com> * chore(deps-dev): bump @babel/plugin-proposal-nullish-coalescing-operator (swagger-api#7656) * chore(deps-dev): bump @babel/plugin-transform-runtime (swagger-api#7655) * chore(deps-dev): bump cypress from 7.7.0 to 9.0.0 Bumps [cypress](https://github.com/cypress-io/cypress) from 7.7.0 to 9.0.0. - [Release notes](https://github.com/cypress-io/cypress/releases) - [Changelog](https://github.com/cypress-io/cypress/blob/develop/.releaserc.base.js) - [Commits](cypress-io/cypress@v7.7.0...v9.0.0) --- updated-dependencies: - dependency-name: cypress dependency-type: direct:development update-type: version-update:semver-major ... Signed-off-by: dependabot[bot] <support@github.com> * chore(deps-dev): bump autoprefixer from 10.3.1 to 10.4.0 (swagger-api#7659) * chore(deps-dev): bump @babel/eslint-parser from 7.14.3 to 7.16.3 (swagger-api#7660) * chore(deps): bump redux from 4.1.0 to 4.1.2 (swagger-api#7663) * chore(deps-dev): bump @commitlint/config-conventional Bumps [@commitlint/config-conventional](https://github.com/conventional-changelog/commitlint/tree/HEAD/@commitlint/config-conventional) from 12.1.4 to 15.0.0. - [Release notes](https://github.com/conventional-changelog/commitlint/releases) - [Changelog](https://github.com/conventional-changelog/commitlint/blob/master/@commitlint/config-conventional/CHANGELOG.md) - [Commits](https://github.com/conventional-changelog/commitlint/commits/v15.0.0/@commitlint/config-conventional) --- updated-dependencies: - dependency-name: "@commitlint/config-conventional" dependency-type: direct:development update-type: version-update:semver-major ... Signed-off-by: dependabot[bot] <support@github.com> * chore(deps-dev): bump husky from 7.0.2 to 7.0.4 (swagger-api#7664) Bumps [husky](https://github.com/typicode/husky) from 7.0.2 to 7.0.4. - [Release notes](https://github.com/typicode/husky/releases) - [Commits](typicode/husky@v7.0.2...v7.0.4) --- updated-dependencies: - dependency-name: husky dependency-type: direct:development update-type: version-update:semver-patch ... Signed-off-by: dependabot[bot] <support@github.com> Co-authored-by: dependabot[bot] <49699333+dependabot[bot]@users.noreply.github.com> Co-authored-by: Vladimir Gorej <vladimir.gorej@gmail.com> * chore(deps-dev): fix security vuln. in react-syntax-highlighter * fix: introduce Error Boundaries to handle unexpected failures (swagger-api#7671) Two new components have been updated via plugin system: ErrorBoundary and Fallback. These components can be overridden by user plugins. Refs swagger-api#7647 * chore(deps): allow updating patch and minor version for highlihter * chore(release): cut the v4.1.1 release * fix: request JumpToPath components always as container Refs swagger-api/swagger-editor#2099 * chore(release): cut the v4.1.2 release * chore(deps-dev): bump @commitlint/cli from 12.1.4 to 15.0.0 (swagger-api#7678) Bumps [@commitlint/cli](https://github.com/conventional-changelog/commitlint/tree/HEAD/@commitlint/cli) from 12.1.4 to 15.0.0. - [Release notes](https://github.com/conventional-changelog/commitlint/releases) - [Changelog](https://github.com/conventional-changelog/commitlint/blob/master/@commitlint/cli/CHANGELOG.md) - [Commits](https://github.com/conventional-changelog/commitlint/commits/v15.0.0/@commitlint/cli) --- updated-dependencies: - dependency-name: "@commitlint/cli" dependency-type: direct:development update-type: version-update:semver-major ... Signed-off-by: dependabot[bot] <support@github.com> Co-authored-by: dependabot[bot] <49699333+dependabot[bot]@users.noreply.github.com> Co-authored-by: Vladimir Gorej <vladimir.gorej@gmail.com> * chore(deps-dev): bump source-map-support from 0.5.19 to 0.5.21 (swagger-api#7681) * chore(deps-dev): bump @babel/plugin-proposal-optional-chaining (swagger-api#7682) * chore(deps-dev): bump eslint-plugin-import from 2.25.2 to 2.25.3 (swagger-api#7683) * chore(deps-dev): bump less from 4.1.1 to 4.1.2 (swagger-api#7685) * fix(security): disable reading config params from URL search params (swagger-api#7697) Reading configuration parameters from URL search params is by default no longer enabled. To re-enable it, set queryConfigEnabled configuration parameter to true. Functionally, this is a breaking change, but given we're just providing a security vulnerability patch we're considering this a PATCH version bump only. Refs swagger-api#4872 Refs GHSA-qrmm-w75w-3wpx * chore(release): cut the v4.1.3 release * R11DT-2620 - Update url-parse to 1.5.10 (#167) * update url-parse to 1.5.10 * update dist folder: npm run build result * Upgrade dompurify to 3.1.3 (#170) --------- Signed-off-by: dependabot[bot] <support@github.com> Co-authored-by: swagger-bot <swagger-bot@smartbear.com> Co-authored-by: dependabot[bot] <49699333+dependabot[bot]@users.noreply.github.com> Co-authored-by: Vasilev Pyotr <vahpetr@gmail.com> Co-authored-by: Tim Lai <timothy.lai@gmail.com> Co-authored-by: Andreas Grub <grub@posteo.de> Co-authored-by: Vladimir Gorej <vladimir.gorej@gmail.com> Co-authored-by: Helen Kosova <hkosova@users.noreply.github.com> Co-authored-by: Calvin Gonzalez <asuma76@gmail.com> Co-authored-by: Dominik Henneke <dominik.henneke@sda-se.com> Co-authored-by: silverwind <me@silverwind.io> Co-authored-by: Mingwei Samuel <mingwei.samuel@gmail.com> Co-authored-by: twjasa <twjasa@gmail.com> Co-authored-by: kristina-kovacikova <47686623+kristina-kovacikova@users.noreply.github.com> Co-authored-by: Mahtis Michel <mathis.michel@outlook.de> Co-authored-by: Sviataslau Hankovich <svyatoslav.hankovich@gmail.com> Co-authored-by: GhBogdan97 <36417662+GhBogdan97@users.noreply.github.com> Co-authored-by: Costas Kotsokalis <55377146+cksnp@users.noreply.github.com> Co-authored-by: Florian Dreier <dreier.florian@gmail.com> Co-authored-by: glebbash <glebbash@gmail.com> Co-authored-by: Andriy Semenyuk <andrewcem7@gmail.com> Co-authored-by: João Almeida Santos <joao.almeida.santos@outsystems.com> Co-authored-by: OS-alexandretome <alexandre.tome@outsystems.com>





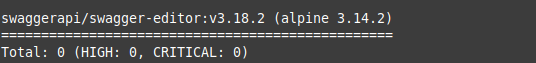
Q&A (please complete the following information)
swaggerapi/swagger-ui:latest,swaggerapi/swagger-ui:v3.51.2,swaggerapi/swagger-ui:v4.0.0-beta.2Content & configuration
Describe the bug you're encountering
The security vulnerability about nodejs has been reported in:
Alpine and nodejs has released a bug fix at 2021-07-29 with version
14.17.4-r0:To reproduce...
Steps to reproduce the behavior: Run Trivy scan as below:
You will see the result like this:
Expected behavior
Trivy security scan should not print out any HIGH or CRITICAL vulnerabilities.
The text was updated successfully, but these errors were encountered: