How to fix Java security issues while coding in IntelliJ IDEA
April 8, 2021
0 mins readNowadays, developers are responsible for more than just creating the application. Besides working on features, developers have to focus on their applications’ maintainability, scalability, reliability, and security. Many developers are unsure of where to start with security. In addition, most companies still work with a dedicated security team instead of having security expertise inside the team.
A lot of developers practically live in their integrated development environment (IDE). A good IDE is like a swiss army knife; it is your go-to tool to do almost everything. Having everything I need to build, run, test, debug, and secure my application, makes a good IDE invaluable for many developers.
From last year’s Snyk Java Ecosystem report, we know that IntelliJ IDEA is the most favorite and commonly used IDE in the Java security landscape, for which Snyk has recently released a new IntelliJ IDE vulnerability scanner plugin. Let’s see how we can integrate security and secure development into this IDE using this new plugin.
But first, here's a quick run through of what we'll cover in the post:
I'd recommend you go fullscreen so you can see the code examples.
Snyk Vulnerability Scanner for IntelliJ IDEA
Wasn’t there already a Snyk IDE plugin for IntelliJ IDEA?
Yes, there was. But the old plugin entirely focused on Snyk Open Source scanning, and helped find and fix vulnerabilities in open source dependencies. However, the new plugin also integrates newly released Snyk Code capabilities, helping developers on multiple levels.
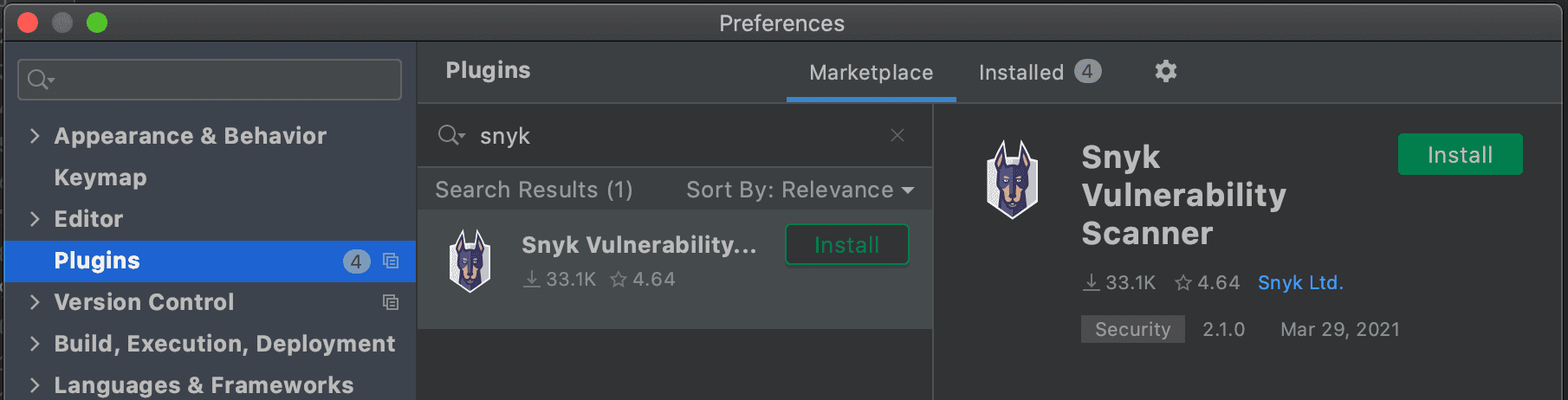
Installing the Snyk IDE plugin
The recommended way to install the plugin is via the IntelliJ IDEA marketplace. If you are simply searching for “snyk” on the plugin marketplace inside IntelliJ IDEA, you will find it right away.
After installing the plugin and restarting the IDE, you have to authenticate the plugin. To use the plugin, you need to have at least a free Snyk account. If you already have a Snyk account, you only need to sign in. If you are new to Snyk, the onboarding process will guide you through the signup process of a free account.
Snyk Code integration in IntelliJ IDEA
As mentioned above, the previous version of the Snyk plugin for IntelliJ IDEA was only leveraging our Snyk Open Source capabilities. It enabled you to scan your projects for security vulnerabilities in your open source dependencies. You can also use our Snyk Code capabilities next to the existing Snyk Open Source scanning in the new plugin. Snyk Code is a security product that statically analyzes your code for possible vulnerable code construction you or your team created. This means that with a single plugin, you can secure your complete application. Let’s take it for a spin.
