Want to try it for yourself?
Establishing Application Security Policies that Power Secure Development Processes
What is an application security policy?
An application security policy establishes acceptable security and protection boundaries within which application developers and security teams can operate as they develop new software, often leveraging application security solutions with policy features. When the software security policy automatically and consistently sets boundaries before work begins, it delivers critical information for efficient application development processes.
No one application security policy will fit every organization. AppSec policies must fit your organization's size and business model. As a result, there’s a need to develop effective policies that follow established application security best practices, while setting suitable levels for vulnerability protection and determining which third-party applications and open source components to use. In addition to organizational preferences, you must closely follow standards like the OWASP Top 10.
Even taking all of that into consideration, it can be difficult to establish AppSec policies that effectively balance protection with performance. The information provided here will help you establish enterprise security policies that reduce vulnerabilities and enable developers to continue releasing innovative software.
Why is Application Security Policy Important?
Software development has changed. Rapid deployment has become standard, and many DevOps teams rely heavily on open source code to support their projects. This new deployment environment has largely grown from the implementation of CI/CD processes within companies, and enterprises in particular.
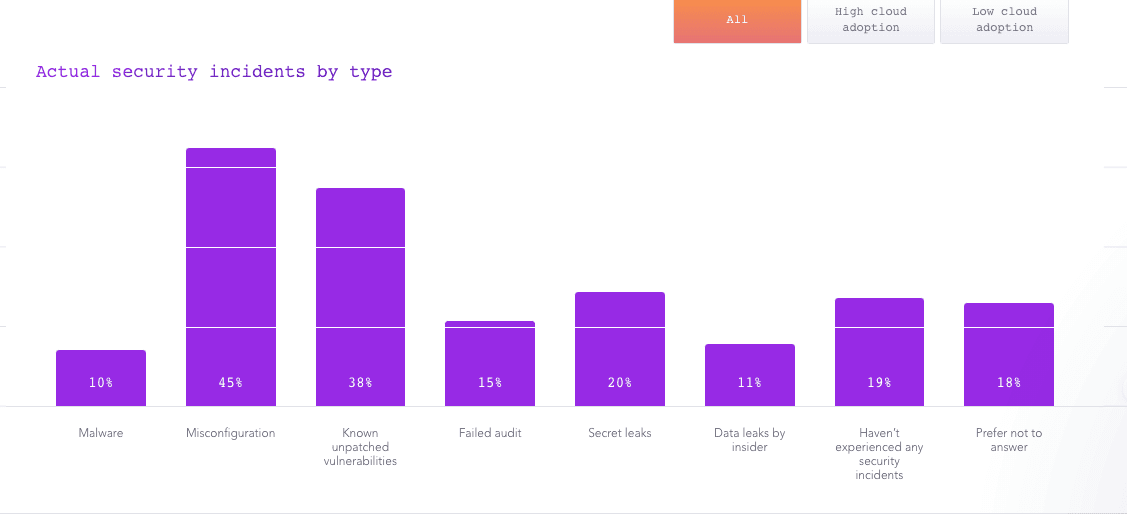
Within this fast-paced, enterprise environment, vulnerabilities can originate from something as simple as a configuration error. Snyk's State of Cloud Native Application Security Report revealed the top two causes for security incidents were misconfiguration (45%) and known unpatched vulnerabilities (38%)
One recent study revealed that out of 85,000 applications that were analyzed, 83% contained at least one security flaw. Of these, 20% had a severe vulnerability. While not all of these vulnerabilities present a major security risk, hackers continue to refine their attacks by using ingenious workarounds to penetrate software.
Application security policies establish boundaries that help prevent vulnerabilities.
The Cost of Vulnerabilities
In 2017, Equifax had been using an outdated version of the Java Apache Struts library, which opened their system to infiltration. This infamous hack exposed the personal information of 143 million users and led to a class-action lawsuit that Equifax settled for $380.5 million.
