Introducing Snyk for Serverless
April 26, 2017
0 mins readToday we’re excited to announce Snyk’s new solution for securing your serverless functions, designed to easily integrate and protect serverless-based applications! The initial launch features tight integration with both AWS Lambda and Heroku. We’re also working closely with Google, Red Hat and others to integrate directly with their platforms in the coming months.
Why Is Securing Serverless Different?
Serverless (FaaS) and PaaS approaches provide a big boost for developer productivity. By moving the infrastructure concerns to teams of dedicated experts, developers are free to spend more time working on code that directly contributes to their core product. This, in turn, pushes many of the security concerns in such infrastructure to the platform, dramatically mitigating risks such as unpatched servers, compromised servers and more.
However, by crippling these attack vectors, Serverless draws attackers to the next easiest way in—vulnerable application dependencies. These open source packages, pulled from repositories such as npm, Maven, PyPI and others, are just as prevalent and just as vulnerable as the binaries we often patch. FaaS and PaaS platforms manage and secure the server dependencies, but do not manage nor secure vulnerable packages pulled in by your app.
Snyk helps address this gap, continuously monitoring your dependencies hidden inside your functions and apps for vulnerabilities (and soon license issues!).
If you're interested in Serverless practices and tools be sure to check out the following 10 Serverless security best practices cheat sheet.
Securing your serverless applications
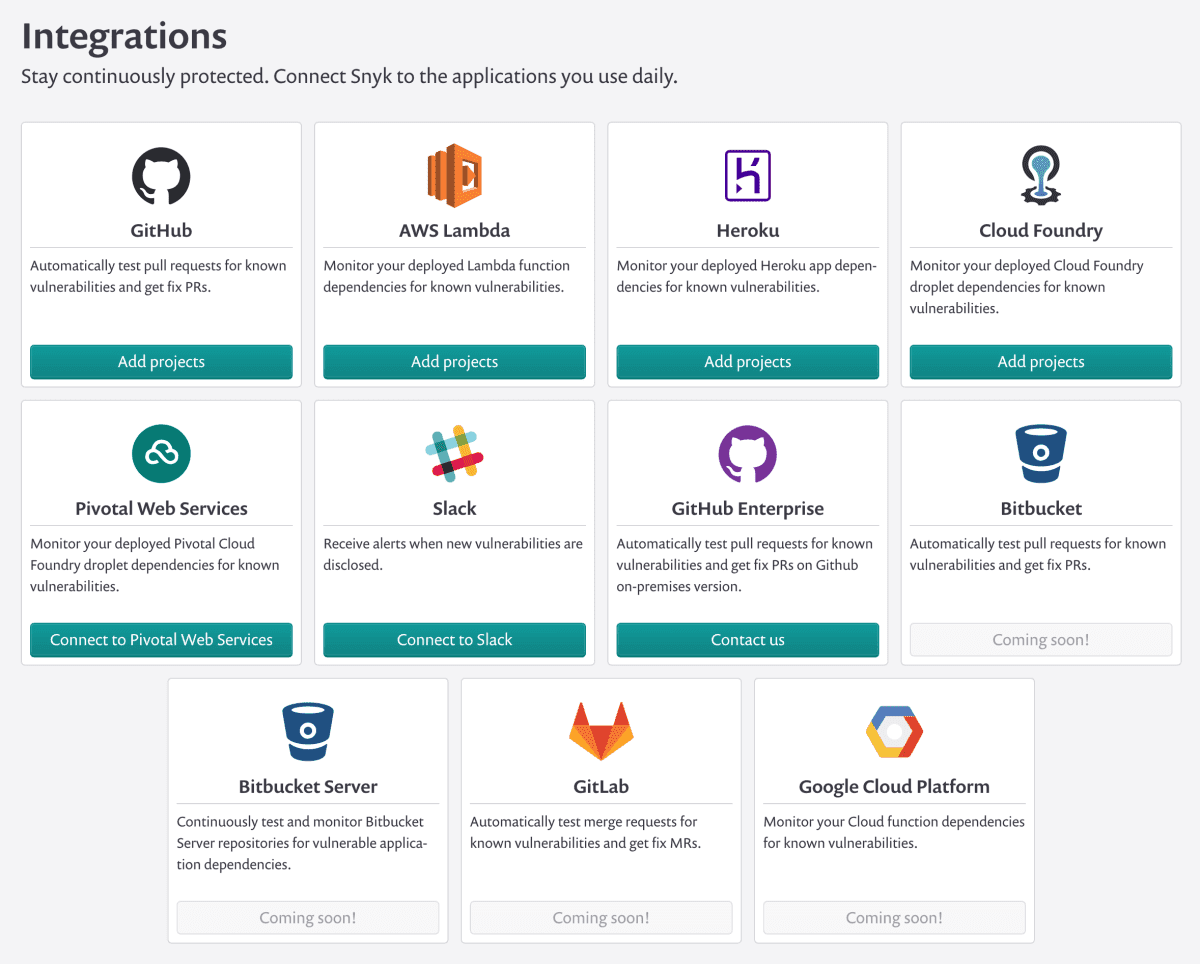
The new serverless support lets you monitor the code you’ve deployed to AWS Lambda or Heroku for any known vulnerable dependencies—with more platforms coming very soon. For each platform your code is deployed to, after entering the relevant API keys, you can choose the functions and applications to monitor continuously.
Snyk will then communicate directly with the platform, using its API, to determine what dependencies are currently deployed for each function or app, and then scan them against our vulnerabilities database for known vulnerabilities. You’ll be given a detailed report of all vulnerabilities as well as guidance on how to remediate them.
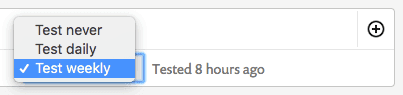
You’ll also be able to tell Snyk how frequently you would like to test each function for newly disclosed vulnerabilities that impact it. If one is found, you will be notified (via email and Slack) and can take action immediately.
Isn’t monitoring source code enough?
Quite clearly, deployed code was previously source code, and so addressing vulnerable dependencies as part of your development process is an excellent way to reduce the likelihood of deploying a vulnerability in the first place. In addition, finding issues during dev makes fixing those issues far easier.
However, securing source code isn’t enough. The path from source code to deployed code isn’t always straight, making it hard to know which functions or apps are affected by a source code vulnerability. Also, deployed code always lags behind source, and often still uses old (and potentially vulnerable) dependencies long after the code being developed has updated or patched them.
Tracking vulnerabilities in deployed code is the best way to understand and manage your risk. Addressing these vulnerabilities in your development process lets you quickly fix such issues, as well as prevent them in the first place. You can now use Snyk to secure your code throughout that lifecycle, and we encourage you to do so.
More serverless platforms to come
Serverless is a big boost for developer productivity, but your approach to security must adapt to accommodate it. Now with Snyk’s support for serverless applications, it’s that much easier to stay secure. Secure your Lambda and Heroku apps today!
We’re thrilled to launch with support for both AWS Lambda and Heroku, but there is much more to come. As we mentioned earlier, we’re working very closely with Google, Red Hat and others to directly integrate with their platforms in the coming months. We want to let you monitor your deployed code wherever it may be, continuously and easily.
If you use a platform that you don’t see in the initial launch, let us know, and we will keep you up to date on our plans for it and, if you would like, include you on relevant beta programs.
Developer loved. Security trusted.
Snyk's dev-first tooling provides integrated and automated security that meets your governance and compliance needs.





