Fixing security vulnerabilities in IntelliJ
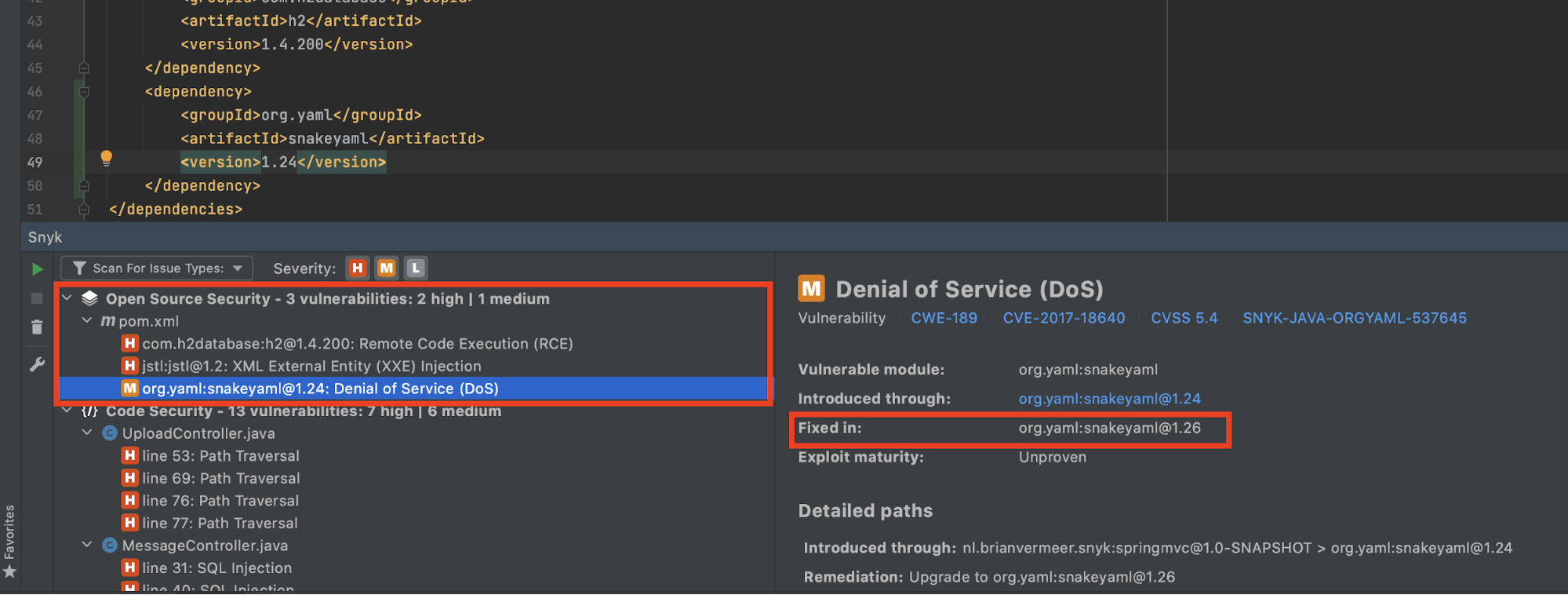
After scanning my application, I see multiple sections on my screen. The first section is the well known Snyk Open Source scanning. This part tells me that I include libraries, either direct or transitive, that contain known vulnerabilities. One of these vulnerable libraries is snakeyaml version 1.24. This version is vulnerable to a Denial of Service attack. I explained the dynamics of this attack and how you can prevent it in the blog post Preventing YAML parsing vulnerabilities with snakeyaml in Java.
The solution is super simple. If I upgrade to at least version 1.26, then the vulnerability is fixed. Note that the version with the fix is not by default the latest version. It is the closest version that does not contain the vulnerability. After updating the version in my pom file and rescanning the application, the vulnerability is gone. The actionable vulnerability remediation advice provided by the Snyk IntelliJ IDE plugin is an excellent pointer on how to fix the problem.
Scanning code for security vulnerabilities
The next section includes information about code vulnerabilities the Snyk plugin found. The Snyk Code capabilities point out flaws in my code that can cause specific security vulnerabilities.
