Want to try it for yourself?
SAST vs. SCA testing: What’s the difference? Can they be combined?
No matter how well developers follow the latest secure coding guidelines or how perfect their intentions are, some production code will almost always include at least one security issue. Developers are only human, and when faced with trying to balance the large and growing list of potential software vulnerabilities and the mounting pressures for faster release cycles, especially in more complex enterprise-level organizations, something has to give.
Let’s take a closer look at Static Application Security Testing (SAST) and Software Composition Analysis (SCA), the basic ideas behind these approaches, their advantages, and the differences between them. We’ll also cover how to leverage SAST and SCA and combine the two to release secure software and produce truly secure applications.
What is SAST and SCA?
Static Application Security Testing (SAST) is a structural testing methodology that evaluates a range of static inputs, such as documentation (requirements, design, and specifications) and application source code to test for a range of known security vulnerabilities. In the simplest terms, SAST is used to scan the code you write for security vulnerabilities.
On the other hand, Software Composition Analysis (SCA) is an application security methodology in which development teams can quickly track and analyze any open source component brought into a project. Simply put, SCA is used to scan your dependencies for security vulnerabilities.
Why is SAST important?
While SAST offers many benefits, the most significant is its ability to detect security vulnerabilities and mark their precise location, including the file name and line number. For each detected vulnerability, the SAST tool will indicate its severity and offer a brief description. This ability to pinpoint problems is crucial, as finding problems is one of the most time-consuming aspects of a developer’s work. Click here to learn the technique for analyzing code throughout the SDLC
How to Perform an Application Security Gap Analysis
In this guide we'll walk through the steps to run a Application Security Gap Analysis for asset visibility, AppSec coverage and prioritization.
Why is SCA testing important?
Increasingly, modern applications are composed of open source code. It has been estimated that open source code makes up 80 to 90 percent of the code composition of applications. And this wide availability of trusted open source code has allowed development teams to build applications faster than ever.
Of course, applications are not only composed of native organization code. In fact, one of the challenges facing organizations trying to secure their code base is the fact that applications are assembled from different building blocks that all need to be secured to be able to effectively manage and mitigate risk.
What you need to know about SAST & SCA tools
Download this guide to learn about the critical aspects of a well-rounded AppSec program that security professionals should consider when choosing static application security testing (SAST) and software composition analysis (SCA) tools.
SAST vs. SCA
Now that we’ve explored the benefits of SAST and SCA, let’s look at the differences in how each technology works to help determine which approach might be right for your organization.
SAST differences
As noted above, the greatest advantage of SAST is that as a static approach, there is no need for a running application (only lines of code), and you can start using it in the earliest development stages. Here is how SAST typically works best:
Analyzes the application from the “inside out”
Can run during all phases of the SDLC
Usually requires to create a build model that the tool understands
The analysis is based on a series of rules
There are multiple analysis types, each focusing on specific types of findings
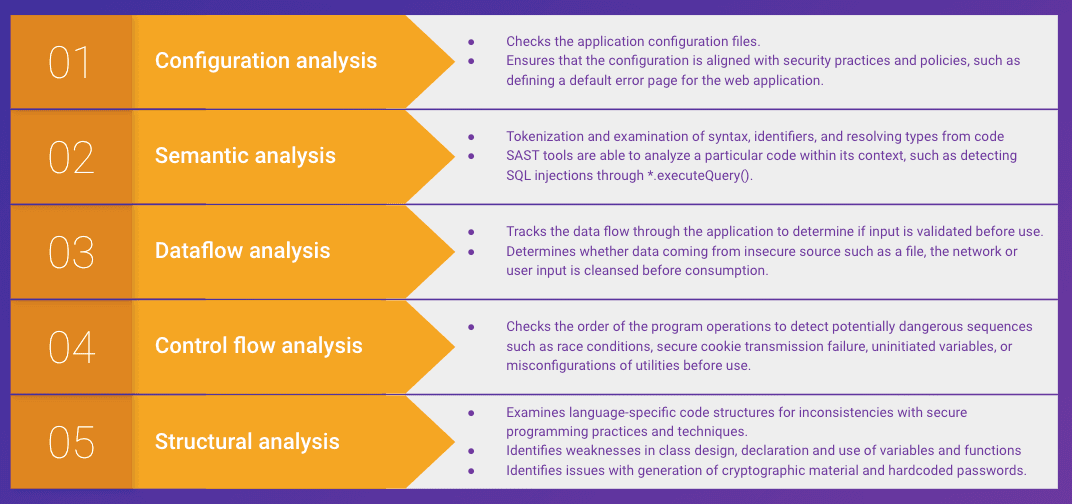
SCA differences
As referenced above, organizations deploying SCA methodologies and tools rely on open source software. Here’s where they typically work best:
Identifying open source components: Analyze applications and identify their reliance on open source packages, either via direct dependencies or transitive dependencies. According to Snyk research, 80% of vulnerabilities are introduced via transitive dependencies, so this function is crucial to effectively mitigating risk.
License compliance management: Identify the different open source licenses being used, which helps organizations mitigate the legal risk associated with open source software. Organizations can use SCA tools to establish license policies to avoid legal risk in the early stages of development.
Security vulnerabilities: Correlate with vulnerability databases and point to security vulnerabilities in open source dependencies. Once identified, some SCA tools will also provide information to facilitate remediation. Snyk, for example, provides full contextual remediation advice as well as precision security patches to help teams fix vulnerabilities in a timely manner.
Governance and control: Automatically enforce security and license policies across the different stages of the software development lifecycle. SCA tools commonly support integrating open source security testing to CI/CD processes to ensure vulnerabilities do not make their way further down the delivery pipeline.
Reporting and analysis: Produce software bill of materials (SBOMs) — detailed lists of the various dependencies used in the code and where in the code they are being used. These reports can then be used to assess exposure to future security risk and shared with other stakeholders and support standardization.
What is SCA in application security?
SCA in itself is not new, but the growing adoption of open source over the past few years has made it a key pillar of application security. As a result, SCA tools have proliferated. But not all SCA solutions are born equal. Modern software development practices, including the notion of DevSecOps, require that an SCA be developer-first — providing teams with developer-friendly tooling and security teams with the ability to guide developers. Beyond that, another differentiator could be compliance auditing functionality or AI and ML capabilities.
SAST and SCA: A combined approach to application security
When looking at these two technologies side-by-side, it becomes clear that both are needed for an effective secure development approach. SAST is most useful for the code you write, while SCA is effective for analyzing the open source software your organization leverages, along with its dependencies. Both technologies enable organizations to address security issues early and often in the development lifecycle.
A combined approach will enable you to find a wider range of vulnerabilities and exploitable weaknesses and allow you to reap the benefits of both SAST’s and SCA’s dynamic approach to security testing. It will also help in getting the complete coverage of both native and open source code.
To learn how to perform static code analysis successfully using static code analysis tools, click here.
Empower developers to build secure applications
Snyk enables developers to build securely from the start, while giving security teams complete visibility and comprehensive controls.
Up Next
SAST vs. DAST: what is the difference and how to combine the two?
Dynamic security testing (DAST) uses the opposite approach of SAST. Whereas SAST tools rely on white-box testing, DAST uses a black-box approach.
Keep reading



