While Equifax presents an extreme example of vulnerability exploitation, any security breach has unfavorable business implications. Many companies never recover from devastating security incidents. This is why application security policies are critical, particularly for companies working with highly sensitive data (e.g. financial institutions, government organizations, healthcare companies, etc.).
By creating application security policies, businesses begin to establish an AppSec program that defines how developers can proactively address vulnerabilities within every phase of the software development lifecycle (SDLC). However, without careful consideration and process integration, application security policies can lead to frustration.
Establishing “Compliance as Code” within Your AppSec Policy
Businesses establish DevOps practices to accelerate development time and business agility. AppSec programs should strive to support these goals by crafting application security policies that balance protection with performance to ensure development continues at pace.
Ineffective application security policies cause developers to waste valuable time rewriting code and overwhelm security teams with alerts, notifications, and remediation tickets. These security policies ultimately slow development and expose businesses to greater risks. On the other hand, effective application security programs can be implemented without disrupting the DevOps workflow and empowering developers. These effective frameworks integrate policies that are coded into the software development lifecycle (SDLC), supporting continuous development.
What is compliance as code?
Compliance as code (or Policy as Code) automates the security process with effective tools that are built into DevOps, minimizing the potential for human error by removing manual, time-consuming steps. These automated security tools, governed by the application security policy, are built into the development process.
During the build process, for example, developers can use automated scanning tools that identify known vulnerabilities, and remediate them before deployment. Once deployed, automated monitoring tools can notify AppSec teams of any new risks identified in production. To support a compliance-as-code approach, application security policies should define the tools for inclusion and the types of vulnerabilities and risks that must be remediated.
Compliance as code, or test-driven compliance, policies are used by large, software-driven enterprises, such as Google, to support a more natural build process and ensure innovation continues within secure businesses. These processes ensure:
Standard reporting and transparency
Explanations of failure
Control test independence
Easy integration with CI/CD processes
Get started in capture the flag
Learn how to solve capture the flag challenges by watching our virtual 101 workshop on demand.
7 Elements of Effective Application Security Policies
While no one policy can suit every business, it’s critical for AppSec policies to clearly define what tools, controls and systems are required within security. In this way, security spans technology and processes, tying both together seamlessly.
Businesses should also address the following elements to establish effective application security policies.
Threat history - Determine which threats and vulnerabilities have led to the greatest consequences in your technology stack. This establishes a baseline for inclusion.
Vulnerability prioritization - The policy should offer a standard on what constitutes high, medium, and low risks. This helps you determine which vulnerabilities must be addressed and which to flag for consideration.
Remediation and mitigation - This is closely tied to vulnerability prioritization, but gets more specific. Who determines what must be remediated? When should a vulnerability be fixed in the development process? Are there acceptable risks?
Processes - Application security policies should define the process by which security is applied to application code. For example, will your business apply SAST and DAST?
Roles and responsibilities- The policy should define who is responsible for ensuring application security and at which stages in the SDLC.
Tool-specific - Most businesses employ security automation tools; the policy should define which tools will be used at which point in the SDLC.
Monitoring - Application vulnerabilities are often discovered and exploited after code has been pushed into production. An effective policy defines how deployed applications will be monitored and uses the priorities defined above to determine corrective actions.
Effective Policies Mean Effective Development
A clear application security policy establishes a framework that empowers both AppSec and developers with the tools and boundaries they need to assure confidence in their software and processes. Strong application security is not an afterthought or a bolted-on tool. Instead, it’s a well-developed process that supports the speed of your organization and instills confidence in your customers. Application security policies define how your organization develops effective code.
Learn more:
Complete Guide to Application Security 2023
Enabling Application Security Management at Scale
Up Next
Enable Visibility for SecOps While Reducing Build and Runtime Application Security Risks
In this session, you will see a demo and learn how to reduce security risks and improve visibility across your containerized web applications.
Keep reading



