The first issue is a “Path Traversal” problem. The Snyk plugin for IntelliJ IDEA shows me where the problem exists and the current data flow. Currently, I am writing a file to disk without checking the actual filename. If the filename contains something like “../../../textfile.txt”, my code will not save the file in the right place. This filename traverses back and breaks out of my destination folder. This means that this file ends up somewhere on my system where I don’t want it to be. More importantly, it can override existing files outside of the destination folder anywhere on the system, depending on the process’s privileges.
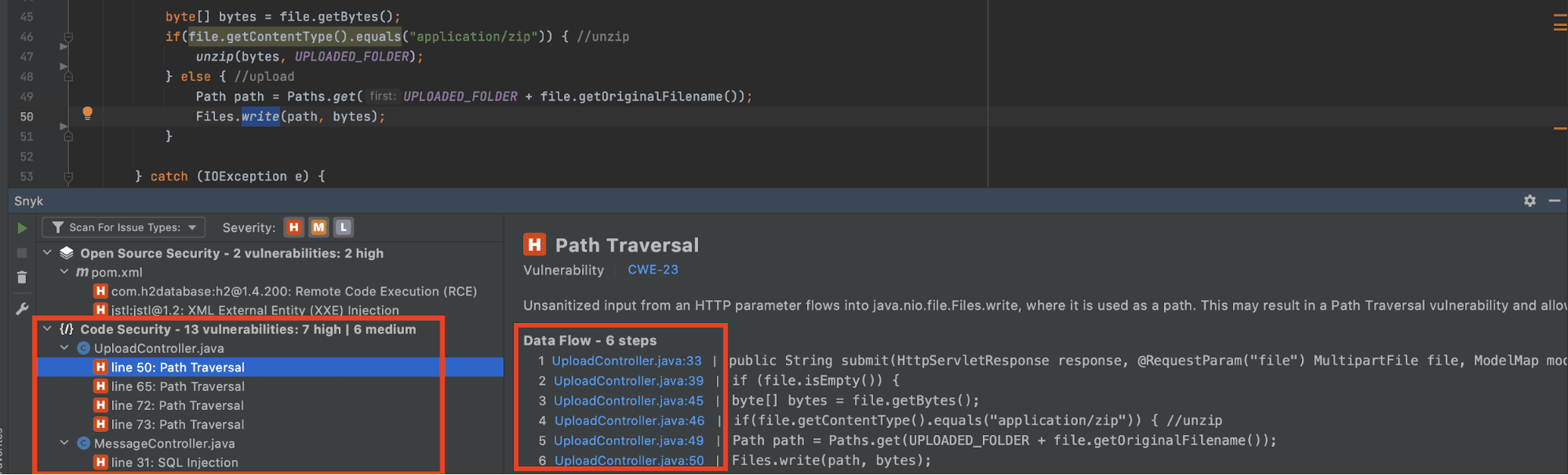
To get rid of this, I can check if the canonical path of the new file starts with the path of my intended target like below.
Path path = Paths.get(UPLOADED_FOLDER + file.getOriginalFilename());
String target = new File(UPLOADED_FOLDER).getCanonicalPath();
if (path.toFile().getCanonicalPath().startsWith(target)) {
Files.write(path, bytes);
}Now path traversal will not work anymore because the file will not be saved outside of my destination folder. After rescanning my application, I see that Snyk Code agrees with me.
Let us look at another example. According to the code inspection, I created a SQL injection vulnerability in my MessageController.java at line 33. When I look at the data flow, I see that the actual SQL injection is in MessageRepo.java. It is incredibly helpful that Snyk Code can analyze between multiple files to find this interfile issue, as not a lot of tools have that capability. Because of the MessageController the SQL injection is available to the outside world and an immediate threat I have to fix.
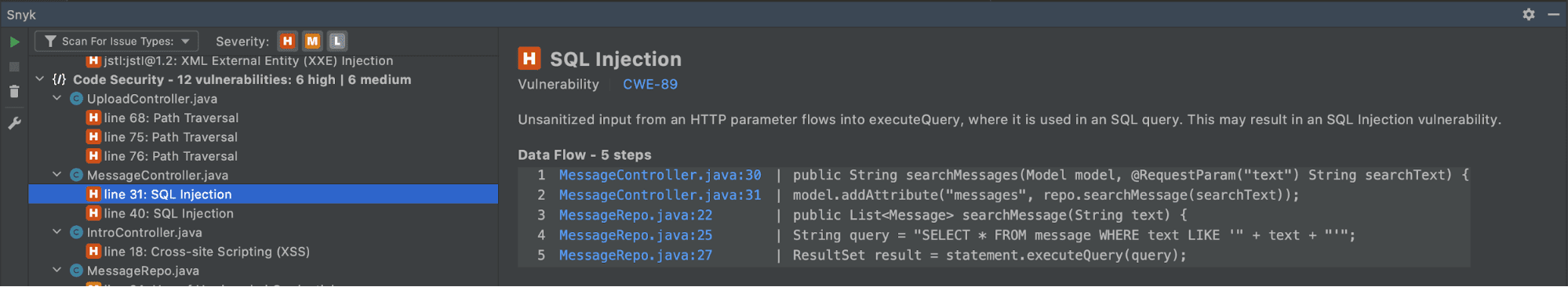
Now that I know about the issue, I will fix the code in MessageRepo.java. I will no longer concatenate the parameter directly to the query string, but use a prepared statement with query parameters. If I implement the prepared statement like below and rescan my application, the vulnerability will no longer be reported by our plugin.
String query = "SELECT * FROM message WHERE text LIKE ?";
PreparedStatement statement = connection.prepareStatement(query);
statement.setString(1, text);
ResultSet result = statement.executeQuery();
If you want to know more about SQL injection prevention, please also take a look at our handy SQL injection prevention cheat sheet.
Code Quality
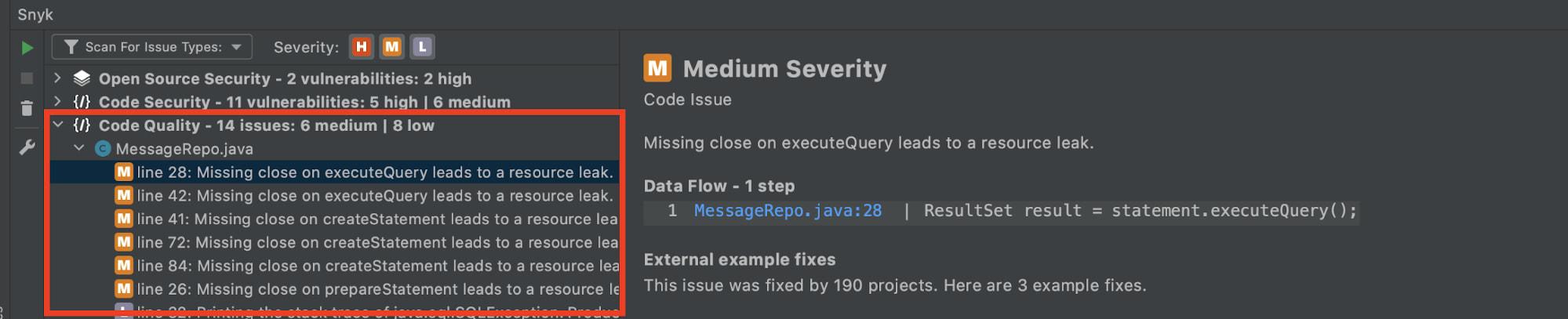
In addition to scanning for security vulnerabilities in your open source dependencies and in your own code, the Snyk plugin for IntelliJ IDEA can also help you with improving your code quality.
In the example below, the Snyk plugin points out that I am not closing certain connections. This can lead to resource leaks and should be avoided by closing the resources in a finally block.
Integrate security into IntelliJ IDEA today
The current Snyk Vulnerability Scanner for IntelliJ IDEA is basically a one-stop shop for the Java developer. Combining the power of Snyk Open Source scanning with Snyk Code scanning gives you a new powerful tool to prevent security mistakes in your application. The code quality part is also an excellent addition to the team. Note that you can configure the plugin to your preferences if you, for instance, do not want the code quality part to execute.
Nevertheless, Java developers like you and me must take responsibility for the application we create. This includes preventing security issues. With the Snyk plugin for IntelliJ IDEA, you can do this comfortably with your favorite IDE. Why don’t you give it spin?
Live Hack: Exploiting AI-Generated Code
Gain insights into best practices for utilizing generative AI coding tools securely in our upcoming live hacking session.